Policy-Based Forwarding (PBF)
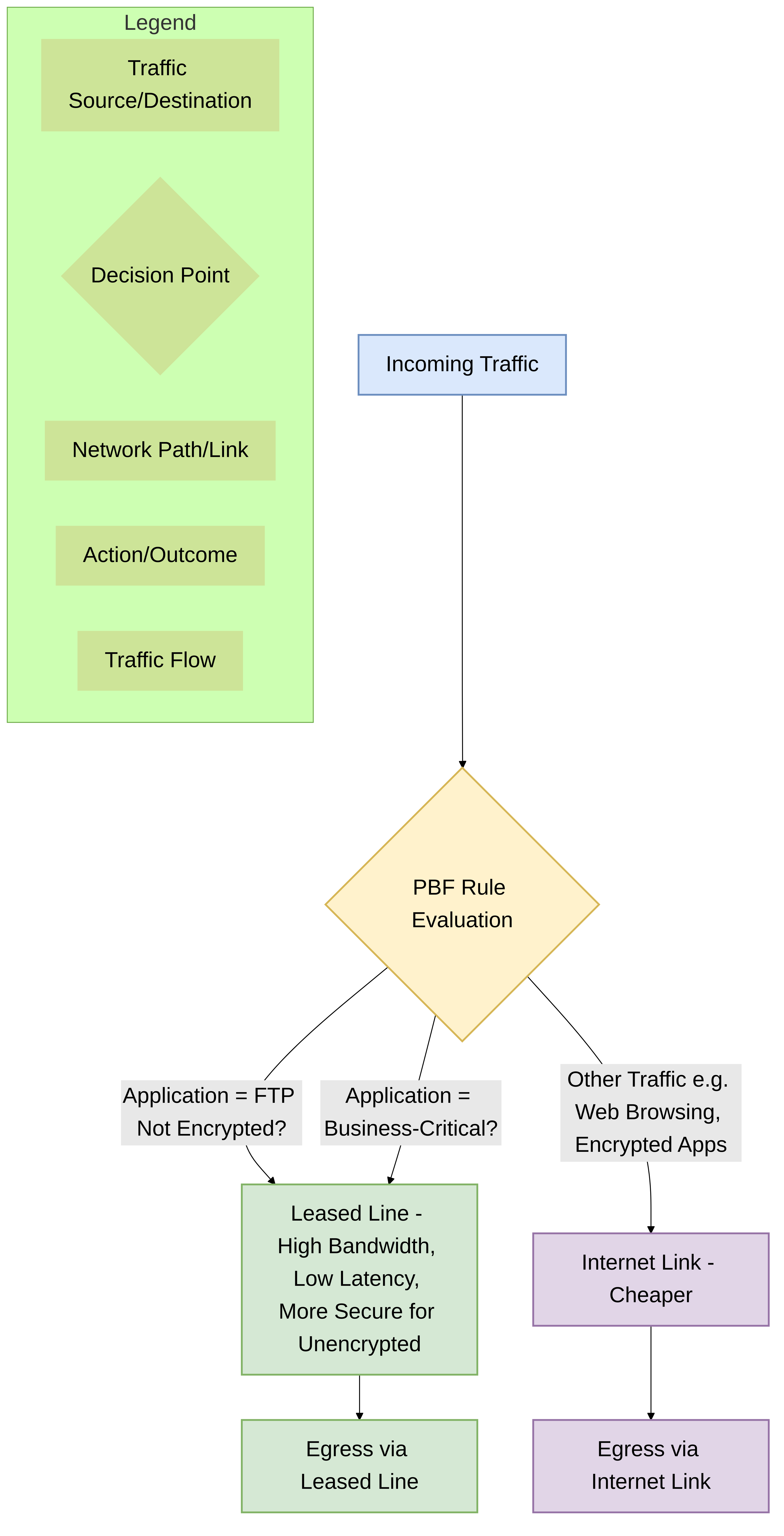
Normally, the firewall uses the destination IP address in a packet to determine the outgoing interface. The firewall uses the routing table associated with the virtual router to which the interface is connected to perform the route lookup. Policy-Based Forwarding (PBF) allows you to override the routing table, and specify the outgoing or egress interface based on specific parameters such as source or destination IP address, or type of traffic.
PBF rules allow traffic to take an alternative path from the next hop specified in the route table, and are typically used to specify an egress interface for security or performance reasons. Let's say your company has two links between the corporate office and the branch office: a cheaper internet link and a more expensive leased line. The leased line is a high-bandwidth, low-latency link. For enhanced security, you can use PBF to send applications that aren’t encrypted traffic, such as FTP traffic, over the private leased line and all other traffic over the internet link. Or, for performance, you can choose to route business-critical applications over the leased line while sending all other traffic, such as web browsing, over the cheaper link.
Egress Path and Symmetric Return
Using PBF, you can direct traffic to a specific interface on the firewall, drop the traffic, or direct traffic to another virtual system (on systems enabled for multiple virtual systems).
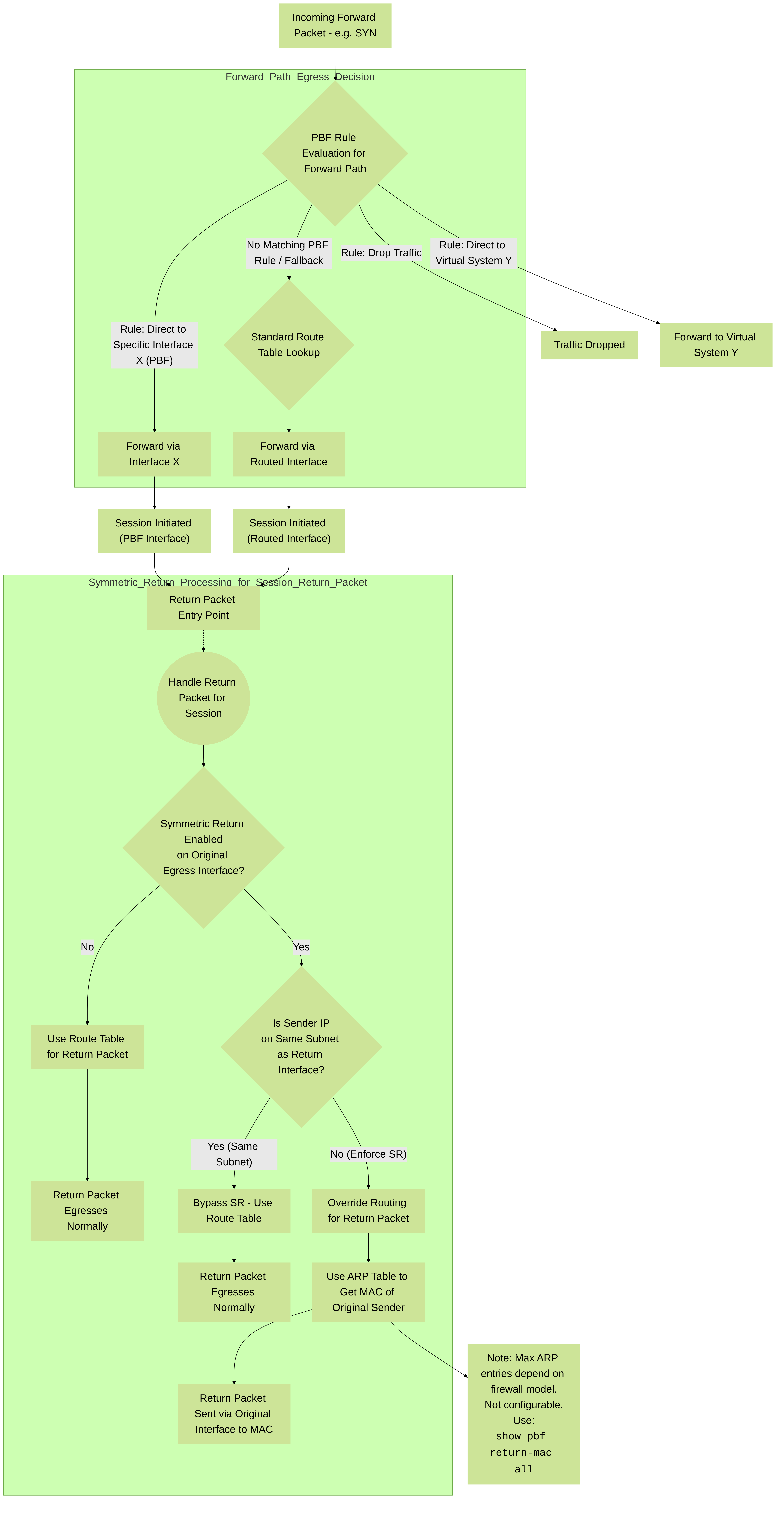
In networks with asymmetric routes, such as in a dual ISP environment, connectivity issues occur when traffic arrives at one interface on the firewall and leaves from another interface. If the route is asymmetrical, where the forward (SYN packet) and return (SYN/ACK) paths are different, the firewall is unable to track the state of the entire session and this causes a connection failure. To ensure that the traffic uses a symmetrical path, which means that the traffic arrives at and leaves from the same interface on which the session was created, you can enable the Symmetric Return option.
With symmetric return, the virtual router overrides a routing lookup for return traffic and instead directs the flow back to the MAC address from which it received the SYN packet (or first packet). However, if the destination IP address is on the same subnet as the ingress/egress interface’s IP address, a route lookup is performed and symmetric return is not enforced. This behavior prevents traffic from being silently discarded.
To determine the next hop for symmetric returns, the firewall uses an Address Resolution Protocol (ARP) table. The maximum number of entries that this ARP table supports is limited by the firewall model and the value is not user configurable. To determine the limit for your model, use the CLI command: show pbf return-mac all .
Path Monitoring for PBF
Path monitoring allows you to verify connectivity to an IP address so that the firewall can direct traffic through an alternate route, when needed. The firewall uses ICMP pings as heartbeats to verify that the specified IP address is reachable.
A monitoring profile allows you to specify the threshold number of heartbeats to determine whether the IP address is reachable. When the monitored IP address is unreachable, you can either disable the PBF rule or specify a fail-over or wait-recover action. Disabling the PBF rule allows the virtual router to take over the routing decisions. When the fail-over or wait-recover action is taken, the monitoring profile continues to monitor whether the target IP address is reachable, and when it comes back up, the firewall reverts back to using the original route.
The following table lists the difference in behavior for a path monitoring failure on a new session versus an established session.
| Condition | Rule Stays Enabled When Monitor Fails (disable rule is unchecked) | Rule Disabled When Monitor Fails (disable rule is checked) | ||
|---|---|---|---|---|
| wait-recover | fail-over | wait-recover | fail-over | |
| Established Sessions | Continue to use egress interface specified in PBF rule. | Continue to use egress interface specified in PBF rule. | Use path determined by routing table (no PBF). | Use path determined by routing table (no PBF). |
| New Sessions | Use path determined by routing table (no PBF). | Use path determined by routing table (no PBF). | Check the remaining PBF rules. If none match, use the routing table. | Check the remaining PBF rules. If none match, use the routing table. |
Service Versus Applications in PBF
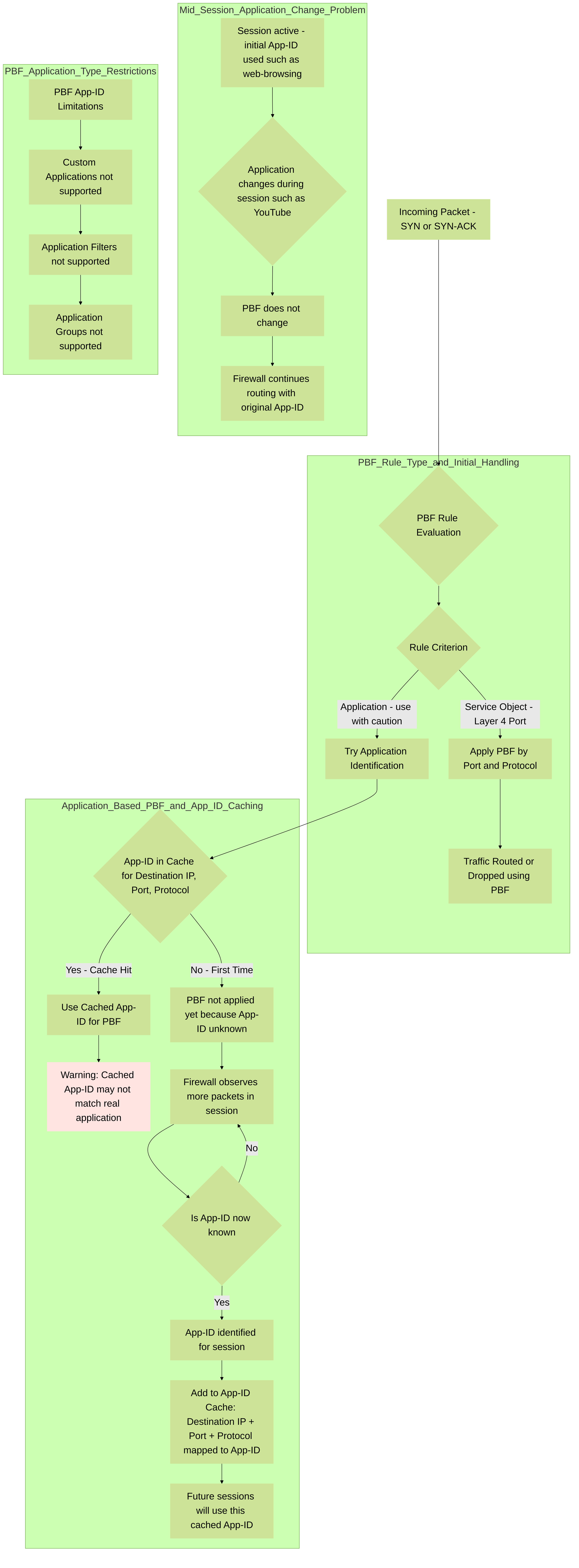
PBF rules are applied either on the first packet (SYN) or the first response to the first packet (SYN/ACK). This means that a PBF rule may be applied before the firewall has enough information to determine the application. Therefore, application-specific rules are not recommended for use with PBF. Whenever possible, use a service object, which is the Layer 4 port (TCP or UDP) used by the protocol or application.
However, if you specify an application in a PBF rule, the firewall performs App-ID caching . When an application passes through the firewall for the first time, the firewall does not have enough information to identify the application and therefore cannot enforce the PBF rule. As more packets arrive, the firewall determines the application and creates an entry in the App-ID cache and retains this App-ID for the session.When a new session is created with the same destination IP address, destination port, and protocol ID, the firewall could identify the application as the same from the initial session (based on the App-ID cache) and apply the PBF rule. Therefore, a session that is not an exact match and is not the same application, can be forwarded based on the PBF rule.
Further, applications have dependencies and the identity of the application can change as the firewall receives more packets. Because PBF makes a routing decision at the start of a session, the firewall cannot enforce a change in application identity. YouTube, for example, starts as web-browsing but changes to Flash, RTSP, or YouTube based on the different links and videos included on the page. However with PBF, because the firewall identifies the application as web-browsing at the start of the session, the change in application is not recognized thereafter.
You cannot use custom applications, application filters, or application groups in PBF rules.
Create a Policy-Based Forwarding Rule
Use a PBF rule to direct traffic to a specific egress interface on the firewall and override the default path for the traffic.
Before you create a PBF rule, make sure you understand that the set of IPv4 addresses is treated as a subset of the set of IPv6 addresses, as described in detail in Policy.
-
Create a Policy-Based Forwarding (PBF) rule.
When creating a PBF rule, you must specify a name for the rule, a source zone or interface, and an egress interface. All other components are either optional or have a default value.
You can specify the source and destination addresses using an IP address, an address object, or an FQDN.
-
Select Policies > Policy Based Forwarding and Add a PBF policy rule.
-
Give the rule a descriptive name ( General tab).
-
Select Source tab and configure the following:
-
Select the Type ( Zone or Interface ) to which you will apply the forwarding policy and specify the relevant zone or interface. If you want to enforce symmetric return, you must select a source interface.
-
Only Layer 3 interfaces support PBF; loopback interfaces do not support PBF.
-
( Optional ) Specify the Source Address to which the PBF rule applies. For example, a specific IP address or subnet IP address from which you want to forward traffic to the interface or zone specified in this rule.
Click Negate to exclude one or more Source Addresses from the PBF rule. For example, if your PBF rule directs all traffic from the specified zone to the internet, Negate allows you to exclude internal IP addresses from the PBF rule.
The evaluation order is top down. A packet is matched against the first rule that meets the defined criteria; after a match is triggered, subsequent rules are not evaluated.
-
( Optional ) Add and select the Source User or groups of users to whom the policy applies.
-
Select Destination/Application/Service tab and configure the following:
-
Destination Address —By default, the rule applies to Any IP address. Click Negate to exclude one or more destination IP addresses from the PBF rule.
-
Add any Application and Service that you want to control using PBF.
-
We do not recommend application-specific rules for use with PBF because PBF rules may be applied before the firewall has enough information to determine the application. Whenever possible, use a service object, which is the Layer 4 port (TCP or UDP) used by the protocol or application. For more details, see Service Versus Applications in PBF.
-
Specify how to forward packets that match the rule ( Forwarding tab).
If you are configuring PBF in a multi-VSYS environment, you must create separate PBF rules for each virtual system (and create the appropriate Security policy rules to enable the traffic).
-
Set the Action to take when matching a packet:
-
Forward —Directs the packet to the specified Egress Interface .
-
Forward to VSYS ( On a firewall enabled for multiple virtual systems )—Select the virtual system to which to forward the packet.
-
Discard —Drops the packet.
-
No PBF —Excludes packets that match the criteria for source, destination, application, or service defined in the rule. Matching packets use the route table instead of PBF; the firewall uses the route table to exclude the matched traffic from the redirected port.
-
-
To trigger the specified Action at a daily, weekly, or non-recurring frequency, create and attach a Schedule .
-
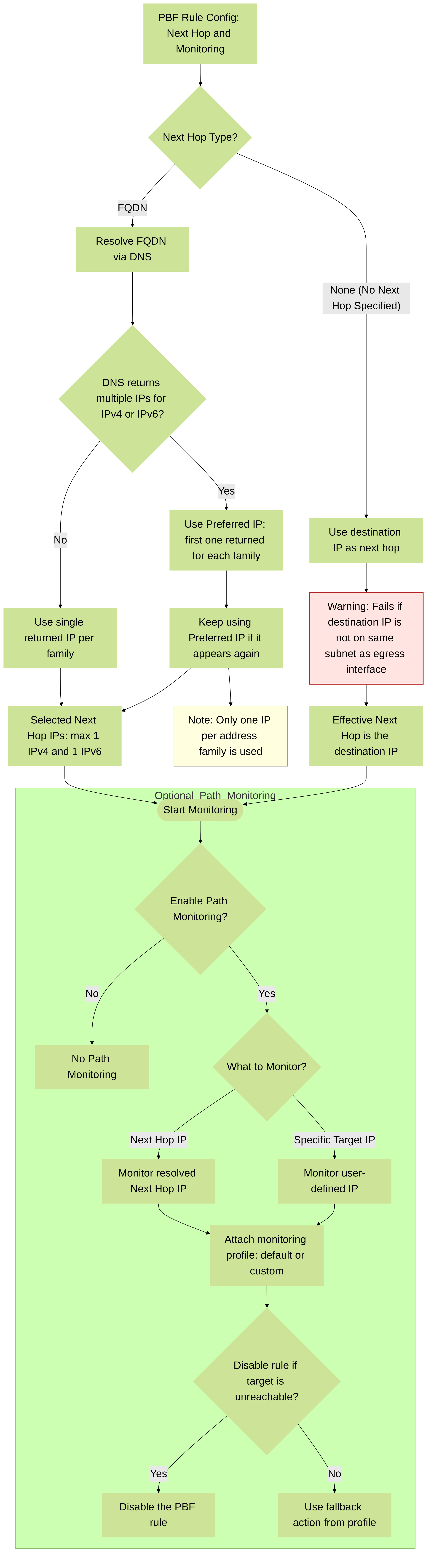
For Next Hop , select one of the following:
-
IP Address —Enter an IP address or select an address object of type IP Netmask to which the firewall forwards matching packets. An IPv4 address object must have a /32 netmask and an IPv6 address object must have a /128 netmask.
-
FQDN —Enter an FQDN (or select or create an address object of type FQDN) to which the firewall forwards matching packets. The FQDN can resolve to an IPv4 address, an IPv6 address, or both. If the FQDN resolves to both IPv4 and IPv6 addresses, then the PBF rule has two next hops: one IPv4 address and one IPv6 address. You can use the same PBF rule for both IPv4 and IPv6 traffic. IPv4 traffic is forwarded to the IPv4 next hop; IPv6 traffic is forwarded to the IPv6 next hop.
-
This FQDN must resolve to an IP address that belongs to the same subnet as the interface you configured for PBF; otherwise, the firewall rejects the resolution and the FQDN remains unresolved.
The firewall uses only one IP address (from each IPv4 or IPv6 family type) from the DNS resolution of the FQDN. If the DNS resolution returns more than one address, the firewall uses the preferred IP address that matches the IP family type (IPv4 or IPv6) configured for the next hop. The preferred IP address is the first address the DNS server returns in its initial response. The firewall retains this address as preferred as long as the address appears in subsequent responses, regardless of order.
-
None —No next hop mean the destination IP address of the packet is used as the next hop. Forwarding fails if the destination IP address is not in the same subnet as the egress interface.
-
( Optional ) Enable monitoring to verify connectivity to a target IP address or to the Next Hop IP address if no IP address is specified. Select Monitor and attach a monitoring Profile (default or custom) that specifies the action when the monitored address is unreachable.
-
You can Disable this rule if nexthop/monitor ip is unreachable .
-
Enter a target IP Address to monitor.
-
The Egress Interface can have both IPv4 and IPv6 addresses and the Next Hop FQDN can resolve to both IPv4 and IPv6 addresses. In this case:
-
If the egress interface has both IPv4 and IPv6 addresses and the next hop FQDN resolves to only one address family type, the firewall monitors the resolved IP address. If the FQDN resolves to both IPv4 and IPv6 addresses but the egress interface has only one address family type address, the firewall monitors the resolved next hop address that matches the address family of the egress interface.
-
If both the egress interface and next hop FQDN have both IPv4 and IPv6 addresses, the firewall monitors the IPv4 next hop address.
-
If the egress interface has one address family address and the next hop FQDN resolves to a different address family address, the firewall does not monitor anything.
-
( Required for asymmetric routing environments; otherwise, optional ) Enforce Symmetric Return and Add one or more IP addresses in the Next Hop Address List . You can add up to 8 next-hop IP addresses; tunnel and PPoE interfaces are not available as a next-hop IP address.
Enabling symmetric return ensures that return traffic (such as from the Trust zone on the LAN to the internet) is forwarded out through the same interface through which traffic ingresses from the internet.
-
Commit your changes. The PBF rule is in effect.
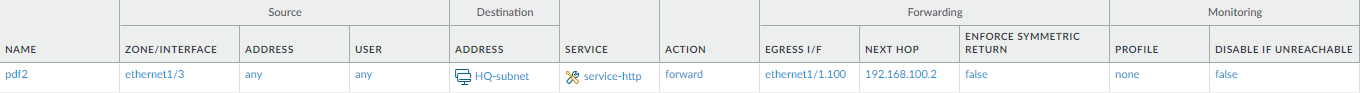
Use Case: PBF for Outbound Access with Dual ISPs
In this use case, the branch office has a dual ISP configuration and implements PBF for redundant internet access. The backup ISP is the default route for traffic from the client to the web servers. In order to enable redundant internet access without using an internetwork protocol such as BGP, we use PBF with destination interface-based source NAT and static routes, and configure the firewall as follows:
-
Enable a PBF rule that routes traffic through the primary ISP, and attach a monitoring profile to the rule. The monitoring profile triggers the firewall to use the default route through the backup ISP when the primary ISP is unavailable.
-
Define Source NAT rules for both the primary and backup ISP that instruct the firewall to use the source IP address associated with the egress interface for the corresponding ISP. This ensures that the outbound traffic has the correct source IP address.
-
Add a static route to the backup ISP, so that when the primary ISP is unavailable, the default route comes into effect and the traffic is directed through the backup ISP.
-
Configure the ingress and the egress interfaces on the firewall.
Egress interfaces can be in the same zone.
-
Select Network > Interfaces and select the interface you want to configure.
The interface configuration on the firewall used in this example is as follows:
-
Ethernet 1/19 connected to the primary ISP:
- Zone: TwoISP
- IP Address: 1.1.1.2/30
- Virtual Router: Default
-
Ethernet 1/20 connected to the backup ISP:
- Zone: TwoISP
- IP Address: 2.2.2.2/30
- Virtual Router: Default
-
Ethernet 1/2 is the ingress interface, used by the network clients to connect to the internet:
- Zone: Corporate
- IP Address: 192.168.54.1/24
- Virtual Router: Default
-
To save the interface configuration, click OK .
-
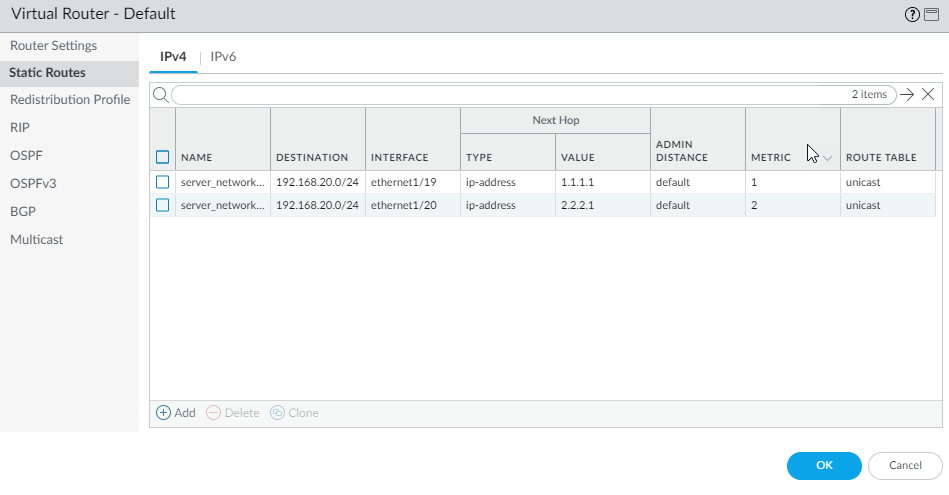
On the virtual router, add a static route to the backup ISP.
-
Select Network > Virtual Router and select the default link to open the Virtual Router dialog.
-
Select Static Routes and click Add . Enter a Name for the route and specify the Destination IP address for which you are defining the static route. In this example, we use 0.0.0.0/0 for all traffic.
-
Select the IP Address radio button and set the Next Hop IP address for your router that connects to the backup internet gateway (you cannot use a domain name for the next hop). In this example, 2.2.2.1.
-
Specify a cost metric for the route.
-
-
Click OK twice to save the virtual router configuration.
-
Create a PBF rule that directs traffic to the interface that is connected to the primary ISP.
Make sure to exclude traffic destined to internal servers/IP addresses from PBF. Define a negate rule so that traffic destined to internal IP addresses is not routed through the egress interface defined in the PBF rule.
-
Select Policies > Policy Based Forwarding and click Add .
-
Give the rule a descriptive Name in the General tab.
-
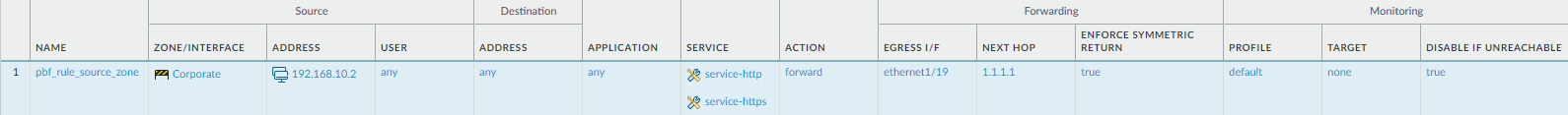
In the Source tab, set the Source Zone ; in this example, the zone is Corporate.
-
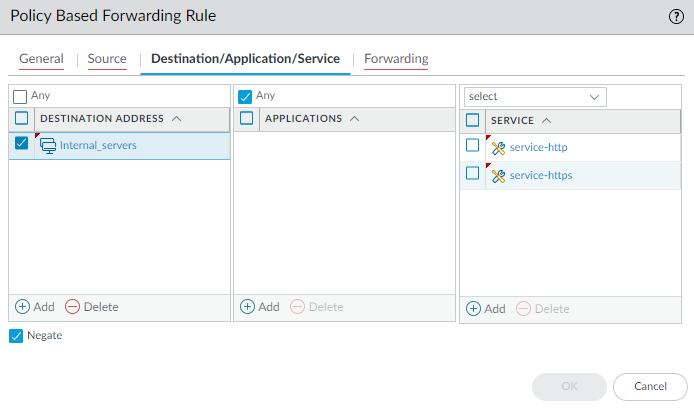
In the Destination/Application/Service tab, set the following:
-
In the Destination Address section, Add the IP addresses or address range for servers on the internal network or create an address object for your internal servers. Select Negate to exclude the IP addresses or address object listed above from using this rule.
-
In the Service section, Add the service-http and service-https services to allow HTTP and HTTPS traffic to use the default ports. For all other traffic that is allowed by security policy, the default route will be used.
-
To forward all traffic using PBF, set the Service to Any .
-
Specify where to forward traffic.
-
In the Forwarding tab, specify the interface to which you want to forward traffic and enable path monitoring.
-
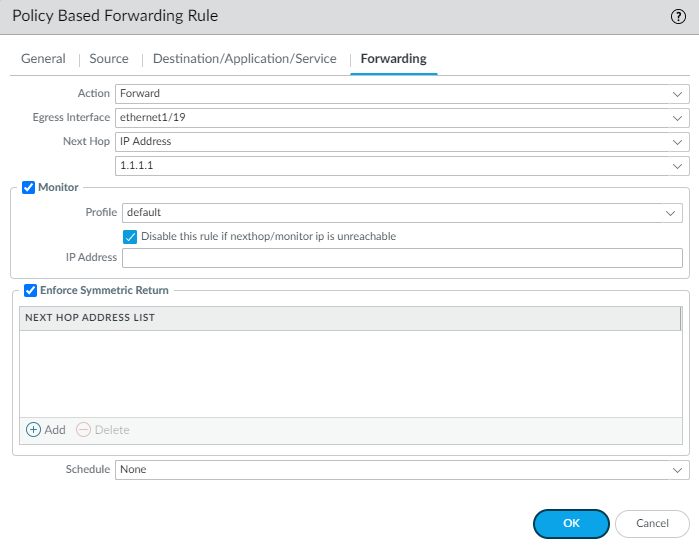
To forward traffic, set the Action to Forward , and select the Egress Interface and specify the Next Hop . In this example, the egress interface is ethernet1/19, and the next hop IP address is 1.1.1.1 (you cannot use a FQDN for the next hop).
-
-
Enable Monitor and attach the default monitoring profile to trigger a failover to the backup ISP. In this example, we do not specify a target IP address to monitor. The firewall will monitor the next hop IP address; if this IP address is unreachable, the firewall will direct traffic to the default route specified on the virtual router.
-
( Required if you have asymmetric routes ) Select Enforce Symmetric Return to ensure that return traffic from the Corporate zone to the internet is forwarded out on the same interface through which traffic ingressed from the internet.
-
NAT ensures that the traffic from the internet is returned to the correct interface/IP address on the firewall.
-
Click OK to save the changes.
-
Create NAT rules based on the egress interface and ISP. These rules ensure that the correct source IP address is used for outbound connections.
-
Select Policies > NAT and click Add .
-
In this example, the NAT rule we create for each ISP is as follows:
-
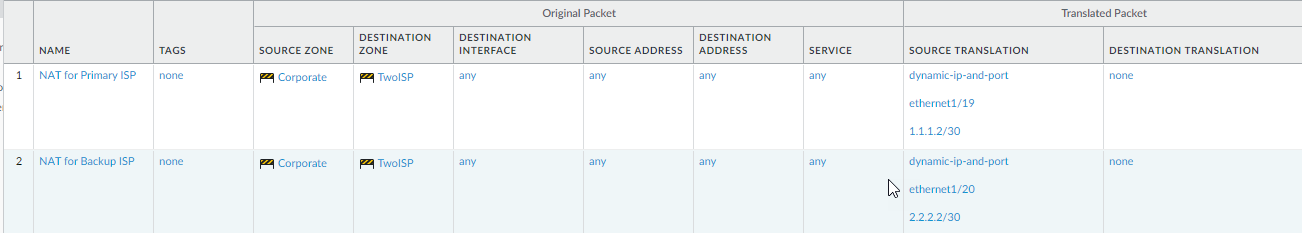
NAT for Primary ISP
In the Original Packet tab,
- Source Zone : Corporate
- Destination Zone : TwoISP
In the Translated Packet tab, under Source Address Translation
- Translation Type : Dynamic IP and Port
- Address Type : Interface Address
- Interface : ethernet1/19
- IP Address : 1.1.1.2/30
NAT for Backup ISP
In the Original Packet tab,
- Source Zone : Corporate
- Destination Zone : TwoISP
In the Translated Packet tab, under Source Address Translation
- Translation Type : Dynamic IP and Port
- Address Type : Interface Address
- Interface : ethernet1/20
- IP Address : 2.2.2.2/30
-
Create security policy to allow outbound access to the internet.
To safely enable applications, create a simple rule that allows access to the internet and attach the security profiles available on the firewall.
-
Select Policies > Security and click Add .
-
Give the rule a descriptive Name in the General tab.
-
In the Source tab, set the Source Zone to Corporate.
-
In the Destination tab, Set the Destination Zone to TwoISP.
-
In the Service/ URL Category tab, leave the default application-default .
-
In the Actions tab, complete these tasks:
- Set the Action Setting to Allow .
- Attach the default profiles for Antivirus, Anti-Spyware, Vulnerability Protection and URL Filtering, under Profile Setting.
-
Under Options , verify that logging is enabled at the end of a session. Only traffic that matches a security rule is logged.

-
Save the policies to the running configuration on the firewall.
Click Commit .
-
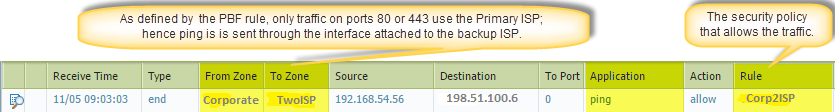
Verify that the PBF rule is active and that the primary ISP is used for internet access.
- Launch a web browser and access a web server. On the firewall, check the traffic log for web-browsing activity.
- From a client on the network, use the ping utility to verify connectivity to a web server on the internet, and check the traffic log on the firewall.
C:\Users\pm-user1> ping 198.51.100.6 Pinging 198.51.100.6 with 32 bytes of data: Reply from 198.51.100.6: bytes=32 time=34ms TTL=117 Reply from 198.51.100.6: bytes=32 time=13ms TTL=117 Reply from 198.51.100.6: bytes=32 time=25ms TTL=117 Reply from 198.51.100.6: bytes=32 time=3ms TTL=117 Ping statistics for 198.51.100.6: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milliseconds: Minimum = 3ms, Maximum = 34ms, Average = 18ms
-
To confirm that the PBF rule is active, use the following CLI command:
-
Verify that the failover to the backup ISP occurs and that the Source NAT is correctly applied.
- Unplug the connection to the primary ISP.
- Confirm that the PBF rule is inactive with the following CLI command:
admin@PA-NGFW> show pbf rule all
Rule ID Rule State Action Egress IF/VSYS NextHop
========== === ========== ====== ============== ===
Use ISP-Pr 1 Disabled Forward ethernet1/19 1.1.1.1
-
Access a web server, and check the traffic log to verify that traffic is being forwarded through the backup ISP.
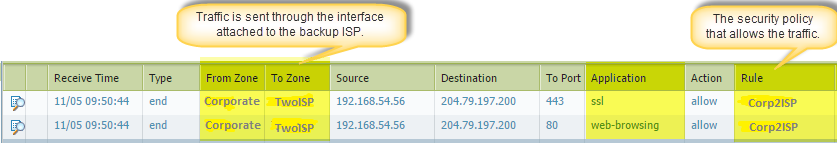
-
View the session details to confirm that the NAT rule is working properly.
admin@PA-NGFW> show session all
---------------------------------------------------------
ID Application State Type Flag Src[Sport]/Zone/Proto (translated IP[Port]) Vsys Dst[Dport]/Zone (translated IP[Port])
---------------------------------------------------------
87212 ssl ACTIVE FLOW NS 192.168.54.56[53236]/Corporate/6 (2.2.2.2[12896]) vsys1 204.79.197.200[443]/TwoISP (204.79.197.200[443])
-
Obtain the session identification number from the output and view the session details.
The PBF rule is not used and hence is not listed in the output.