Introducing AI Access Security
PCNSE/PCNSA Focus: Understand the fundamental purpose of AI Access Security, the problems it solves (data leakage, shadow AI), and its core pillars (Identify/Control, Visibility/Reporting, Data Protection). Know the supported platforms and licensing models.
Generative AI (GenAI) applications are AI apps capable of generating text, images, videos, and other data in response to user prompts, continuously learning from inputs. While offering opportunities, their usage presents new security dangers: ensuring employees don't expose sensitive or proprietary data to GenAI apps.
Palo Alto Networks introduced AI Access Security to enable businesses to safely adopt GenAI apps by mitigating risks associated with data leakage in prompts and malicious content in responses. It includes:
- An extensive dictionary of GenAI apps to identify usage.
- Contextual, fine-grained access control policy rules to prevent exfiltration of sensitive data .
- Detailed monitoring capabilities to filter usage by apps, users, and use cases, enabling targeted policy rule creation .
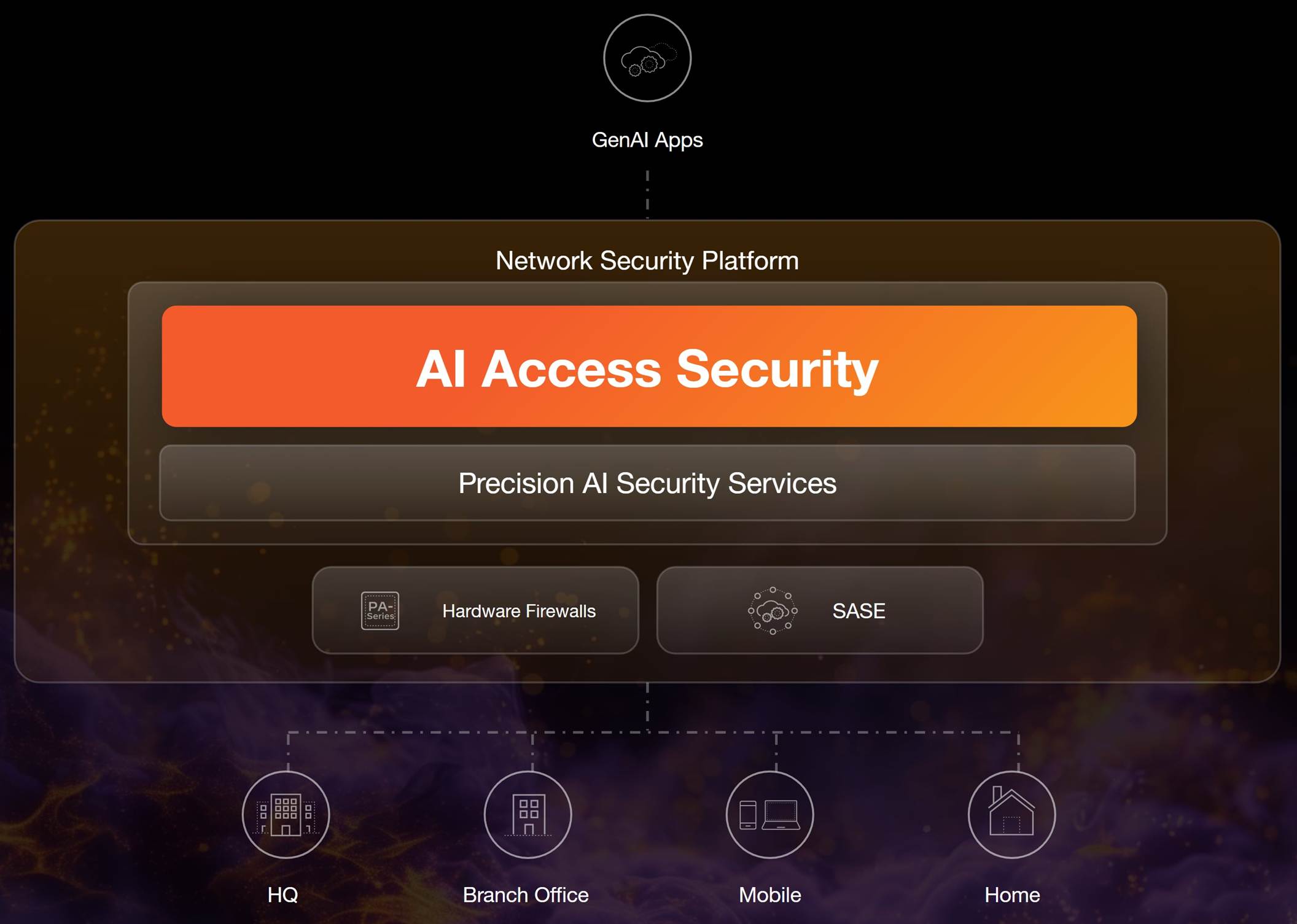
AI Access Security follows core principles for safe GenAI leverage:
- Identify and Control GenAI Apps: Provides visibility into usage, bespoke risk scores, and policy enforcement for sanctioned and shadow AI apps.
- Comprehensive Visualization and Reporting: Managed via Strata Cloud Manager for unified visibility, with detailed dashboards on usage trends, users, data transfers, and use cases.
- Data Protection: Integrates with Enterprise DLP for sensitive data exfiltration prevention and inspects GenAI responses for threats.
Identify and Control GenAI Apps
Provides robust tools to identify and control GenAI app usage.
- Attributes: Detailed descriptions and attributes used for calculating risk scores.
- Access Control: Create Internet Access policy rules to control access based on user groups, app categories, risk, use case, or even specific functions within an app. Control access for browser extensions, plugins, and custom GPTs.
- Enterprise Accounts and Custom GenAI Apps: Sanction enterprise account usage while blocking public access, or control access for custom apps with outbound internet access.
PCNSE/PCNSA Focus: Understand how AI Access Security identifies GenAI apps (dynamic content updates, ACE) and the methods available for controlling access (policy rules, attributes, user groups, functions).
Comprehensive Visualization and Reporting
Managed on Strata Cloud Manager for a single pane of glass experience.
- Detailed dashboard with trends filterable by users, data transfers, GenAI apps, and use cases.
- Comprehensive dictionary of over 500 GenAI apps and 60+ attributes for accurate discovery and monitoring.
- Context-aware LLM-powered data classification with over 300 classifiers for accurate sensitive data discovery.
- Support for persona-based access with role-based access controls.
PCNSE/PCNSA Focus: Know that Strata Cloud Manager is the primary management interface and the types of visibility provided (dashboards, user activity, app dictionary, reports).
Data Protection
Provides data protection, posture management, and zero trust security.
- Enterprise DLP: Cloud-based data loss prevention service using AI/ML. It is the detection engine for AI Access Security, blocking sensitive data exfiltration for file/nonfile traffic and text prompts.
- Uses DLP data patterns and data profiles to define sensitive data match criteria. Can use predefined or custom patterns (PII, source code, etc.).
- Threat Inspection: Inspects responses from sanctioned/tolerated GenAI apps for malicious content (files, URLs, code snippets).
PCNSE/PCNSA Focus: Understand the critical role of Enterprise DLP in AI Access Security's data protection. Know that it uses data patterns and profiles and can inspect both prompts (exfiltration) and responses (threats).
What's Supported with AI Access Security?
PCNSE/PCNSA Focus: Understand the prerequisites for using AI Access Security features, especially minimum PAN-OS/dataplane versions and required plugins/services (E-DLP, Cloud Services Plugin, Strata Logging Service). Know the different GenAI app use cases and associated risks.
Gotcha: Not all GenAI apps are supported by Enterprise DLP for sensitive data inspection. Know how to identify which ones are and the fallback (blocking access).
AI Access Security gives you visibility into hundreds of generative AI (GenAI) apps grouped into predefined Use Cases .
Traffic for these apps is visible in the Activity Insights dashboard.
Enterprise Data Loss Prevention (E-DLP) powers sensitive data prevention for supported GenAI apps. Prerequisites for using Enterprise DLP with GenAI apps:
- All GenAI app support requires PAN-OS 10.2.3 or later (NGFW, Panorama, Prisma Access dataplane).
- All GenAI apps support only nonfile inspection unless otherwise specified.
If E-DLP doesn't support a GenAI app, you can block access to it via policy rules if it's not sanctioned.
Use Cases
Safely adopt GenAI apps based on predefined use cases and associated risks.
- Audio Generators: Create audio from text/audio inputs. Risks: Copyright, Data Privacy (voice), Sensitive Data Exposure.
- Conversational Agent: Chatbots for tasks (text/file input). Risks: Malicious Prompting (data exfiltration), Sensitive Data Exposure, Insecure Plugin Configurations, Hallucinations/Bias.
- Code Assistants & Generators: Generate code snippets/suggestions. Risks: Security Vulnerabilities, Intellectual Property Violations (copyrighted code), Sensitive Data Exposure (proprietary algorithms).
- Developer Platforms: Streamline GenAI app building. Risks: Exposure of Sensitive Information (training with proprietary data).
- Enterprise Searches: Centralized search across organizational data. Risks: Data Privacy/Security (access to sensitive data), Malicious Prompting.
- Image Editor & Generators: Generate/manipulate images from text/image input. Risks: Copyright Infringement, Deepfake Misuse, Bias/Ethical Concerns.
- Meeting Assistants: Summarize meetings, generate action items. Risks: Privacy/Confidentiality Breaches (training on sensitive meeting data).
- Productivity Assistants: Task assistance in productivity tools. Risks: Data Privacy/Security (access to broad sensitive data), Excessive Agency (plugin risks), Malicious Prompting.
- Video Editors & Generators: Generate/manipulate videos from text/image input. Risks: Copyright Infringement, Deepfake Misuse, Bias/Ethical Concerns.
- Writing Assistants: Writing suggestions, grammar, content generation. Risks: Plagiarism/Copyright Infringement, Exposure of Sensitive Information, Bias/Ethical Concerns.
PCNSE/PCNSA Focus: Be able to identify key risks associated with different categories (use cases) of GenAI applications. This is often tested in scenario-based questions.
SaaS Security Integration
PCNSE/PCNSA Focus: Understand how AI Access Security leverages other SaaS Security components (Inline, Data Security, SSPM) for comprehensive protection and visibility across SaaS apps, not just GenAI.
SaaS Security (Inline, Data Security, SSPM) provides an integrated CASB solution.
- Data Security: Visibility and control of data-at-rest in sanctioned SaaS apps like ChatGPT Enterprise. View sensitive assets in the Activity Insights dashboard or Data Security > Data Assets, filtering by Sensitive Asset and Application.
- SaaS Security Inline: Visibility into GenAI Apps traffic . Review GenAI apps and attributes in the Application Dictionary, filtering by "GenAI Applications".
- SaaS Security Posture Management (SSPM): Visibility into third-party GenAI plugins from app marketplaces. View in the Plugins widget or SSPM > 3rd Party Plugins, filtering by "GenAI Applications".
AI Access Security Setup Prerequisites
PCNSE/PCNSA Focus: Critical section! Memorize the minimum PAN-OS versions, required plugins (E-DLP, Cloud Services), and logging service (Strata Logging Service) for *both* AI Access Security only AND CASB-PA/X scenarios, and across Panorama/Strata Cloud Manager management. Understand the implications of different licenses on included functionality.
Gotcha: The minimum PAN-OS/Dataplane version varies depending on which license you have (AI Access Security vs. CASB-PA/X) and the management method (Panorama vs. Strata Cloud Manager) AND the Prisma Access version (Preferred vs. Innovation). Pay close attention to these details.
Review the minimum PAN-OS and Prisma Access dataplane versions, and additional services required.
Functionality depends on licenses and PAN-OS/dataplane versions. Refer to the AI Access Security Licenses section for more details on included functionality.
NGFW and Prisma Access (Managed by Panorama)
Prerequisites when managed by Panorama.
| Prerequisite | AI Access Security License | CASB-PA and CASB-X Licenses |
|---|---|---|
| PAN-OS or dataplane | PAN-OS 11.2.2-h1 |
|
| Data Filtering | Enterprise DLP plugin 5.0.4 or later | Review Compatibility Matrix for supported Enterprise DLP plugin versions. |
| AI Access Security includes Enterprise DLP when you activate AI Access Security, CASB-PA, and CASB-X licenses. | ||
| Cloud Services Plugin | Cloud Services plugin 5.1 | |
| Logging | Strata Logging Service | |
NGFW and Prisma Access (Managed by Strata Cloud Manager)
PCNSE/PCNSA Focus: Note the slight differences in prerequisites when managed by Strata Cloud Manager vs. Panorama (e.g., no separate Cloud Services plugin mention explicitly for Strata Cloud Manager in the table, but it's integrated).
Prerequisites when managed by Strata Cloud Manager.
| Prerequisite | AI Access Security License | CASB-PA and CASB-X Licenses |
|---|---|---|
| PAN-OS or dataplane | PAN-OS 11.2.2-h1 |
|
| Data Filtering | AI Access Security includes Enterprise DLP when you activate AI Access Security, CASB-PA, and CASB-X licenses. | |
| Logging | Strata Logging Service | |
AI Access Security Licenses
PCNSE/PCNSA Focus: Know the different license types (AI Access Security, CASB-PA, CASB-X) and which ones include AI Access Security functionality. Understand the basic differences between AI Access Security only vs. having CASB-PA/X active, especially regarding DLP scope and visibility.
Gotcha: The scope of DLP inspection for non-GenAI apps depends on whether you *only* have the AI Access Security license or also have Enterprise DLP or CASB-PA/X licenses active.
AI Access Security can be used with NGFW and Prisma Access , managed by Panorama or Strata Cloud Manager .
Requires one of the following licenses: AI Access Security , CASB-PA , or CASB-X .
AI Access Security License
A standalone license with three types:
- AI Access Security EVAL: Evaluation license. Must convert to production after evaluation to continue.
- AI Access Security LAB: For lab environments only. Not intended for production.
- AI Access Security: Production license.
CASB-PA and CASB-X
AI Access Security is included by default with CASB-PA and CASB-X licenses. No additional action needed for activation if CASB-PA or CASB-X is active.
What's Included with an AI Access Security License?
Included functionality depends on other active licenses and the PAN-OS/dataplane version (refer to Setup Prerequisites ).
AI Access Security only
When only the AI Access Security license is active (on NGFW/Prisma Access managed by Panorama or Strata Cloud Manager).
| PAN-OS or Dataplane Version | NGFW and Prisma Access (Managed by Panorama or Strata Cloud Manager) |
|---|---|
|
11.2.2-h1 and later
Prisma Access 5.1 Innovation |
|
AI Access Security and Enterprise DLP Licenses
When both AI Access Security and Enterprise DLP licenses are active (on NGFW/Prisma Access managed by Panorama or Strata Cloud Manager).
PCNSE/PCNSA Focus: Notice the difference here compared to "AI Access Security only" - Enterprise DLP inspection now applies to *both* GenAI and non-GenAI apps.
| PAN-OS or Dataplane Version | NGFW and Prisma Access (Managed by Panorama or Strata Cloud Manager) |
|---|---|
|
11.2.2-h1 and later
Prisma Access 5.1 Innovation |
|
CASB-PA and CASB-X Licenses
When CASB-PA or CASB-X licenses are active (on NGFW/Prisma Access managed by Strata Cloud Manager). Note: Functionality is the same across listed versions.
PCNSE/PCNSA Focus: Know that CASB-PA/X provides broader visibility and reporting capabilities across *all* SaaS Inline apps, not just GenAI apps, compared to having only the AI Access Security license.
| PAN-OS or Dataplane Version | CASB-PA and CASB-X |
|---|---|
|
10.2, 11.1, 11.2.2-h1+
Prisma Access 5.0/5.1 (Preferred & Innovation depending on version) |
|
Activate the AI Access Security License
PCNSE/PCNSA Focus: Understand the general activation process using the magic link via CSP. Know the role of CSP and Multitenancy (TSGs). Understand that activating CASB-PA/X includes AI Access Security automatically. Be aware of the prerequisites that must be met *before* activation (PAN-OS, management setup, E-DLP setup).
Gotcha: Activating AI Access Security requires a valid CSP account matching the email that received the magic link. Multitenancy adds steps for selecting the correct account and TSG.
Activate your AI Access Security license using a magic link from Palo Alto Networks after purchase.
AI Access Security is included automatically when you activate a CASB-PA or CASB-X license.
These procedures assume you have license auth codes and magic links, and that prerequisites are met (minimum PAN-OS, management setup, E-DLP setup).
New Deployments (Prerequisites)
Steps required before activating the AI Access Security license on a new deployment:
- Install and perform initial configuration for your NGFW , including activating support licenses.
-
Set up management for your NGFW or Prisma Access tenant (Panorama or Strata Cloud Manager). This involves:
- Setting up Panorama (M-Series or Virtual Appliance).
- Deploying Strata Logging Service .
- Registering Panorama and activating Panorama support/management licenses.
- Adding managed firewalls to Panorama.
- Upgrading Panorama and NGFW to minimum PAN-OS versions.
- Installing Cloud Services plugin on Panorama (for Prisma Access).
- Setting up Panorama Managed Prisma Access (for Prisma Access).
- OR Activating AIOps for NGFW Premium license (for Strata Cloud Manager managed NGFW).
- OR Activating Prisma Access license on Strata Cloud Manager (for Strata Cloud Manager managed Prisma Access).
- Onboarding NGFW to Strata Cloud Manager (if applicable).
- Installing latest dynamic content updates and upgrading NGFW to minimum PAN-OS (if SCM managed).
- Setting up Prisma Access (if SCM managed).
-
Set up
Enterprise Data Loss Prevention (E-DLP)
. This involves:
- Installing the E-DLP plugin (Panorama) or Enabling E-DLP (SCM).
- Editing E-DLP cloud content, data filtering, and snippet settings.
- Reviewing supported advanced detection methods.
- Creating data patterns and data profiles (recommend advanced profiles).
- Modifying the DLP Rule (Strata Cloud Manager only).
Activation Steps (New or Existing Deployments)
Procedure after prerequisites are met:
- Click the magic link provided by Palo Alto Networks.
- Click Activate Subscription .
-
Enter your
Palo Alto Networks Customer Support Portal (CSP) Email Address
. It must match the email that received the link.
- If no valid CSP account exists for the email, you can Create a New Account . This new account gets a Multitenant Superuser role and is associated with the tenant.
- ( Multitenancy only ) Select the Customer Support Account.
- ( Multitenancy only ) Select the tenant service group (TSG) for activation (parent or child tenant). Activation is for the selected tenant *only*.
- Review the tenant Region (pre-populated and cannot be changed).
- In the Assign Licenses section, click Done . Verify AI Access Security License is Fully Assigned .
-
Verify your
Data Loss Prevention
instance is selected if E-DLP is already active.
- Gotcha: E-DLP is *not* required for AI Access Security activation itself. If E-DLP isn't active, one is created during activation. If you don't renew the AI Access Security license, E-DLP is no longer accessible and traffic isn't forwarded for inspection.
- Agree to the Terms and Conditions.
- Activate .
You are redirected to the Tenant Management page. The AI Access Security Activation Status starts Initializing . It displays as Data Security with a serial number starting with AIX . Proceed after status is Complete .
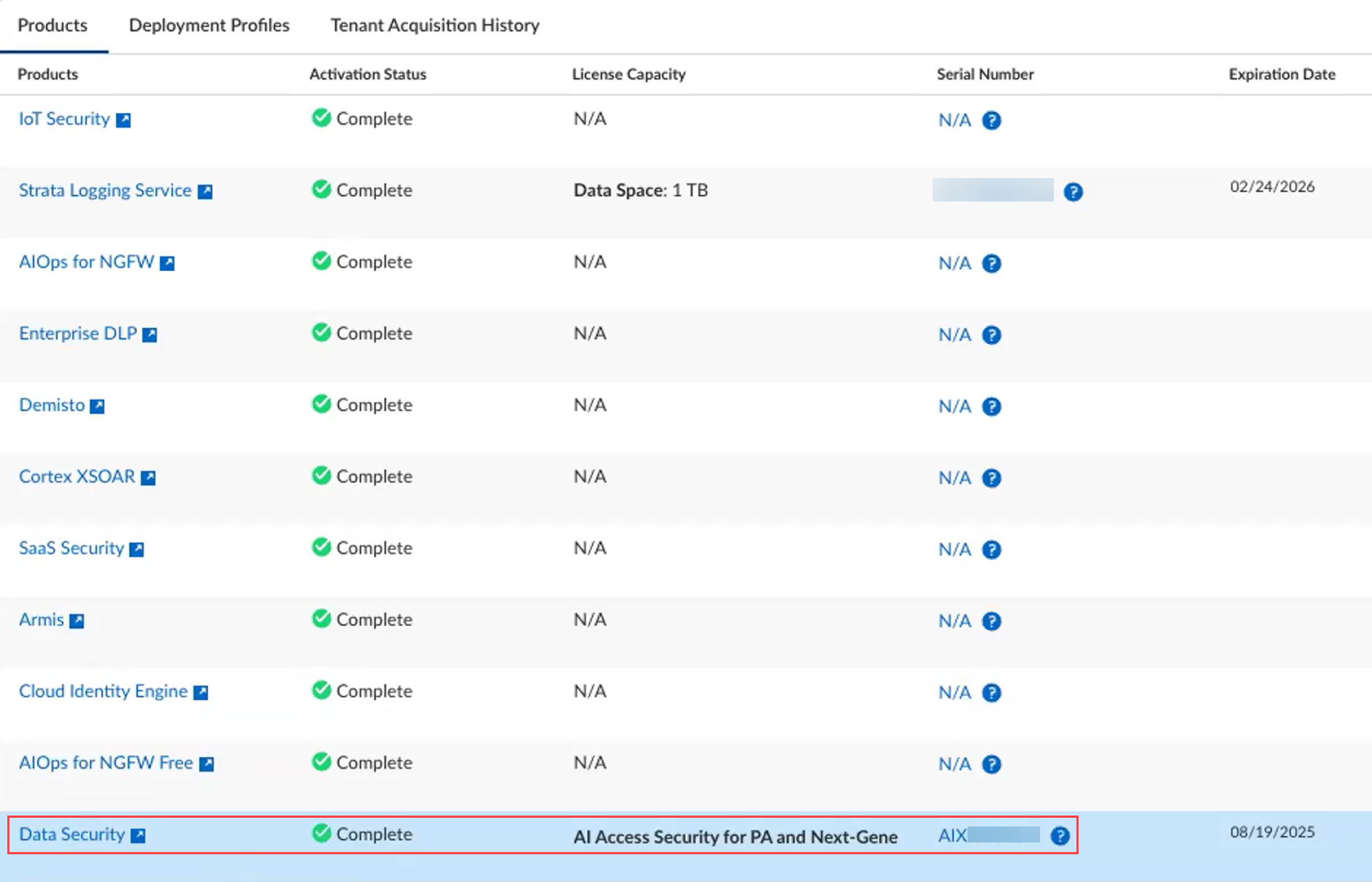
- ( NGFW only ) Associate the AI Access Security license with your NGFW in Strata Cloud Manager (Settings > Device Associations > Associate Apps > Data Security > Select NGFW > Save). This is required for NGFW activation.
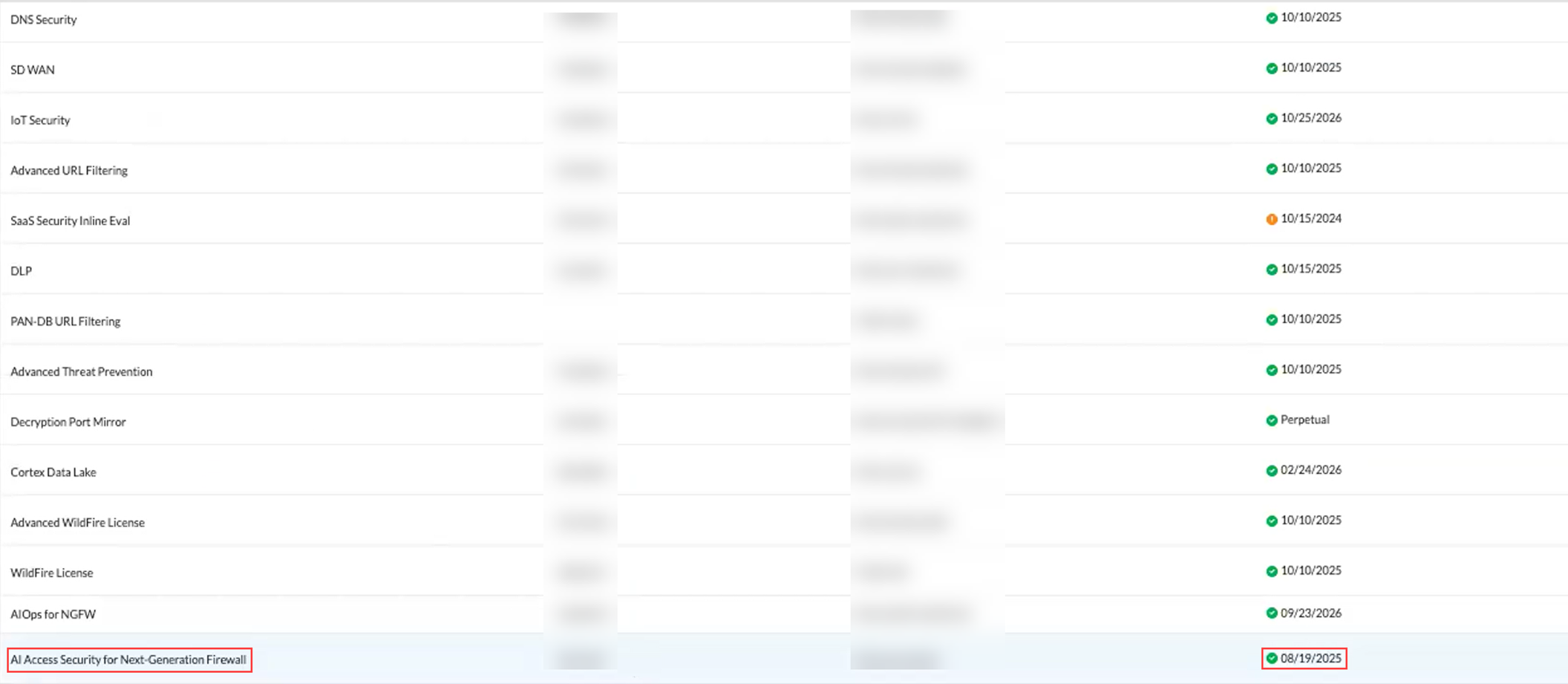
- Verify activation in CSP (Products > Assets > Select NGFW or Prisma Access tenant > Licenses & Subscriptions). Verify the AI Access Security license is active.
- Get Started with AI Access Security.
Convert an AI Access Security Evaluation License to a Production License
PCNSE/PCNSA Focus: Understand the process for converting an EVAL license and the consequences of *not* converting it after the evaluation period (loss of E-DLP functionality/access).
Gotcha: Failure to convert means E-DLP stops working for *all* traffic, not just GenAI, even though the policy rules are preserved.
If you have the AI Access Security EVAL license active, you must convert it to production to continue safely controlling access and adopting GenAI apps after the evaluation period ends.
If you don't convert:
- Traffic containing sensitive data is no longer forwarded to Enterprise DLP for inspection/verdict.
- Enterprise DLP is no longer accessible (via Panorama or Strata Cloud Manager).
- Web Security and Security policy rules created for AI Access Security are preserved .
Procedure:
- Log in to Strata Cloud Manager .
- In the SCM menu (bottom-left), select Settings > Subscriptions .
- Find the AI Access Security evaluation license and select Actions > Eval to Prod Request .
-
Specify the production license terms:
- License Quantity: Number of individuals using AI Access Security.
- Term: Length of subscription.
- Send Request .
Renew an AI Access Security License
PCNSE/PCNSA Focus: Know that AI Access Security licenses require manual renewal and the specific consequences if they expire (loss of E-DLP functionality/access).
Gotcha: Like EVAL licenses, expired production licenses result in E-DLP being inaccessible and traffic no longer being inspected for sensitive data, even if policy rules remain.
You must manually renew your expiring AI Access Security license to continue using it. It does not automatically renew .
If the AI Access Security license expires:
- Traffic containing sensitive data is no longer forwarded to Enterprise DLP for inspection/verdict.
- Enterprise DLP is no longer accessible (via Panorama or Strata Cloud Manager).
- Web Security and Security policy rules created for AI Access Security are preserved .
Procedure:
- Contact your Palo Alto Networks sales representative to request a renewal.
- Log in to Strata Cloud Manager .
- From the bottom-left menu, select Settings > Tenants .
- Select the tenant for which you're renewing the license (parent or child). Tenants requiring immediate action are marked with a blue circle.
- Edit the tenant licenses.
- Agree to the terms and conditions and Activate Now (after the renewal is processed by PANW).
Perform Initial AI Access Security Configuration
PCNSE/PCNSA Focus: Understand the essential configuration steps needed after license activation to make AI Access Security functional. This includes E-DLP setup (patterns/profiles), enabling Role-Based Access, enabling the Best Practice snippet (policy rules), associating the Tagging snippet, creating a Vulnerability Protection profile, and creating zones (for NGFW).
An initial configuration is required after license activation.
Gotcha: Simply activating the license doesn't provide protection. You *must* perform these configuration steps, especially setting up E-DLP and enabling the policy snippets.
This procedure assumes the AI Access Security license is already activated .
Initial Configuration Steps:
-
Set up and configure
Enterprise Data Loss Prevention (E-DLP)
.
- E-DLP is the detection engine. You must associate a data profile with a Security policy rule.
- Steps include: Installing/Enabling E-DLP (based on management), editing settings, reviewing advanced detection methods, creating data patterns and data profiles (advanced profiles recommended), and modifying the DLP Rule (Strata Cloud Manager only).
- Enable Role Based Access to define administrator access privileges (for AI Access Security, E-DLP, and the management interface).
-
Enable the Gen-AI-Best-Practice Snippet
.
- Provides a starting point with preconfigured Security policy rules based on best practices.
- Quickly allows Sanctioned apps and blocks many risky ones by default.
- Associated with the Global folder by default but can be reassigned.
-
Associate the Application-Tagging Snippet
.
- Required for tag-based policy rule enforcement .
- Contains info on which apps are tagged Sanctioned or Tolerated (otherwise Unsanctioned).
- Tags are read from this snippet for UI display and policy enforcement.
-
Create a
Vulnerability Protection profile
.
- Associated with Security policy rules to stop attempts to exploit system flaws.
-
(
NGFW only
) Create an internal trust zone and an outbound untrusted zone.
- Zones logically group interfaces. Policy rules use zones (source/destination) for traffic control.
- Create application filters to dynamically group GenAI apps for consistent policy application (predefined filters based on use case are included).
- Create Custom Security policy rules to refine control beyond the best-practice snippet.
Enable Role Based Access to AI Access Security
PCNSE/PCNSA Focus: Understand the predefined roles that grant access to AI Access Security and their general privilege levels (Full Read/Write, Read/Write, Read-Only). Know that custom roles are *not* supported specifically for AI Access Security access.
Gotcha: Custom roles *can* be configured in Panorama/SCM but they don't provide granular access *specific to the AI Access Security service itself*. You must use the predefined roles listed here.
Configure role-based access by assigning a predefined role to security administrators. These roles define read/write privileges for AI Access Security.
Roles and Permissions details other privileges.
Gotcha: Custom roles are not supported specifically for granting access privileges within the AI Access Security features/UI itself, although they are used for other Panorama/SCM functions.
| Predefined AI Access Security Role | Privileges |
|---|---|
| Data Security admin | Full read and write access privileges for AI Access Security. |
| Multitenant Superuser | Full read and write privileges for all available system-wide functions for all tenants in the particular multitenant hierarchy where the role is assigned. |
| Security Administrator | Read and write access for AI Access Security. |
| Superuser |
Full read and write privileges for the tenant, including AI Access Security.
(Specific to a child tenant in multitenancy, not parent or other children). |
| View Only Administrator | Read-only privileges for AI Access Security |
Procedure (Managed by Panorama or Strata Cloud Manager):
- Configure a Panorama administrator account and admin role ( account and role ) (Panorama only) OR Onboard the NGFW to Strata Cloud Manager and configure Strata Cloud Manager user roles (Strata Cloud Manager only) . This step grants access to the management interface itself.
- Enable role-based access for Enterprise Data Loss Prevention (E-DLP) . This step defines privileges for configuring E-DLP patterns/profiles. Skip if already done or not needed for this user.
-
Assign role-based access for AI Access Security
in Common Services Identity and Access Access Management:
- Select User , enter the Identity Address (email).
- For Apps & Services , select AI Access Security .
- Select a predefined Common Services Role from the table above.
- Submit .
Enable the Gen-AI-Best-Practice Snippet
PCNSE/PCNSA Focus: Understand the purpose and initial state of the Gen-AI-Best-Practice snippet (disabled by default). Know the two policy rules included and their default actions and placement in the rulebase (Sanctioned = pre-rule, Default = post-rule). Understand how enabling this snippet quickly establishes basic GenAI policy control.
Gotcha: The snippet is disabled by default after license activation. You *must* manually enable the two policy rules within it for them to take effect.
Activating AI Access Security grants access to the predefined Gen-AI-Best-Practice snippet .
This snippet provides a starting point for Security policy rules using best practices for GenAI app adoption. It allows access to Sanctioned GenAI apps and blocks many potentially risky ones by default, enabling productivity while maintaining control.
It's associated with the default Global configuration folder by default but can be reassigned.
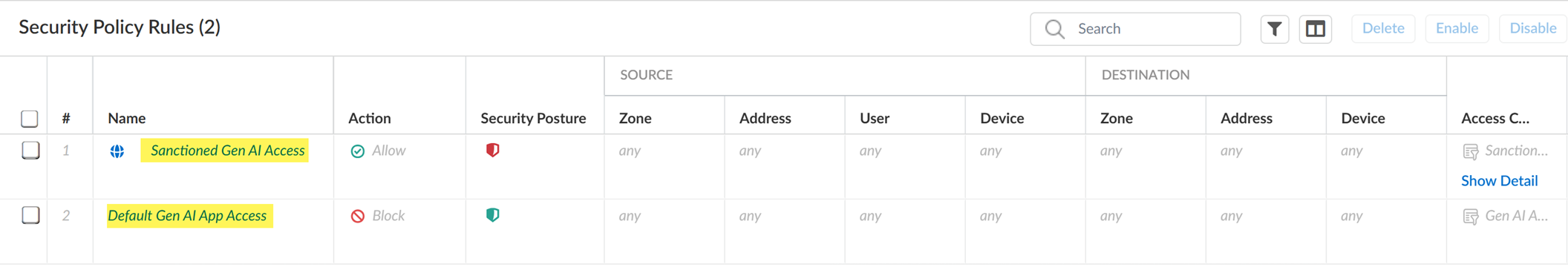
The snippet includes two key Security policy rules:
-
Sanctioned GenAI Access:
- Allows access to apps tagged as Sanctioned .
- Part of the pre-rule rulebase (takes precedence over deployment-specific/post-rules).
- Disabled by default. You must manually enable it.
- Applies the predefined Sanctioned GenAI Apps application filter.
- Applies to any source/destination/user by default.
-
Default GenAI App Access:
- Blocks access to apps not classified as Sanctioned or Tolerated , or any GenAI not explicitly allowed by higher priority rules.
- Part of the post-rule rulebase (evaluated after pre-rules and deployment-specific rules).
- Disabled by default. You must manually enable it.
- Applies the predefined GenAI Apps application filter (includes all GenAI apps).
- Applies to any source/destination/user by default.
Procedure to enable the rules:
- Log in to Strata Cloud Manager .
- Select Manage > Configuration > NGFW and Prisma Access > Security Services > Security Policy > Internet Security .
- Toggle the State column to enable (blue) for both the Sanctioned GenAI Access and Default GenAI App Access policy rules.
- ( Optional ) Create and apply Security Profiles (like a DLP rule ) to the Sanctioned GenAI Access policy rule to prevent sensitive data exfiltration for allowed apps. Use Recommendations to identify gaps.
Associate the Application-Tagging Snippet
PCNSE/PCNSA Focus: Understand the purpose of the Application-Tagging snippet (supports tag-based policy enforcement). Know that it must be associated with the correct scope(s) and that those scopes must have ACE enabled. Understand the importance of managing tags *only* within this snippet scope.
Gotcha: Tagging apps outside the Application-Tagging snippet scope or associating the snippet with scopes without ACE enabled can lead to inconsistent tags in the UI vs. what's enforced by policy, or configuration push failures.
The predefined Application-Tagging snippet in Strata Cloud Manager is required for tag-based policy rule enforcement .
It contains tagging information (Sanctioned, Tolerated, Unsanctioned) for GenAI apps. Tags are written to and read from this snippet for display in the UI (AI Access Security, Activity Insights, Command Center) and for policy evaluation.
Re-tagging apps (based on risk, etc.) updates this snippet. Pushing configuration applies these new tags to the NGFW/Prisma Access deployment, affecting tag-based rules.
To push tags, the snippet must be associated with the appropriate scope(s). Associate the snippet ONLY with NGFWs or Prisma Access deployments that have App-ID Cloud Engine (ACE) enabled .
Gotcha: The Application-Tagging snippet uses ACE App-IDs. If the NGFW/Prisma Access isn't configured to receive App-IDs from ACE, the configuration push will fail.
Procedure:
- Log in to Strata Cloud Manager .
-
(
Important if you tagged apps before Sept 2024 update
)
Remove existing Sanctioned and Tolerated app tags from all Configuration Scopes *other than* the Application-Tagging snippet scope
.
- Navigate to Manage > Configuration > NGFW and Prisma Access > Objects > Application > Applications .
- Change Configuration Scope to where you previously managed tags.
- Select tagged apps (use filters).
- Remove Tag (removes admin-added tags, not predefined ones).
- Repeat for all relevant scopes.
Gotcha: Old tags outside the Application-Tagging snippet scope can still affect policy enforcement based on evaluation order, leading to unexpected behavior. Remove them to ensure the snippet's tags are authoritative.
- Select Manage > Configuration > NGFW and Prisma Access > Overview .
- Select Configuration Scope > Snippets > Application-Tagging .
- In the Snippet Associations area, click the settings gear icon.
- Select the scopes to associate with the Application-Tagging snippet. Ensure selected scopes have ACE enabled .
If you tag apps from the Applications page in Strata Cloud Manager ( Manage > Configuration > NGFW and Prisma Access > Objects > Application > Applications ), make sure the Configuration Scope is set to the Application-Tagging snippet .
Tagging to the Application-Tagging scope is important:
- Tags displayed in UI (AI Access Security, Activity Insights, Command Center) are read from this snippet. Tagging elsewhere leads to UI/Policy inconsistency.
- Tag-based policy enforcement uses an evaluation order. Tagging in multiple scopes can cause unexpected policy behavior.