PCNSE Route Monitoring & Troubleshooting Guide
1. Route Monitoring Overview
Route monitoring in Palo Alto Networks firewalls is a crucial feature for ensuring network reliability and high availability. It primarily involves two main areas: path monitoring for static routes and the monitoring of dynamic routing protocol states. Effective monitoring allows the firewall to detect reachability issues or protocol failures and take corrective actions, such as removing an invalid route or failing over to a redundant path. This ensures traffic continues to flow and minimizes network downtime. Understanding these mechanisms is vital for the PCNSE exam.
2. Static Route Path Monitoring In-Depth
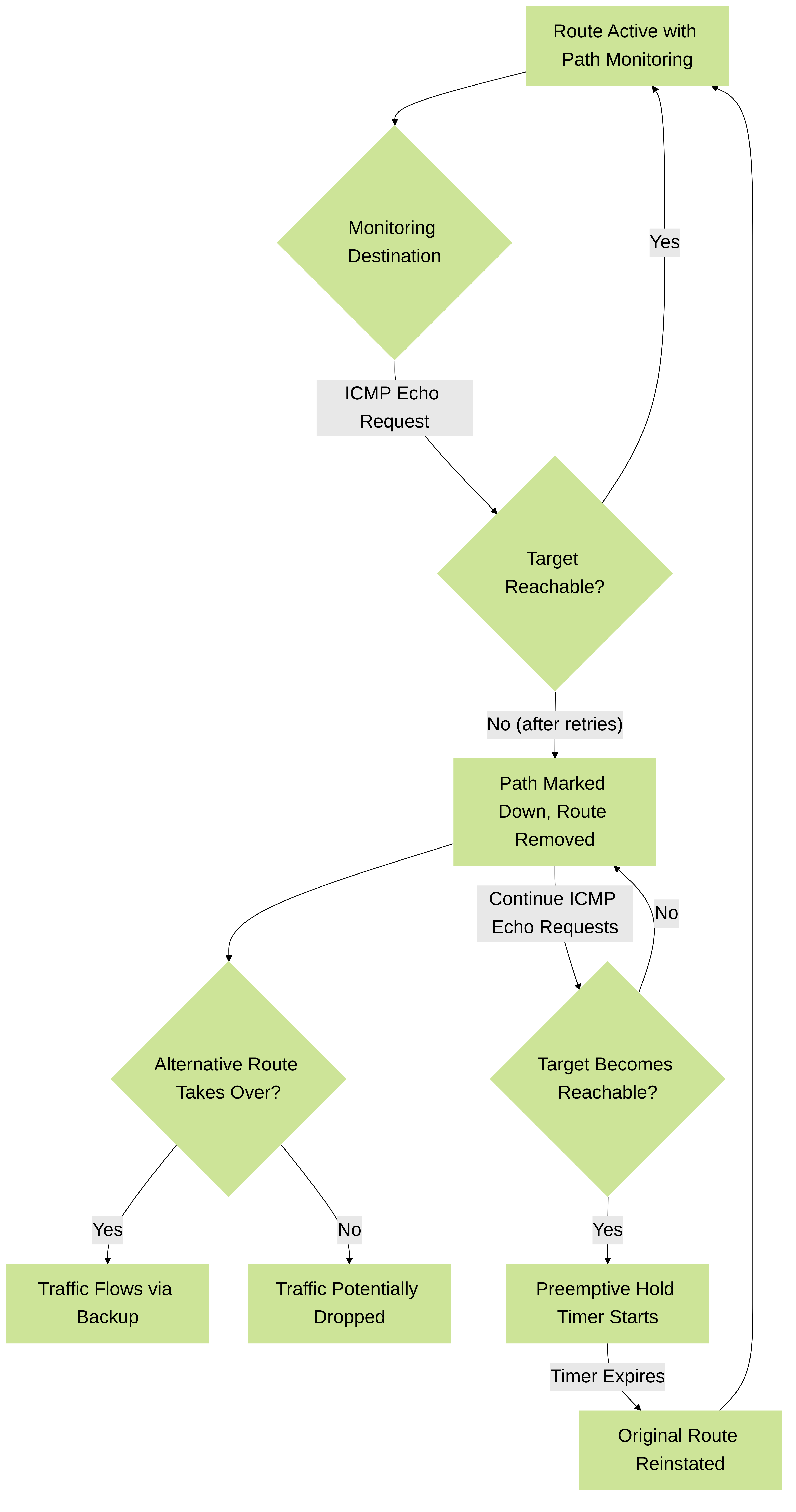
Path monitoring is specifically used for static routes to verify the reachability of a next-hop or a specific destination IP address. If the monitored destination becomes unreachable, the firewall can automatically remove the associated static route from the routing table, allowing an alternative route (perhaps another static route with a higher metric or a dynamically learned route) to take over.
2.1. The Monitoring Process
The firewall sends ICMP (ping) echo requests to the specified monitored IP address at configurable intervals. If responses are not received within a certain threshold (defined by ping interval and count), the path is considered down. It's important that the monitored IP is a reliable indicator of the path's health. A single ping packet failure does not necessarily mean the path is down; it's typically based on a series of failed pings.
2.2. Failure Detection and Failover Action
When path monitoring determines that the monitored destination is unreachable, the static route is flagged as invalid and removed from the firewall's Routing Information Base (RIB). This triggers the routing engine to find an alternative path. If no other specific route exists, traffic destined for that network might use a default route or be dropped if no route is available.
You can configure whether "any" monitored IP or "all" monitored IPs in a group must fail for the route to be removed.
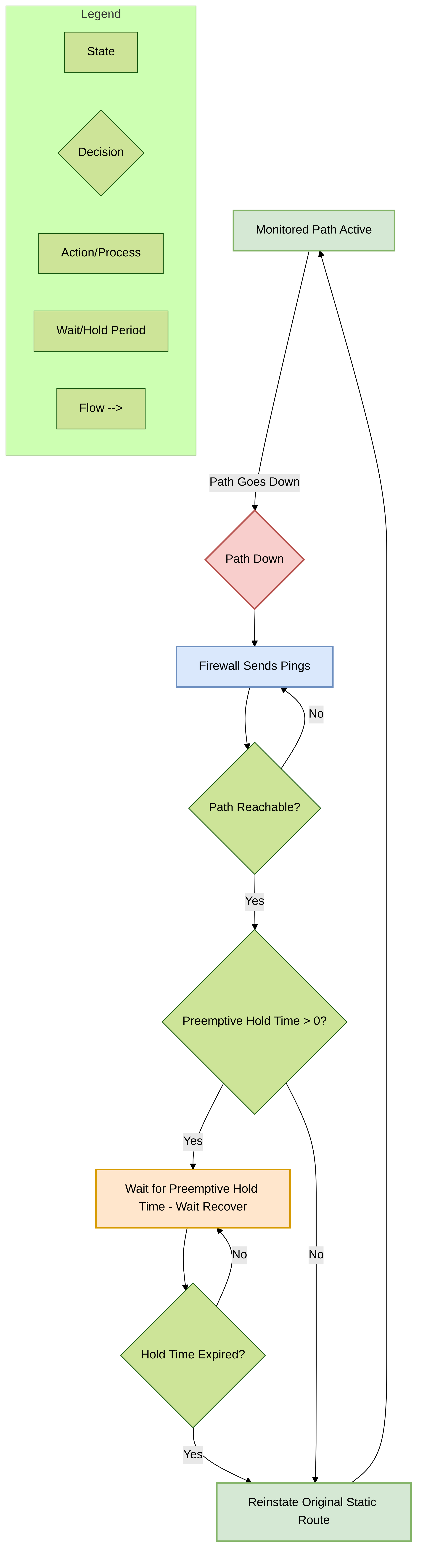
2.3. Wait Recover Time and Preemptive Hold Time
Once a monitored path goes down, the firewall continues to send pings to check for recovery. The
The term "Wait Recover" is conceptually linked to this preemptive behavior. The firewall "waits" to "recover" the route by using the preemptive hold timer to ensure stability before making the route active again.
2.4. Logging Path Monitoring Events
Path monitoring events are logged in the
-
When a path fails: An event with an ID like
Path monitoring failedorROUTING_PATHTEST_FAILmight be logged, indicating the route was removed. -
When a path recovers: An event with an ID like
Path monitoring recoveredorROUTING_PATHTEST_RECOVERmight be logged, indicating the route was restored after the preemptive hold time.
To find these logs:
- Navigate to Monitor > Logs > System in the WebUI.
-
Use the CLI command:
less mp-log routed.logto view the routing daemon log for more detailed troubleshooting. -
System log filter in the WebUI:
( subtype eq 'routing' ) and ( description contains 'Path monitoring' )or specific event IDs like( eventid eq 'routed-path-mon-down' )or( eventid eq 'routed-path-mon-up' )(Note: exact event IDs can vary slightly by PAN-OS version, always verify with current documentation or by observing logs). The messages "Path monitoring failed for static route destinationwith next hop . Route removed." and "Path monitoring for static route destination with next hop . Recovered. Route restored." are common.
You can also use the CLI command
show routing path-monitor
to check the current status of monitored paths.
Detailed Path Monitoring Lifecycle
3. Dynamic Routing Protocol Monitoring
Palo Alto Networks firewalls support dynamic routing protocols such as OSPF and BGP. Monitoring their state, especially neighborship or peerings, is critical for network stability.
3.1. Importance of Neighborship/Adjacency
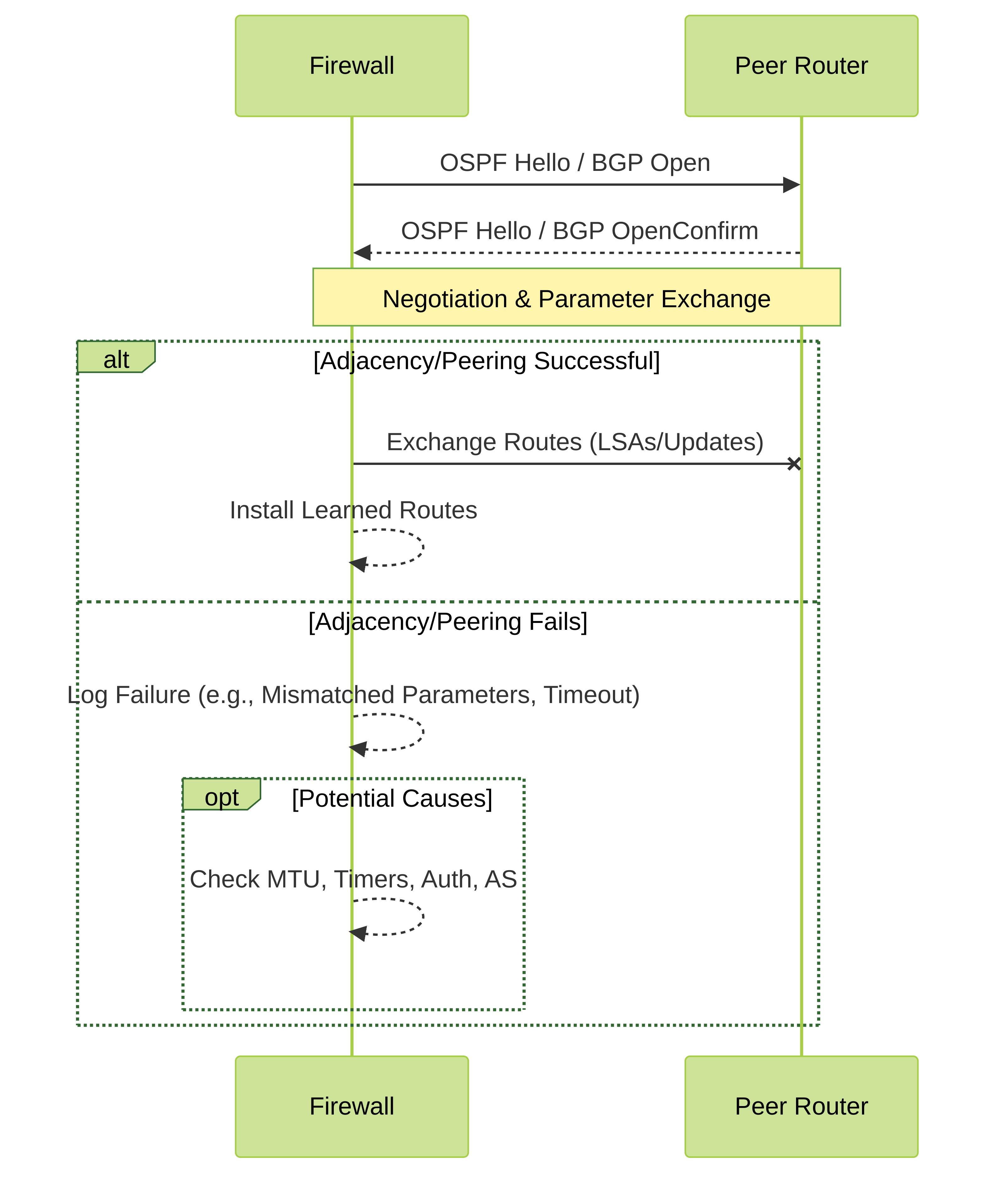
Dynamic routing protocols rely on forming neighborships (OSPF) or peerings (BGP) with adjacent routers to exchange routing information. If a neighborship fails, routes learned through that neighbor are withdrawn, potentially leading to routing black holes or suboptimal routing until convergence occurs via an alternate path.
3.2. Detecting Failures
Failures in dynamic routing protocols can be detected through several methods:
-
CLI Commands:
-
OSPF:
show routing protocol ospf neighbor(to check neighbor states). Other useful OSPF commands includeshow routing protocol ospf interfaceandshow routing protocol ospf lsdb. -
BGP:
show routing protocol bgp peer(to check peer states and received prefixes).
-
OSPF:
-
System Logs:
-
OSPF neighborship changes (e.g., going down or coming up) generate system log entries. Look for event IDs like
routed-OSPF-neighbor-downor messages like "OSPF adjacency with neighbor has gone down".Search in System Logs:
( subtype eq 'routing' ) and ( description contains 'OSPF' )or( eventid eq 'routed-OSPF-neighbor-down' ). -
BGP peer state changes also generate logs. Look for event IDs like
BGP_PEER_CONN_LOSTor messages like "BGP peer session left established state".Search in System Logs:
( subtype eq 'routing' ) and ( description contains 'BGP' )or( eventid eq 'routed-bgp-peer-down' )(Note: actual event IDs can vary). BGP log messages might indicate if a peer closed the session. -
The primary log file for routing daemon activities is
routed.logon the management plane. This can be viewed via CLI:less mp-log routed.logor for real-time viewing:tail follow yes mp-log routed.log. This log provides detailed reasons for adjacency failures, such as mismatched MTU, timers, or authentication issues.
-
OSPF neighborship changes (e.g., going down or coming up) generate system log entries. Look for event IDs like
For OSPF, common reasons for adjacency issues include mismatched Area IDs, Hello/Dead timers, authentication, MTU sizes, or network type. For BGP, common issues include incorrect AS numbers, IP addresses, TCP port 179 being blocked, or authentication.
Dynamic Routing Adjacency/Peering Process
4. Tracking General Route Changes
Beyond specific path monitoring or protocol neighborships, general route additions, deletions, or modifications in the routing table are also logged.
-
System Logs:
Events related to route table modifications can be found in the System Log. Look for messages indicating routes being added or removed by different protocols (static, OSPF, BGP).
Search in System Logs:
( subtype eq 'routing' ) and ( eventid contains 'ROUTING_RT_' )or filtering for descriptions containing "route added" or "route removed". The configuration log also tracks changes made to the firewall's configuration, which includes static route definitions. -
Viewing the Routing Table:
-
show routing route: Displays the entire RIB (Routing Information Base), showing all routes known to the firewall, their administrative distances, and metrics. -
show routing fib: Displays the FIB (Forwarding Information Base), which contains the actual routes installed and used for forwarding traffic. -
test routing fib-lookup virtual-router [vr_name] ip [destination_ip]: Simulates a route lookup for a specific destination.
-
Understanding Administrative Distance (AD) is crucial. If multiple protocols provide a route to the same destination, the route with the lowest AD is preferred. If ADs are equal, the protocol-specific metric is used.
5. Other Methods of Monitoring and Advanced Techniques
- SNMP Traps: The firewall can be configured to send SNMP traps for various system events, including routing-related events like BGP peer state changes or OSPF neighbor changes.
- Log Forwarding: System logs, including routing logs, can be forwarded to external syslog servers or Security Information and Event Management (SIEM) systems for centralized analysis and alerting.
- Panorama: If using Panorama for centralized management, logs from managed firewalls are aggregated, providing a central point for monitoring and troubleshooting routing events across multiple devices.
- ACC (Application Command Center): While not a direct routing monitor, the ACC can provide insights into traffic patterns. Unexpected changes in traffic flow or application reachability can indirectly indicate underlying routing issues.
- Packet Captures: For in-depth troubleshooting, especially for dynamic routing protocol issues, packet captures can be invaluable. You can capture traffic on specific interfaces to analyze protocol messages.
WebUI: Monitor > Packet Capture
CLI:
debug routing pcap
6. Troubleshooting Routes (Summary)
Effective troubleshooting involves a systematic approach:
- Verify Configuration: Double-check static route settings, path monitoring parameters, and dynamic routing protocol configurations (Area IDs, AS numbers, authentication, timers, network advertisements).
-
Check Interface Status:
Ensure physical and logical interfaces involved in routing are up and correctly configured. Use
show interface. -
Examine Routing Tables:
Use
show routing routeandshow routing fibto understand what routes are present and active. -
Path Monitoring Status:
For static routes, use
show routing path-monitor. -
Dynamic Protocol Status:
-
OSPF:
show routing protocol ospf neighbor,show routing protocol ospf interface. -
BGP:
show routing protocol bgp peer.
-
OSPF:
-
Analyze Logs:
- System Logs (Monitor > Logs > System): Filter for 'routing' subtype and keywords like 'path-monitor', 'OSPF', 'BGP', or specific event IDs.
-
routed.log(CLI:less mp-log routed.logortail follow yes mp-log routed.log): For detailed daemon-level messages.
-
Test Connectivity:
Use
pingandtraceroutefrom the firewall CLI (specifying source interface/IP if necessary) and from affected hosts. - Packet Captures: If protocol issues are suspected (e.g., OSPF adjacency stuck, BGP messages not exchanged).
7. Common Pitfalls (Gotchas) for PCNSE Exam Takers
- Incorrect Path Monitoring IP: Monitoring an IP that isn't a reliable indicator of the entire path's health, or an IP that doesn't respond to ICMP.
- Path Monitoring Source Interface: Path monitoring pings for static routes originate from the firewall's dataplane interface assigned to the next-hop of the static route, or as specified. Ensure this is intended.
- Preemptive Hold Time Misunderstanding: Forgetting its purpose or configuring it too low (causing flapping) or too high (delaying primary path restoration). A value of 0 means immediate reinstatement.
-
Dynamic Routing Adjacency Issues:
- OSPF: Mismatched Area ID, Hello/Dead timers, MTU, authentication, passive interface settings, or network types.
- BGP: Incorrect peer IP/AS, TCP port 179 blocked by security policy or an intermediate device, mismatched timers or authentication. Control plane traffic like BGP might hit default interzone/intrazone policies if not explicitly allowed, and these default policies often don't have logging enabled.
- Route Redistribution: Incorrectly configured redistribution profiles leading to missing routes or routing loops. Understanding how to filter routes during redistribution is key.
- Administrative Distance vs. Metric: Confusing these or not knowing default AD values for different route types (Static, OSPF Internal/External, BGP eBGP/iBGP).
-
Log Analysis:
Not knowing where to find relevant logs (System vs. Traffic vs. specific daemon logs like
routed.log) or how to filter them effectively. - Uncommitted Changes: Always commit configuration changes; otherwise, they won't take effect.
- Virtual Routers: Ensuring interfaces and routing protocols are configured within the correct virtual router instance.