🔄 Palo Alto Networks BFD Implementation Guide
Introduction to Bidirectional Forwarding Detection (BFD)
Bidirectional Forwarding Detection (BFD) is a network protocol designed to rapidly detect faults in the path between two forwarding engines (like routers or firewalls). Its primary purpose is to provide much faster failure detection times than the native mechanisms built into many routing protocols (e.g., OSPF Hellos, BGP Keepalives). This allows for quicker network convergence and minimized traffic disruption in the event of a link or device failure.
Why is BFD Needed? (The BFD Reason)
Traditional routing protocols often have Hello/Keepalive timers in the order of seconds (e.g., OSPF default dead interval is 40 seconds, BGP default hold time is 180 seconds). In modern networks, especially those carrying real-time traffic like VoIP or critical business applications, these detection times are too slow and can lead to significant service interruption. BFD addresses this by:
- Speed: Detecting failures in milliseconds or even sub-second intervals.
- Low Overhead: BFD control packets are lightweight and can often be processed in the forwarding plane, reducing CPU load on the control plane.
- Protocol Independence: BFD can provide a consistent failure detection mechanism across various routing protocols and even for static routes.
How BFD Works: The Basics
BFD operates by establishing a session between two devices over a specific path. These devices then exchange BFD control packets at a pre-negotiated, regular interval. If one device stops receiving these packets from its peer for a certain period (determined by a detection multiplier and the negotiated interval), it declares the BFD session, and thus the path, as down.
Key components of BFD operation include:
- BFD Control Packets: Small UDP packets used to establish, maintain, and terminate BFD sessions. Single-hop BFD typically uses UDP port 3784, while multihop BFD uses UDP port 4784. Palo Alto Networks firewalls also support BFD Echo function, which uses UDP port 3785.
-
Session States:
A BFD session transitions through several states:
- Down: No active BFD session.
- Init: The local system can communicate with the remote system but bidirectional communication is not yet established.
- Up: Bidirectional communication is established, and the path is considered active and monitored.
-
Timers:
-
Desired Minimum Tx Interval: The minimum interval at which the local system wants to send BFD control packets. -
Required Minimum Rx Interval: The minimum interval at which the local system can accept BFD control packets. -
Detect Multiplier: The number of consecutive BFD packets that can be missed before the session is declared down. The detection time is calculated as the negotiated transmit interval multiplied by the Detection Time Multiplier.
-
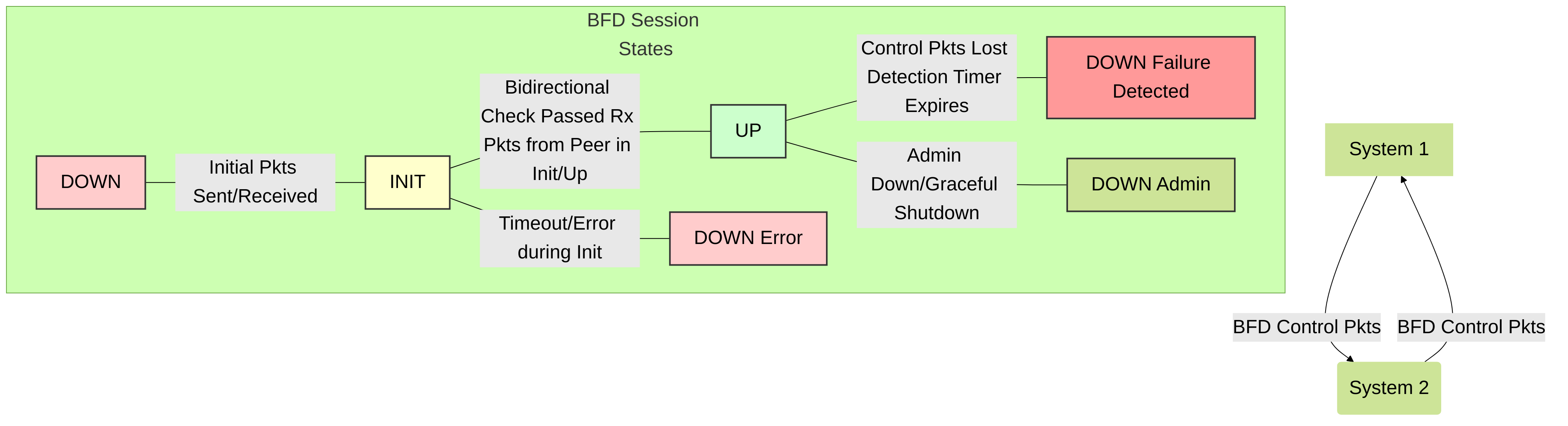
Figure 1: BFD Session States and Basic Communication
BFD Modes of Operation
BFD primarily operates in a few modes, with Asynchronous mode being the most common and relevant for Palo Alto Networks firewalls:
- Asynchronous Mode: Both BFD peers periodically send control packets to each other at the negotiated interval. If a certain number of these packets are missed (based on the detection multiplier), the session is declared down. Palo Alto Networks' implementation of BFD operates in asynchronous mode after session establishment.
- Demand Mode: Once a BFD session is up, one system can request the other to stop sending periodic control packets. Control packets are then only sent as needed. Palo Alto Networks documentation primarily focuses on asynchronous mode.
- Echo Function: One device sends BFD Echo packets, and the peer loops them back without fully processing them at the BFD protocol level. If the sender doesn't receive its Echo packets back, it declares the session down. This mode can test the forwarding path with minimal load on the peer's control plane. The BFD Echo function is often used for single-hop paths.
BFD Failure Detection and Remediation
When a fault occurs in the forwarding path (e.g., interface failure, link interruption, or unresponsive forwarding engine), the BFD peer will stop receiving BFD control packets.
- Detection: The local BFD process on the detecting router notices the absence of incoming BFD control packets from its peer.
- Timer Expiry: After the detection time (Negotiated Tx Interval * Detect Multiplier) expires without receiving BFD packets, the local BFD session transitions to the DOWN state.
- Notification: BFD immediately notifies its client applications (e.g., routing protocols like OSPF, BGP, or the static routing process) about the path failure.
-
Remediation (Routing Protocol Action):
- The client routing protocol then takes appropriate action. For example, an OSPF neighbor adjacency might be torn down, a BGP peer declared unreachable, or a static route invalidated.
- The routing protocol will then attempt to reconverge by removing the failed path from its routing table and calculating an alternative path if one exists.
This rapid notification allows the routing protocols to converge much faster than they would using their own, slower keepalive mechanisms, thus significantly reducing packet loss and network downtime.
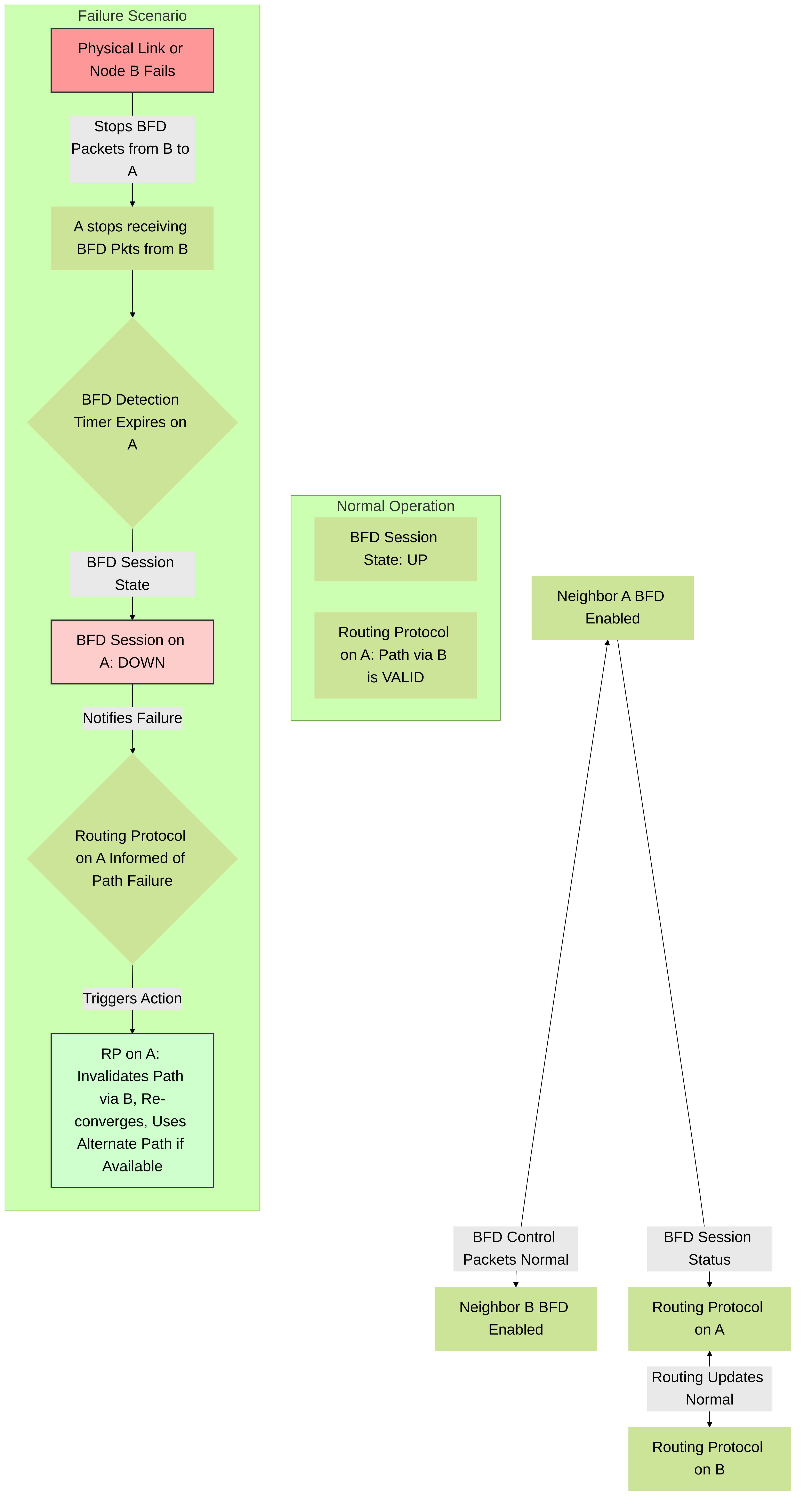
Figure 2: BFD Failure Detection and Remediation Process
1. Overview of BFD Support in Palo Alto Networks
Palo Alto Networks firewalls support Bidirectional Forwarding Detection (BFD) for the following routing protocols and static routes:
- Static Routes : BFD provides fast failure detection for the next-hop gateway of a static route. If the BFD session to the next-hop fails, the static route is removed from the routing table, allowing for failover to an alternate route or floating static route.
- BGP (Border Gateway Protocol) : BFD enables quicker detection of BGP peer failures compared to BGP's native keepalive and hold timers, leading to faster routing convergence.
- OSPFv2 and OSPFv3 (Open Shortest Path First) : BFD allows OSPF to rapidly detect neighbor unreachability, leading to faster SPF calculations and network reconvergence.
- RIPv2 (Routing Information Protocol version 2) : While RIP has its own timers, BFD can provide more aggressive failure detection for RIP adjacencies.
BFD provides rapid detection of faults in the path between forwarding engines, enabling faster failover than traditional methods. Some firewall models, like the PA-800 series, PA-220, and VM-50, do not support BFD, while others like the PA-400 series gained support in later PAN-OS versions (e.g., PAN-OS 11.0+). Always check the latest Palo Alto Networks documentation for specific model support.
2. Multihop BFD Implementation
The firewall's implementation of multihop BFD adheres to the encapsulation portion of RFC 5883 but does not support BFD-specific authentication. BFD control packets for multihop support are transmitted over UDP port 4784. To achieve authentication for BGP sessions using multihop BFD, configure BFD within a VPN tunnel (e.g., IPsec). The VPN's inherent authentication mechanisms can then secure the BFD traffic.
3. OSPF and BFD Behavior
When BFD is enabled for OSPFv2 or OSPFv3 on Palo Alto Networks firewalls:
- Broadcast Interfaces: BFD sessions are established only with the OSPF Designated Router (DR) and Backup Designated Router (BDR).
- Point-to-Point Interfaces: A BFD session is established with the direct OSPF neighbor.
- Point-to-Multipoint Interfaces: BFD sessions are established with each OSPF peer on that interface.
Note: BFD is not supported on OSPF or OSPFv3 virtual links.
4. Shared BFD Sessions Across Protocols
Multiple routing protocols (BGP, OSPF, RIP) can share a single BFD session on an interface if they use the same source and destination IP addresses. This resource optimization allows the firewall to support more BFD sessions overall. In such cases:
- If different BFD profiles are configured for the sharing protocols, the profile with the lowest Desired Minimum Tx Interval takes precedence.
- If profiles have the same Desired Minimum Tx Interval , the profile associated with the first BFD session created is used.
- In scenarios where a static route and OSPF share the same BFD session, the static route's BFD profile typically takes effect. This is because the BFD session for a static route is often established immediately after a configuration commit, whereas OSPF waits for adjacency formation before establishing its BFD session.
This shared session approach optimizes resource utilization, allowing the firewall to support more BFD sessions across different interfaces or IP pairs.
5. IPv4 and IPv6 Considerations
Even when using the same BFD profile, IPv4 and IPv6 on the same physical interface will always establish separate BFD sessions.
6. Interaction with HA Path Monitoring and BGP Graceful Restart
When implementing both BFD for BGP and High Availability (HA) path monitoring:
- It is generally recommended not to enable BGP Graceful Restart. BFD can detect a failure, remove affected routes from the routing table, and synchronize this change to the passive HA firewall before Graceful Restart can take effect. This can lead to BFD acting faster than Graceful Restart, potentially causing unexpected behavior if both are aggressive.
- If BFD for BGP, Graceful Restart for BGP, and HA path monitoring are all implemented, Palo Alto Networks recommends configuring BFD with a larger Desired Minimum Tx Interval and a larger Detection Time Multiplier than the default values to prevent premature route removal by BFD before Graceful Restart has a chance to maintain forwarding during a control plane restart.
7. BFD Profiles in PAN-OS
Palo Alto Networks firewalls use BFD Profiles to manage BFD settings. A default profile exists, but custom profiles allow for granular control over BFD timers and parameters.
Configuration Path:
Network > Network Profiles > BFD Profile
Key parameters in a BFD Profile include:
- Name: A unique name for the profile.
-
Mode:
Typically
Active(BFD initiates sending control packets). The default is Active. - Desired Minimum Tx Interval (ms): The minimum interval at which this firewall wishes to send BFD control packets. The default is often 1000ms. For some platforms like the PA-7000 Series, a value less than 100ms might risk BFD flaps.
- Required Minimum Rx Interval (ms): The minimum interval at which this firewall can receive BFD control packets. The default is often 1000ms.
- Detection Time Multiplier: The number of packets that can be missed before the session is declared down. Default is typically 3.
- Multihop: Enable if the BFD session is over multiple IP hops. This uses UDP port 4784.
The actual negotiated transmission interval between BFD peers will be the greater of the local Desired Minimum Tx Interval and the remote Required Minimum Rx Interval. The detection time is this negotiated interval multiplied by the detection multiplier.

Example of BFD Profile Settings in PAN-OS (Illustrative)
8. Configuring BFD on Palo Alto Networks Firewalls
Enabling BFD typically involves two main steps:
- Create a BFD Profile (Optional but Recommended): Define your desired BFD timers and mode. If no custom profile is created, the system `default` profile is used.
-
Apply the BFD Profile:
-
For Static Routes:
Navigate to
Network > Virtual Routers > [Your VR] > Static Routes > [IPv4/IPv6], select the route, and assign the BFD Profile. An interface and IP Address next-hop must be specified. -
For BGP:
Navigate to
Network > Virtual Routers > [Your VR] > BGP. BFD can be applied globally or per peer group/peer. Enabling BFD globally can cause a momentary disruption as BGP sessions are re-established. -
For OSPF:
Navigate to
Network > Virtual Routers > [Your VR] > OSPF (or OSPFv3). BFD can be applied globally or per OSPF interface within an area. -
For RIP:
Navigate to
Network > Virtual Routers > [Your VR] > RIP. BFD can be applied globally or per RIP interface.
-
For Static Routes:
Navigate to
Important: When enabling BFD for BGP, be aware that it can cause BGP sessions to flap momentarily as BFD is initiated. It's best to do this during a maintenance window. For static routes on DHCP or PPPoE interfaces, you might need two commits: one to get the IP and gateway, and a second to configure the static route with BFD using that gateway.
9. Troubleshooting BFD on Palo Alto Networks Firewalls
Troubleshooting BFD involves checking session states, timers, and counters.
Common Issues:
- Mismatched BFD Configuration: Timers or modes might not be compatible between peers.
- Firewall Policies/ACLs: Security policies on the Palo Alto Networks firewall or ACLs on intermediate devices might be blocking BFD UDP packets (ports 3784 for single-hop, 4784 for multihop, 3785 for echo).
- Underlying Link Issues: Physical layer problems or high packet loss on the link.
- Platform Limitations: Ensure the specific firewall model and PAN-OS version support BFD as configured.
- Control Plane Load: High CPU on either device could delay BFD packet processing, leading to false positives. While BFD is designed to be lightweight, extreme conditions can affect it.
PAN-OS CLI Commands:
Here are some essential CLI commands for BFD troubleshooting:
-
show routing bfd session all: Displays the status of all BFD sessions, including state, local/remote discriminators, and timers. This is a primary command. -
show routing bfd session interface: Shows BFD sessions specific to an interface. -
show routing bfd details session-id: Provides detailed information for a specific BFD session ID. -
show routing bfd active-profile [: Displays active BFD profiles.] -
show routing bfd drop-counters session-id: Shows drop counters for a BFD session. -
show counter global | match bfd: Displays global counters related to BFD, including transmit, receive, and error packets. -
clear routing bfd counters session-id: Clears BFD packet counters. -
clear routing bfd session-state session-id: Clears BFD sessions, useful for debugging. -
For specific protocols:
-
show routing protocol bgp peer bfd-status peer-name(or similar for peer group) -
show routing protocol ospf interfacebfd-status
-
Total BFD sessions: 1
Session ID: 1025 Virtual Router: default Interface: ethernet1/1 Peer IP: 192.168.1.2 Local IP: 192.168.1.1 Status: Up Client: Static Route Profile: bfd-profile-aggressive Type: Single Hop Version: 1 My Discriminator: 1025 Peer Discriminator: 2049 Desired Min Tx Interval: 100 ms Required Min Rx Interval: 100 ms Detection Time Multiplier: 3 Negotiated Tx Interval: 100 ms Echo Active: No Demand Active: No Authentication: None Uptime: 0 days, 00:10:35 Last Down: N/A Packets In: 635 Packets Out: 636
Illustrative output of
show routing bfd session all
Checking Logs:
Review system logs (
Monitor > Logs > System
) and routing logs for any BFD-related messages or errors. For more detailed debugging, you might need to use debug commands (e.g.,
debug routing bfd ...
), but these should be used cautiously in production environments as they can generate significant output.
10. Other Important Information
BFD and Link Aggregation Groups (LAGs)
BFD can be used to monitor the liveness of member links within a LAG or the LAG interface itself, depending on the vendor implementation and configuration. This ensures faster failover if a LAG member or the entire bundle goes down.
BFD and ECMP (Equal Cost Multi-Path)
When BFD is used with ECMP, it can quickly detect the failure of one of the ECMP paths. This allows the routing protocol to rapidly remove the failed path from the ECMP set, ensuring traffic is only forwarded over healthy paths.
11. BFD Best Practices
- Test Thoroughly: Before deploying BFD in a production network, test its behavior, especially failover times, in a lab environment that mimics your production setup.
-
Timer Tuning:
- Avoid overly aggressive timers (very low Tx/Rx intervals and small multipliers) unless absolutely necessary and tested. Aggressive timers can lead to false positives and session flaps on less stable links or during periods of high control plane load.
- Start with conservative timers (e.g., defaults provided by Palo Alto Networks, like 1000ms intervals with a multiplier of 3) and adjust gradually based on application requirements and network stability.
- Ensure BFD timers are consistent or compatible between peers.
- Consider Platform Capabilities: Be aware of the maximum number of BFD sessions supported by your firewall model and any platform-specific recommendations for timer values.
- Monitor BFD Sessions: Regularly monitor the state and statistics of BFD sessions to proactively identify potential issues.
- Security Policies: Ensure that your security policies permit BFD traffic (UDP ports 3784, 4784, 3785) between the BFD peers.
- Graceful Restart Interaction: Carefully consider the interaction with BGP Graceful Restart. In many cases, BFD's faster detection is preferred, and Graceful Restart might be disabled or its timers made less aggressive if BFD is used.
- Use BFD Profiles: Utilize BFD profiles for consistent and manageable BFD configurations across multiple routes or protocol instances.
Conclusion
Bidirectional Forwarding Detection is a critical protocol for modern networks requiring fast convergence. Palo Alto Networks firewalls provide robust BFD support for static routes and key dynamic routing protocols like BGP, OSPF, and RIP. Understanding its configuration, operational nuances, interactions with other features like HA and Graceful Restart, and troubleshooting techniques is essential for network engineers, particularly those preparing for the PCNSE certification. By implementing BFD correctly, organizations can significantly improve network resiliency and minimize downtime.