Cloud Identity Engine Directory Sync
Intro
hi my name is rob ringer and today i'm going to be going over the directory sync portion of palo alto numbers cloud identity engine so with the growing list there's five different ways to connect to your
identity providers today and instead of making five different videos i've decided to create a single one-stop shop for you so at any time if you need to skip ahead i'll have links down below different time stamps to each of the identity providers but feel free to watch it all i'm sure you'll learn something get something out of it and i'm definitely awesome to listen to
so at the very end you'll be able to get an actual walkthrough of how to apply it to your panorama instance as well as to your palo alto network's uh cloud services such as a managed prisma access

so with that the agenda today i'm going to go over what cloud identity engine is what identity looks like in the enterprise today any dependencies that we have then we're going to get down into it right i'm going to help you walk through building out your cloud identity engine instance and then we're actually going to go through each and every one of those five instances so it doesn't matter if it's the on-prem id doesn't matter if it's azure ad if it's the new azure skim secure cross domain identity management um apparently you can just pick and choose which characters you want in your acronym because the d is there but not
uh and then we'll move on to google workplace and finally octa
and then we'll wrap that up at the end with like doing the uh panorama and then managed uh prisma access integration
so cloud identity engine was created to help identify and verify all users across your infrastructure irrespective of what the users are on-prem cloud hybrid or multi-cloud identity provider sources
really why this was created was to help make xero trust possible one of the core tenets is to be able to have identity right so we can identify our users and our groups on our firewalls on our cloud services it doesn't matter where they are having that identity is critical and crucial for success and what palo alto networks did as you'll see is make it incredibly easy to accomplish
and so some of those key benefits are we can collect those user and group information not only from on-prem or the cloud so it doesn't matter if you're using guest accounts if you're using more than one we can bring
them all together and actually have an example that i'll show you of a cie instance that has all of them integrated and then we're able to start looking at how those sample claims are are sending back attributes so if we don't like what we're getting from those idps instead of having to troubleshoot with the different teams getting them involved elongating the process cloud identity engine can actually sit in the middle of that and remap those attributes for you so as the firewall or the service administrator you could just start troubleshooting get your eyes on it and fix the problems without having to rely on a bunch of two bunch of teams getting involved
so that is the idp portion of cie and i'll have another video covering that
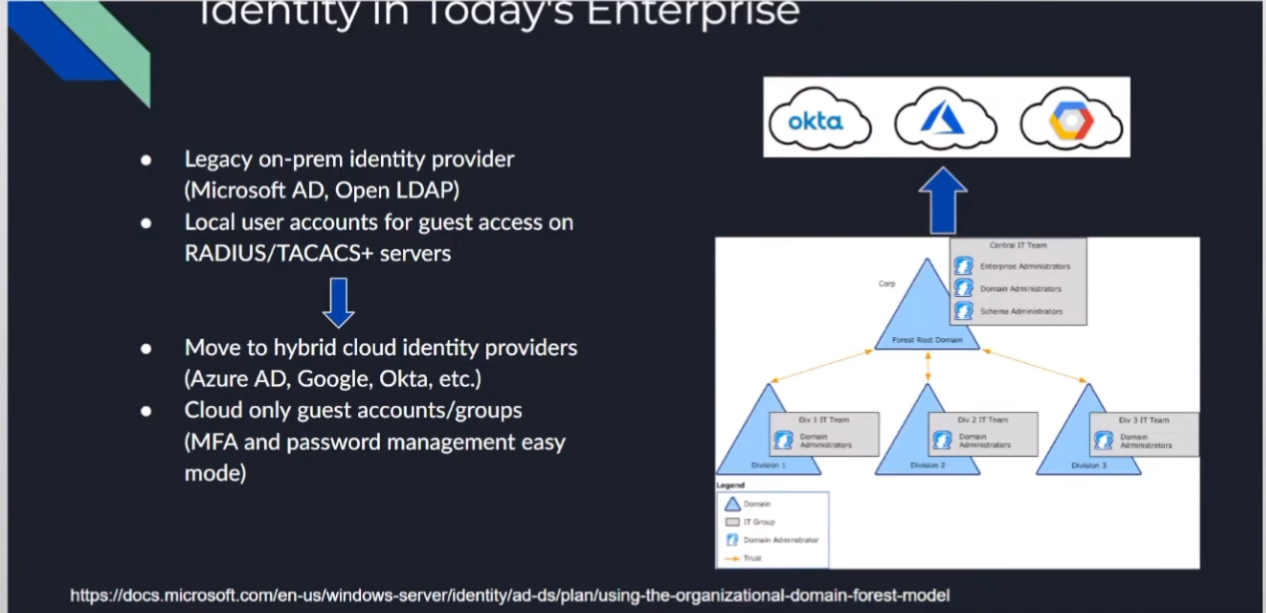
so identity today so we have our traditional ldap structure so this could be microsoft ad open ldap you name it right and it really was just creating those attributes uh so that we could have users and groups and have some sort of mapping and so this is where we were doing things like radius or tacacs or you name it to be able to query them and we're really moving those out into the cloud where a lot of our services are going
so it doesn't matter if you're doing octa or azure or google we're moving out there and a lot of the benefits are simplified mfa when we're going out there and using other protocols that are easier to implement such as sam

so the dependencies on the palo alto network side uh panos 10.1 so i'm going to be using 1015 h1 and then you'll need an active support contract as well as permissions to create an app within the palo alto networks hub
not a lot pretty easy straightforward
so we're going through each of our idps so with microsoft azure you'll need at least a free ad account
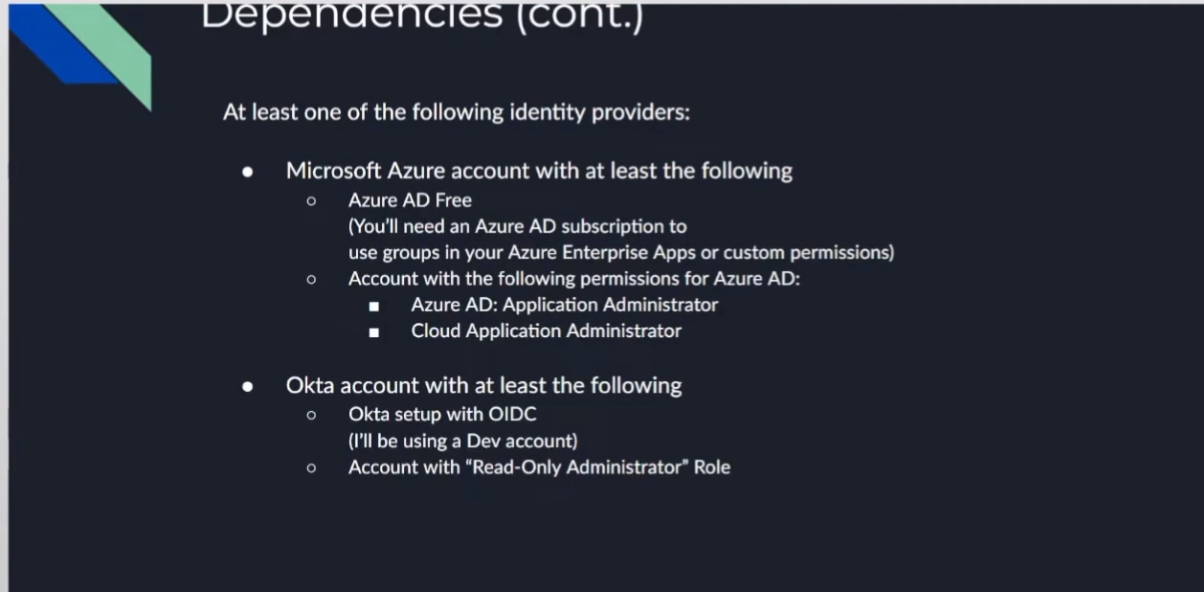
if you're going to do anything with the permissions uh you'll need a higher tier and you'll see that where you need like a p1 p2 type thing i have a screenshot of it and then you'll need if you're doing the azure ad portion of it you'll need azure id application administrator as well as cloud application administrator
with octa you'll need an account with at least one of the following noctis setup with uh oidc i'm just using a dev account there's a lot of different options with octa i'm definitely not an office specialist so get with them they'll be able to help you with it and it just needs to read only administrator rule
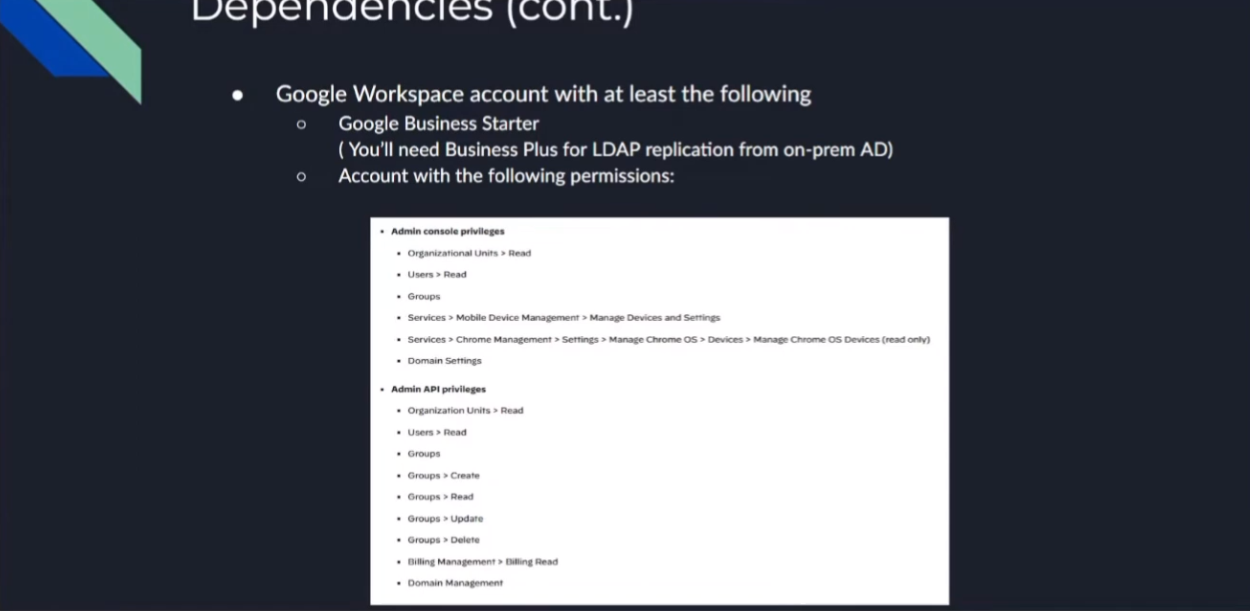
so google workspace account you'll just need the the google business starter edition and then there you'll need business plus if you're doing your ldap replication for your on-prem and then you'll need any there's 15 total permissions that you'll need i created a specific role for this that i'll show you that just captured all of them the screenshots there it only takes a couple minutes to set up it's not that big of a deal um but we'll have that information
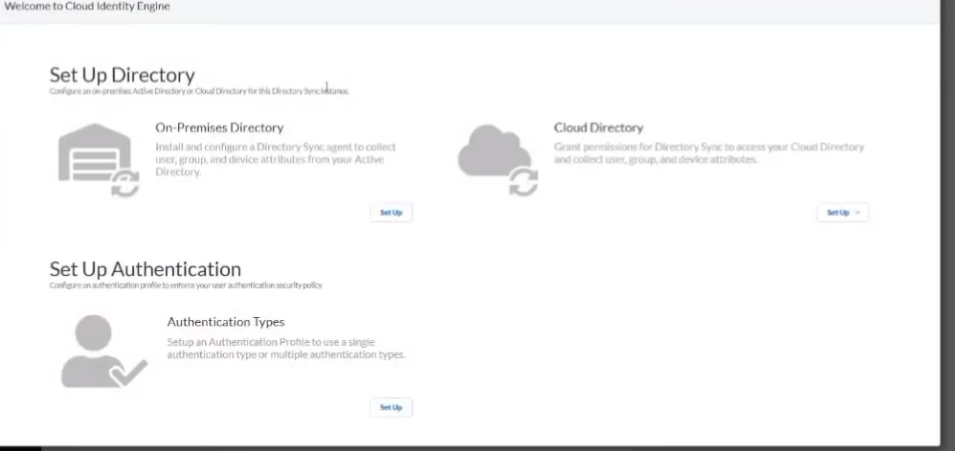
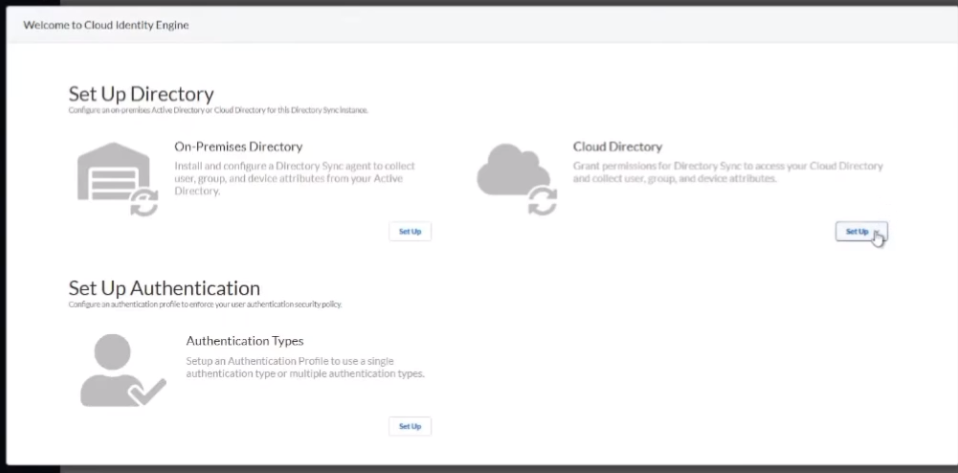
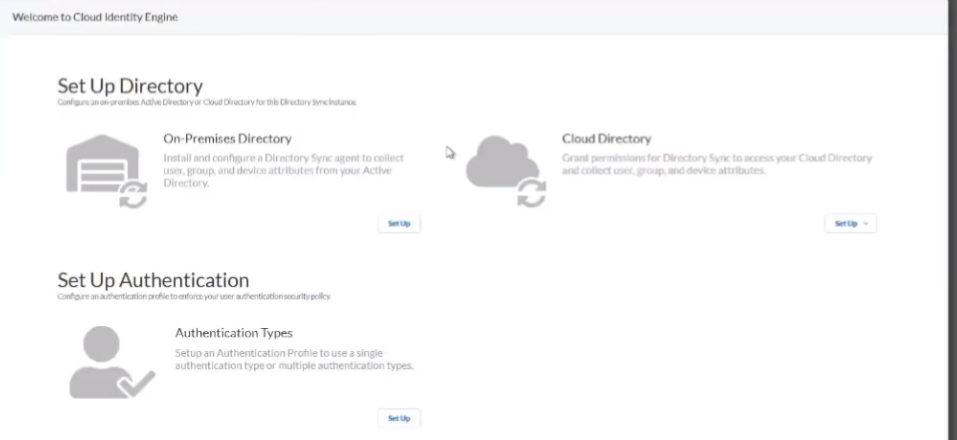
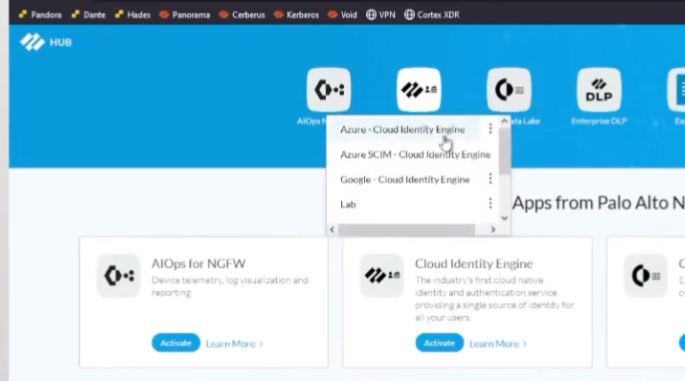
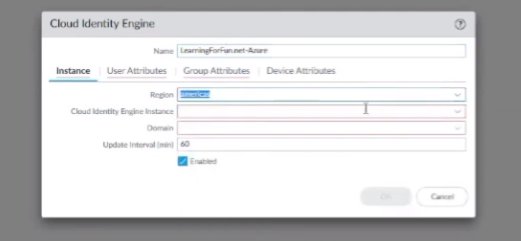
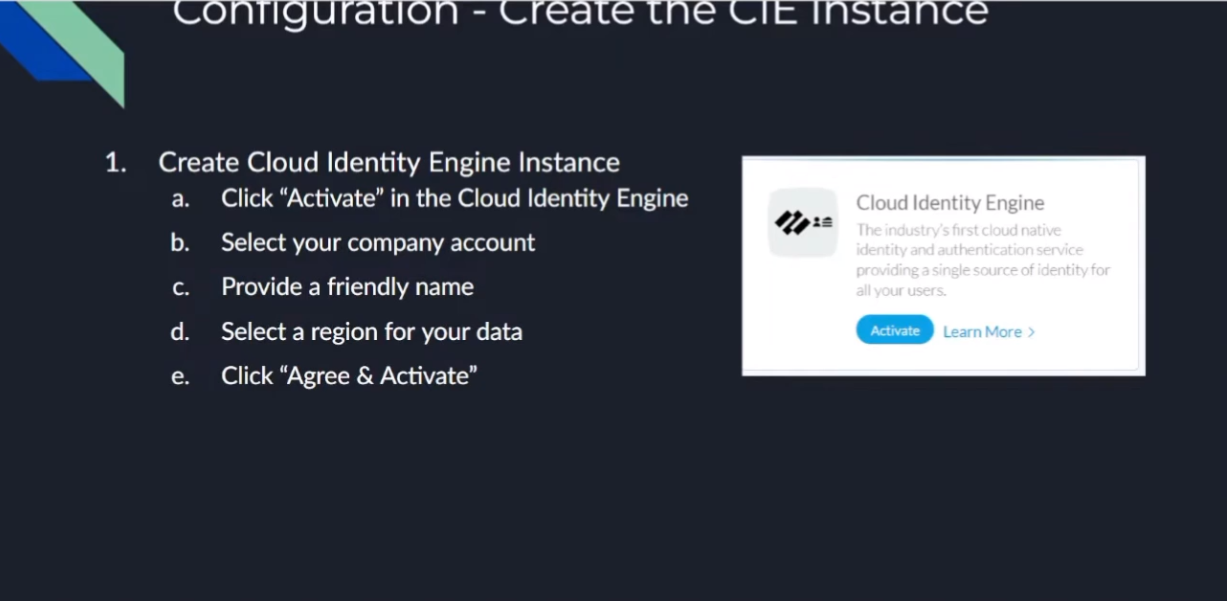 on to the good stuff creating your first uh cloud identity engine instance so it's just a couple steps you go to your hub you'll see there's a nice little button there says hey activate your cloud identity engine once you click that you're going to select the account you want it under you're going to give it a friendly name and select the region that you want your data stored so if you're in the americas you'll pick the americas or europe whatever makes sense for your data click to agree and then a couple of minutes later it's created so we're going to go ahead and walk through that right now
on to the good stuff creating your first uh cloud identity engine instance so it's just a couple steps you go to your hub you'll see there's a nice little button there says hey activate your cloud identity engine once you click that you're going to select the account you want it under you're going to give it a friendly name and select the region that you want your data stored so if you're in the americas you'll pick the americas or europe whatever makes sense for your data click to agree and then a couple of minutes later it's created so we're going to go ahead and walk through that right now
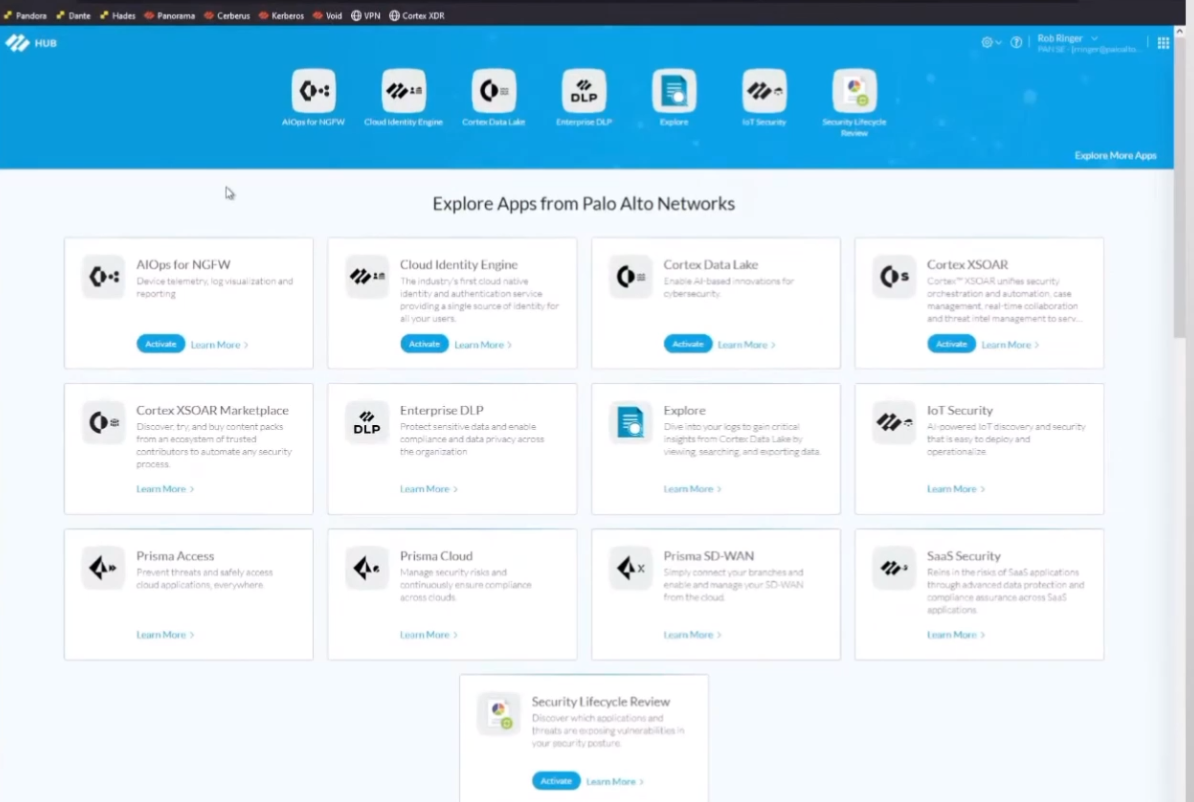
here we are all right so i'm logged into my hub and then we can see right here i have my activate cloud identity engine
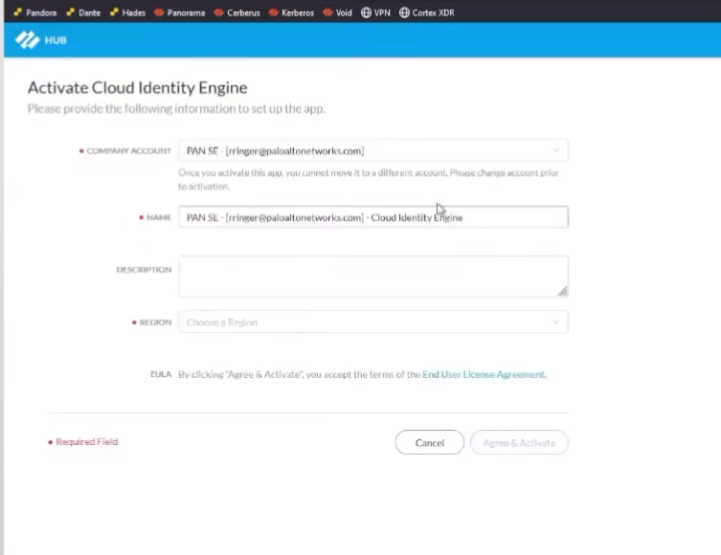
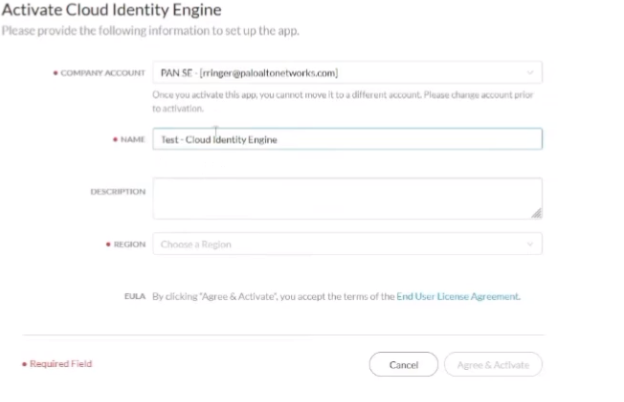
i'm gonna go ahead and do that and instead of this name here i'm just gonna call it my test cloud identity engine i have my account name i want it my company name and then under region i'm just going to select united states and agree and activate and then it's going to be activated so i can just go ahead and click back on the hub and then after i don't know a minute or two it'll show up down here under the drop down
for today i've created a different cie instance for each one of the idps that we're going to be doing as well as we can see that the test since it's already shown up there so do we just click on it to be able to enter it and then under the lab is the one where i have everything already combined to show you guys
so going back to the next step
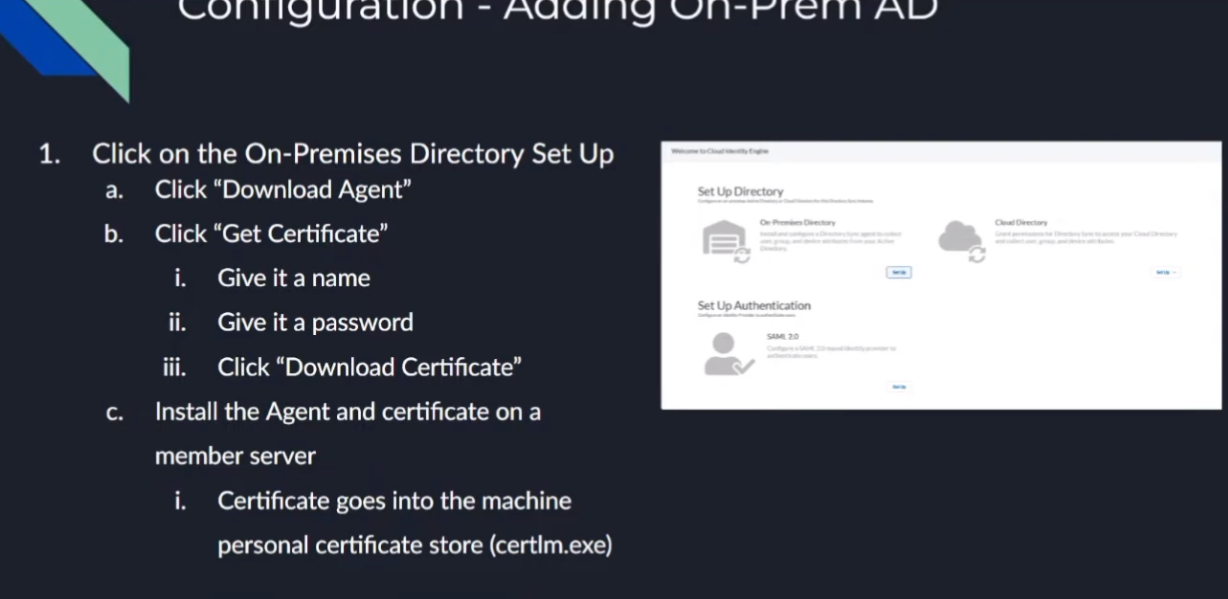
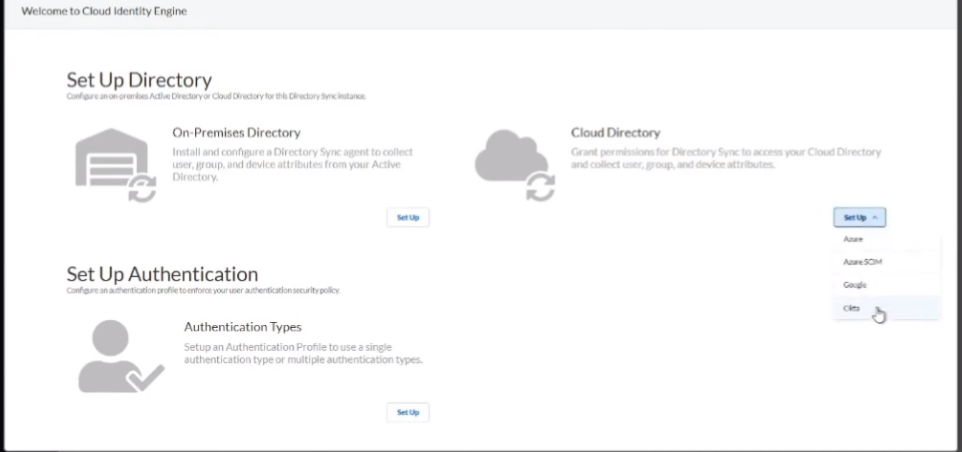
On-Prem AD
to do our on-premise ad we're just once we click into our cie instance we're going to click to set up our on-premise directory and really it's just going to have us download the agent we're going to get a certificate for the agent that allows the agent to securely communicate back up with your cie instance and identify itself so it knows where to store that data and so to do that we're just gonna give it a name and we're gonna give it a password and we're going to download it and with those two pieces of information we're going to go install it on a member server and we're going to install the certificate in your local machine personal store and to do that uh you're just going to use the utility cert lm for cert manager that you might be used to for your personal certs and that's really there all is to it once we open it up we're going to put our ldap information so that we can query ad so you'll need your bind dn your buying password the protocol l.s or ldap with start tls and then you're going to want at least two servers there's a little something called redundancy right so
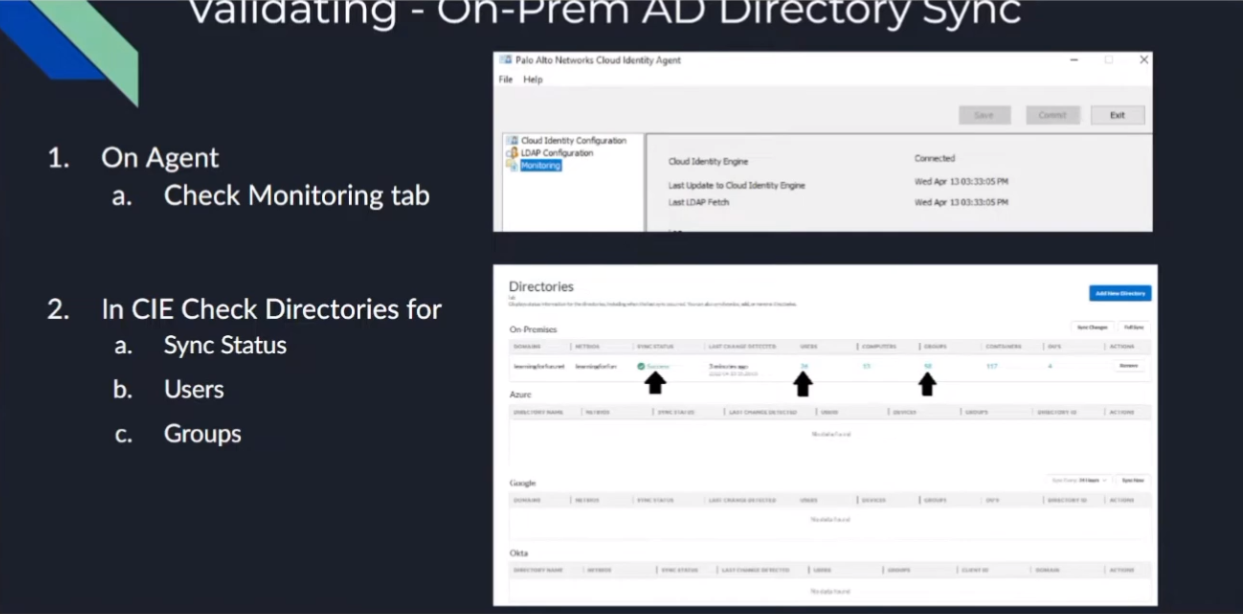
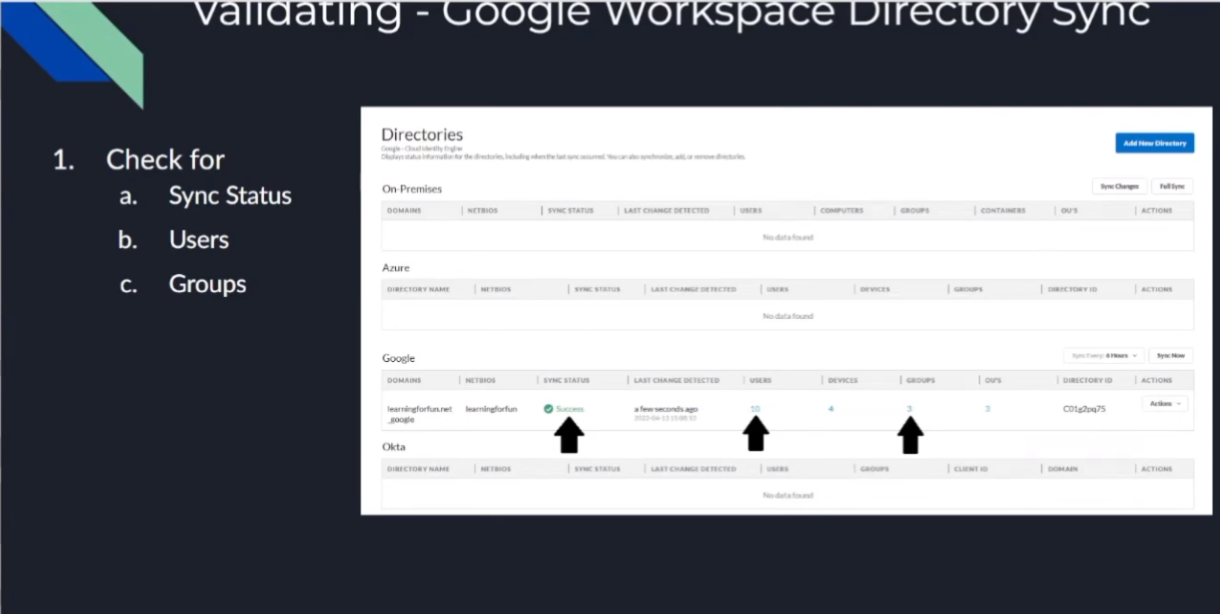
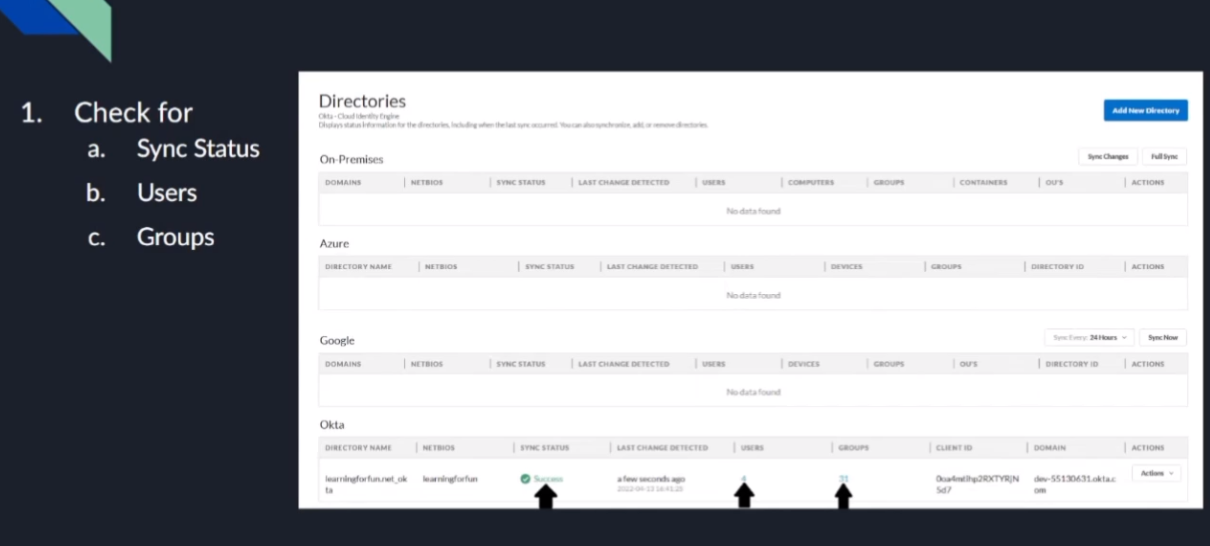
and then we're going to start the agent and after that it's going to go ahead and replicate up so um and then to validate we're going to be able to see both on the agent itself that is connected it's going to tell you the date and then on the cloud identity engine inside your instance you're going to be able to see some positive messages right you're going to see hey it's successful and then you're going to see there there was some users replicated and there were some groups those are going to change based on your environment so don't look for the exact numbers that i have on the screen because they're probably not going to match so now we're going to go ahead and do a walkthrough of that
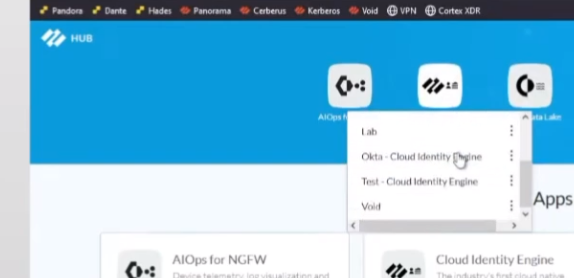
all right so we're going to go ahead into the seat here best one so i go into it i'm going to set up the directory i'm going to click to download the agent
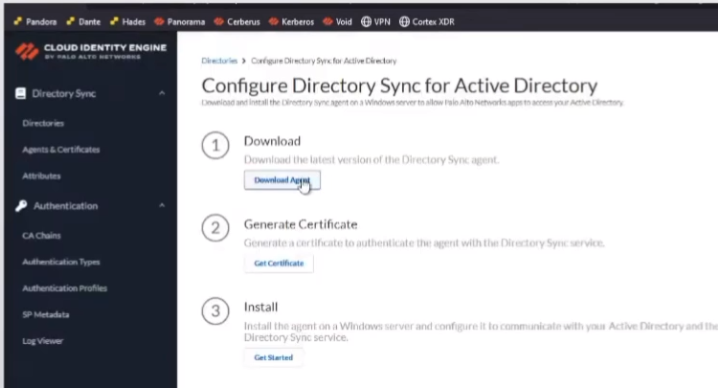
i'm going to set up the directory i'm going to click to download the agent so it's downloading and then i'm going to do click to get my certificate
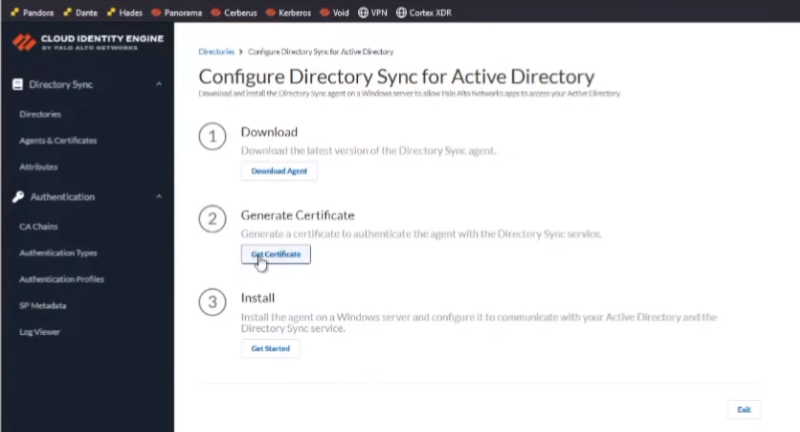
so i'm going to give it a fun uh name see i'll call it services and what i found is if you give it the machine name that you're gonna be installing it on and then the year it makes it really easy to come back to and then we're going to give it a fun little password that only we know
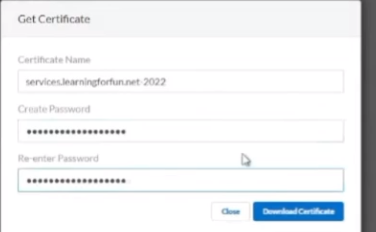
and then after that you're going to download the certificate awesome and then if you click on the getting started guide it just walks you through everything that i'veshown you and really at that point we're going to hit exit and then if we click on the agent set certificates we'll see that our certificate's waiting that there's no agent tied to it yet but what we're going to do now is swap over and i've logged into my vm where i'm going to install it and the first thing i need to do is copy over that certificate and that agent so just give me one moment
yeah i was playing with it earlier okay so the first thing i'm going to do is i'm going to install my cert so i'm going to launch cerlm
once this comes up i'm gonna go to and we can see it's by local computer i'm gonna go into my certificates here
and then i'm going to right click all tasks import

i'm going to browse to my certificate which for me i pasted on the desktop
go ahead and grab it and then i'm going to put the password in from earlier that i did on the portal
verify where i want it click finish so now we see that certs in there so we are good to go on that part the next portion is installing the client
all right clouded any setup i'm just going to step through it so once it's done installing and go down to palo alto networks cloud identity agents
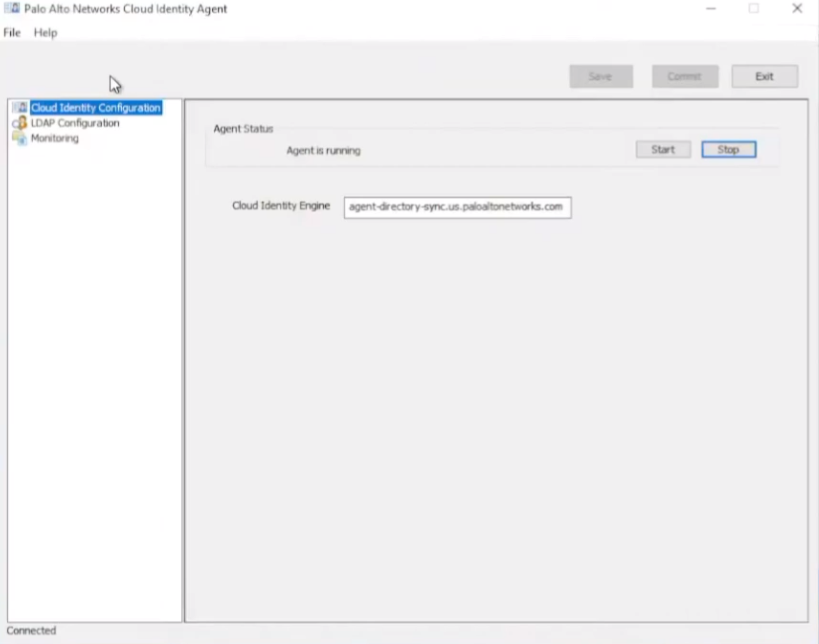
and then we're going to go to the ldap configuration you're going to paste your bind dn in and then your password and then pick your protocol so i'm just gonna use ldap s
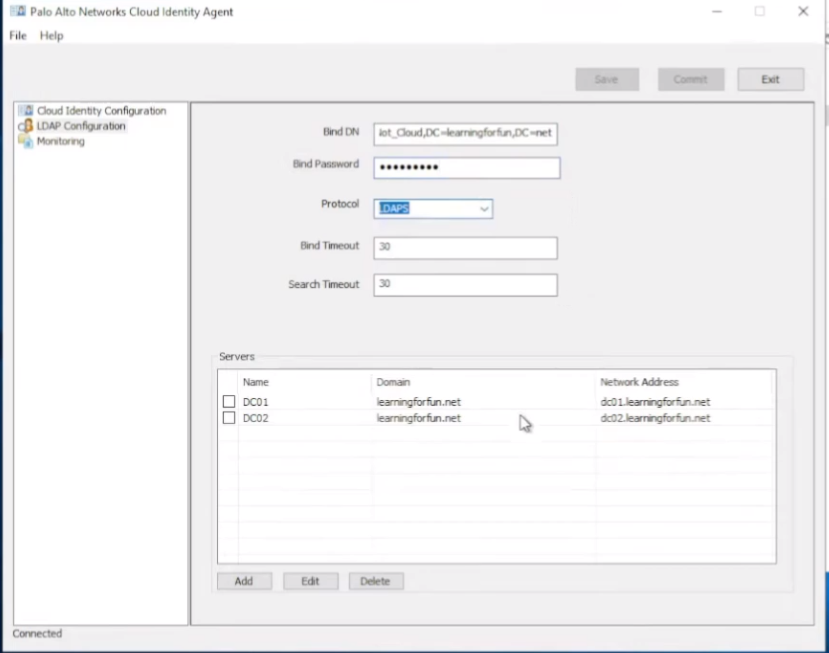
and then add your dc's that you want to query down here so i have two in here for redundancy purposes um you can add more if you want
once you're finished with that you're going to go ahead and click save and commit and then start then on the monitoring tab you should see connected
so we're good to go
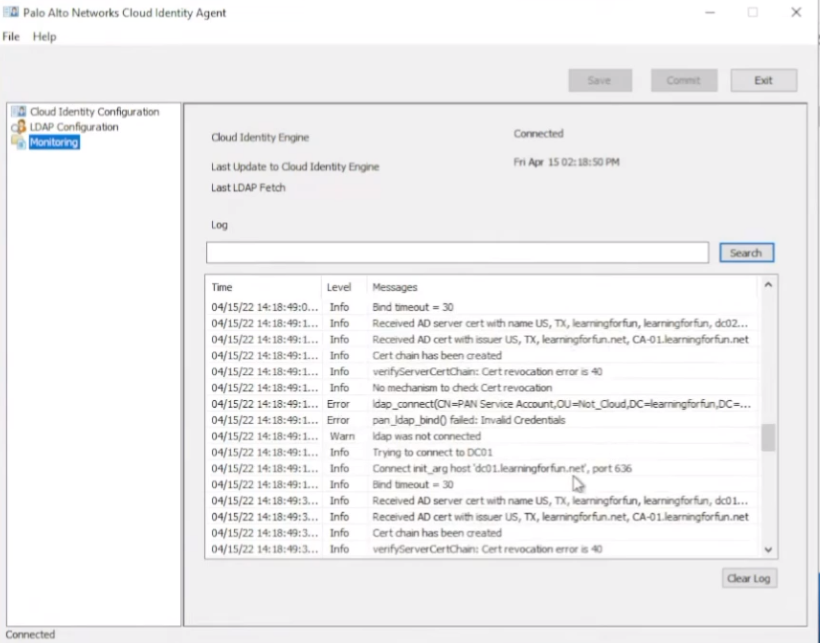
and we see with that it's going to have a bunch of information once it goes in fine failed okay so my password's not correct which is fine we can fix that save it look free troubleshooting isn't it awesome
so now we see that it's successful sending the domain list over
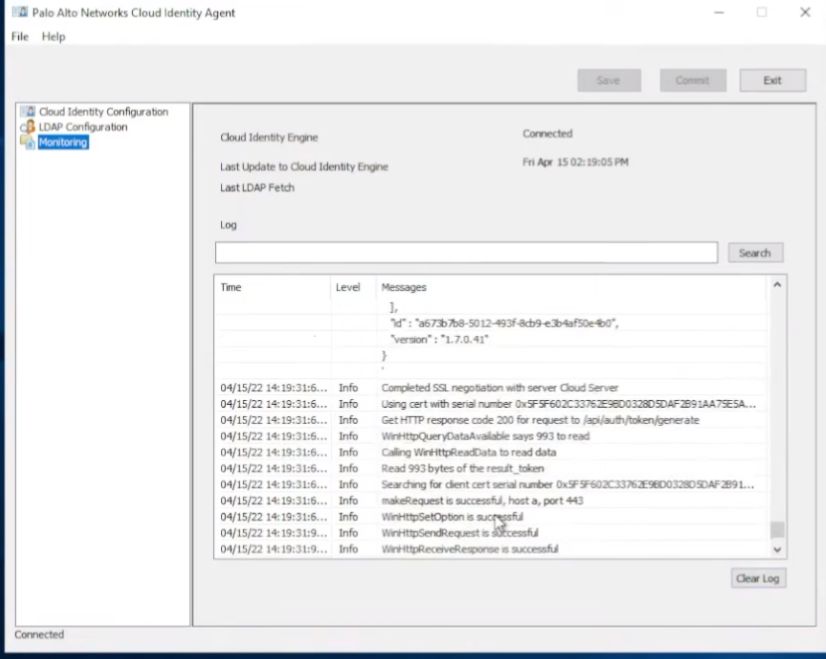
and if we jump back we see that it's connected that's great if we jump back over we'll see that now we have an agent online
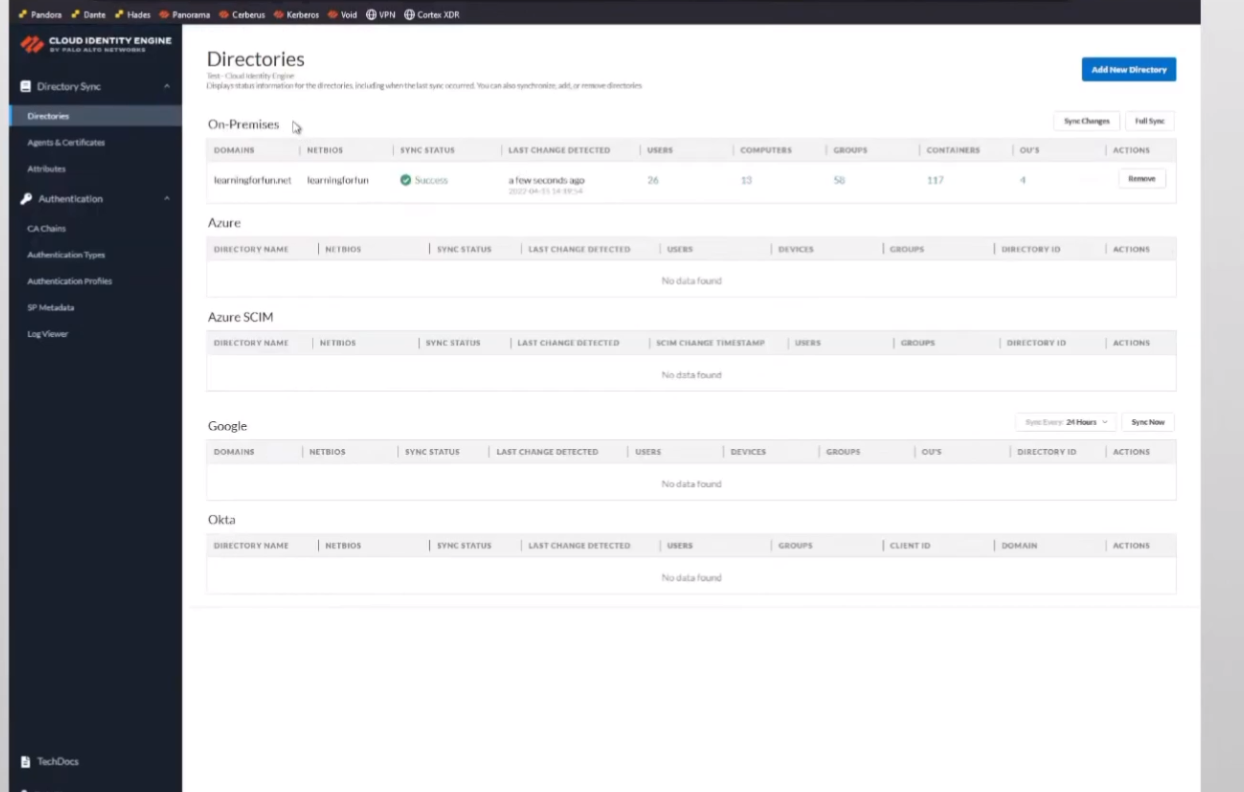
and then under my directories we should see that we get some sync information here in a minute all right so there we are so we can see the domain that got synced that bios day and we see is successful you can see the users uh the groups and i'm going to use but that's really all there is to do the the on-premise ad so only took a couple minutes we made it all the way through it and we were done with it so i'm gonna go ahead and head back to the hub and go back to our presentation
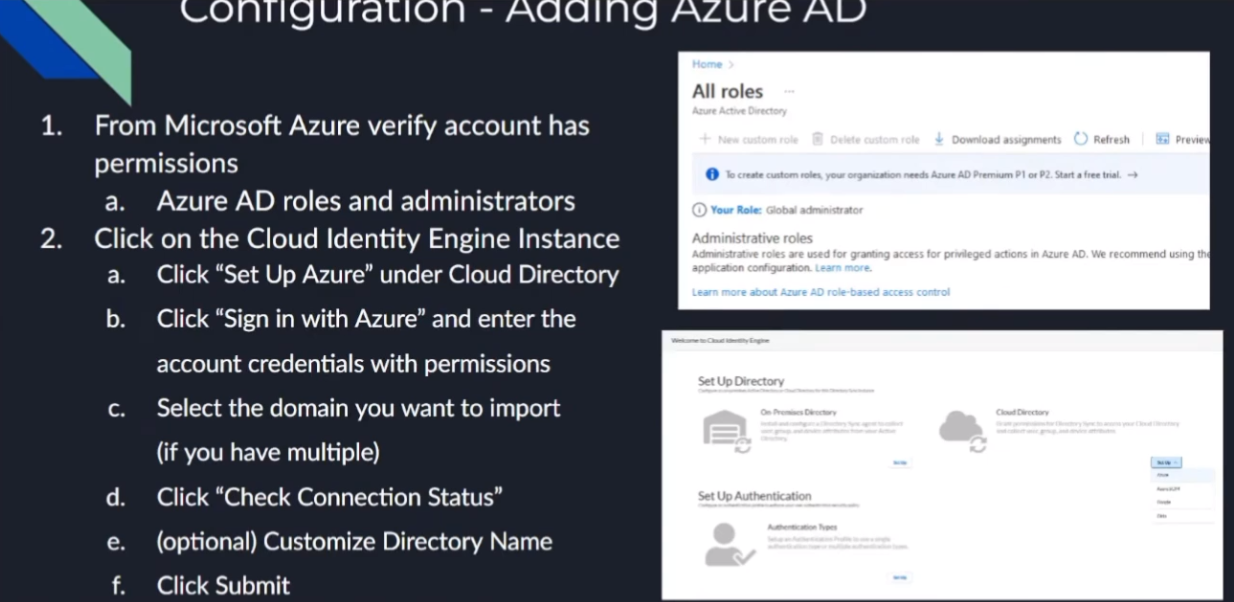
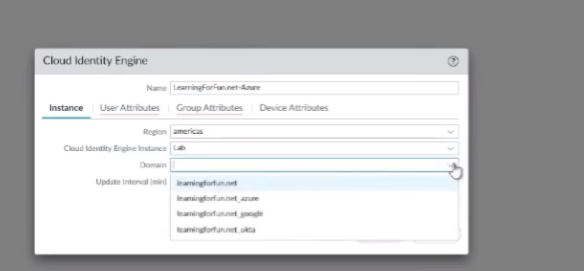
now we're going to move on to azure 80. so we want to make sure that the account has those roles from earlier the screenshot on the right you can see the little warning i had to create custom rules you have to have an azure premium p100 p2 i don't so i am a global administrator just a gear with your organization make sure they have the right rights those right rules they listed out so they're not really much to this in that case everything's done through cie once you have the right account we're going to go under the cie instance we're going to set up an azure under the cloud directory sign in with those credentials select the domain if you have multiple domains and then check your connection status customize your domain name the reason you're going to want to do that is if you have an on-prem directory and a cloud directory in the same domain say that you're migrating only some things you want to give them a distinct identifier so like if it's learning for fun.net is my on-prem and then i have one in azure you'll see that i tag it with underscore azure same goes for google and then octa that way you can identify them when you're bringing them in and there's you'll see that when you're doing it on the firewall or any of your your instances that that you'll want to do that that's only for overlapping domains
so the way that you validated something correctly you'll see that just like with our on-prem one and with the rest of them it's we'll have success we'll have users and we'll have groups
so with that i'll go ahead and do the walkthrough so we're back at the hub so we'll go ahead and pick the azure instance when we log in we're going to go ahead and do theappear cloud directory we're going to click sign in with azure
it's going to take us to our nice little microsoft sign-in page
and then we are going to sign in maybe maybe we're gonna go sign in
all right once we are logged in you can see i have two domains i'm just gonna go ahead and click one and then we're to test the connection
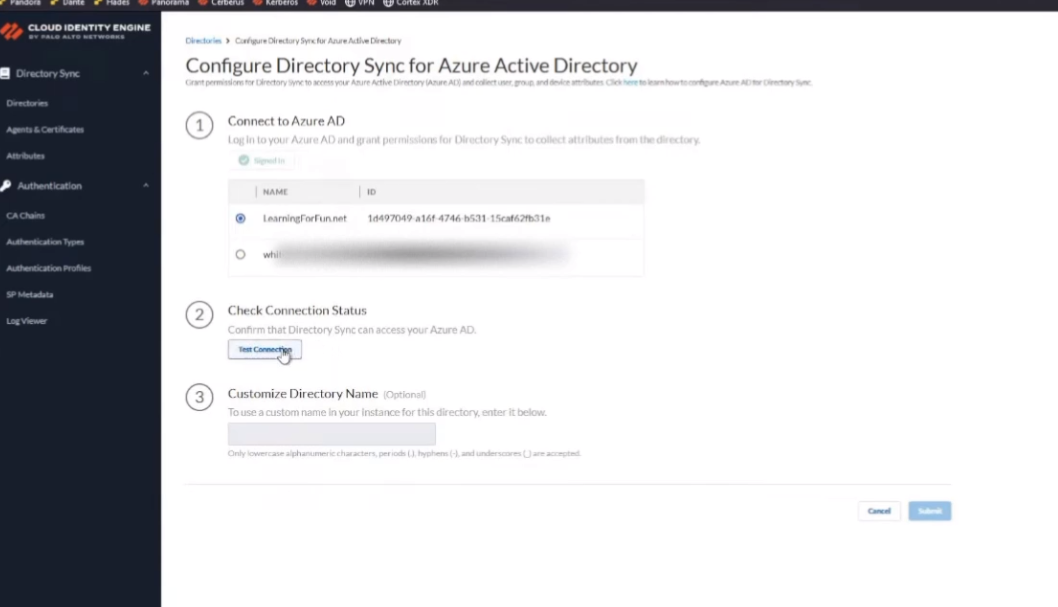
once it's been confirmed successful we're going to give that customized name so this one will do underscore and i'm going to do azure so that has its own customized one and we are going to go ahead and click
submit you'll get it in progress
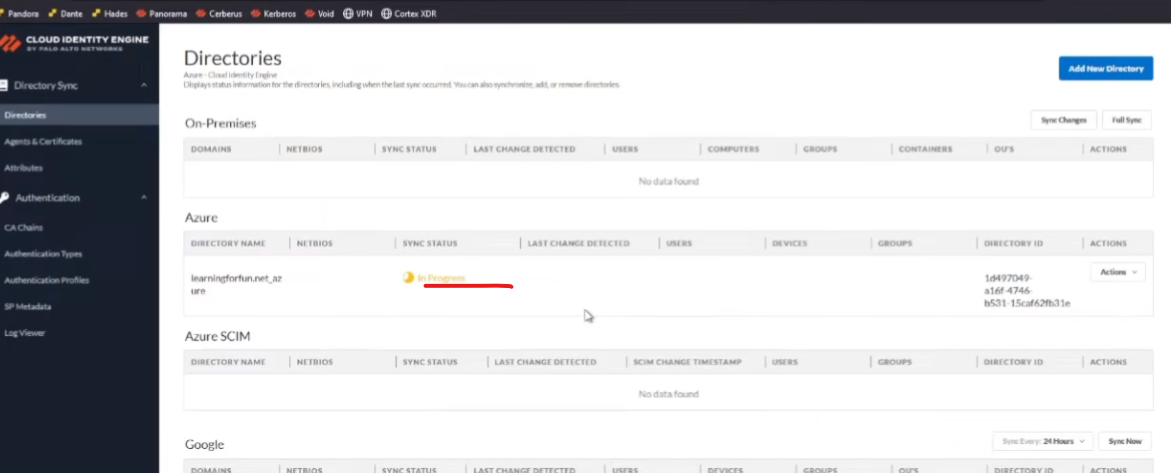
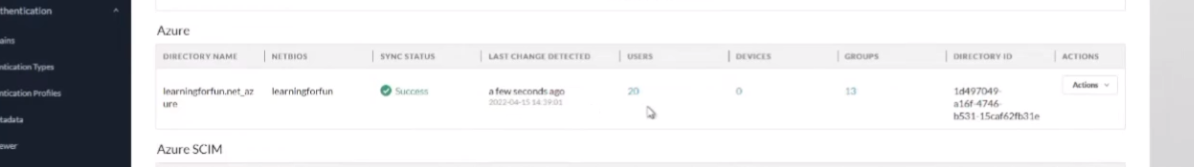
and this just will take a minute or so for it to sync up and we'll get those positive uh sync status messages and we can move on so there we are we see success we see
that we have users and we have groups and that's all there is to it for that
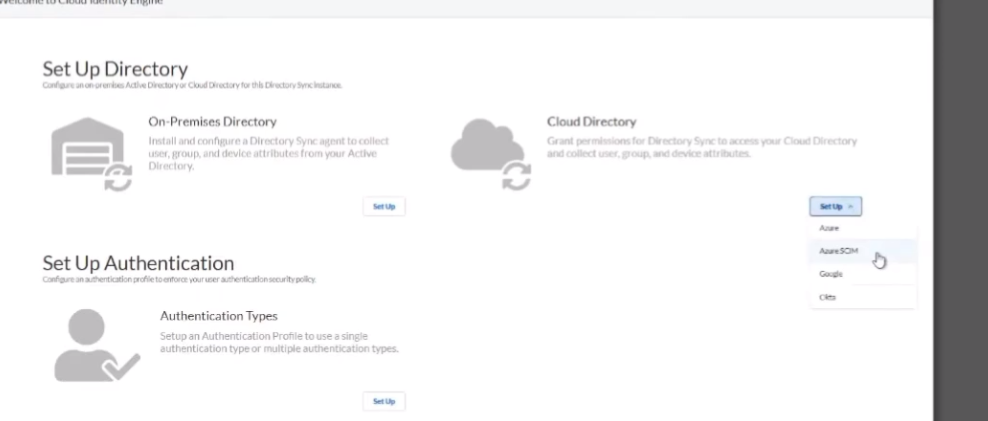
so i'm going to transition back and next we are going to go over to our azure using skim this time
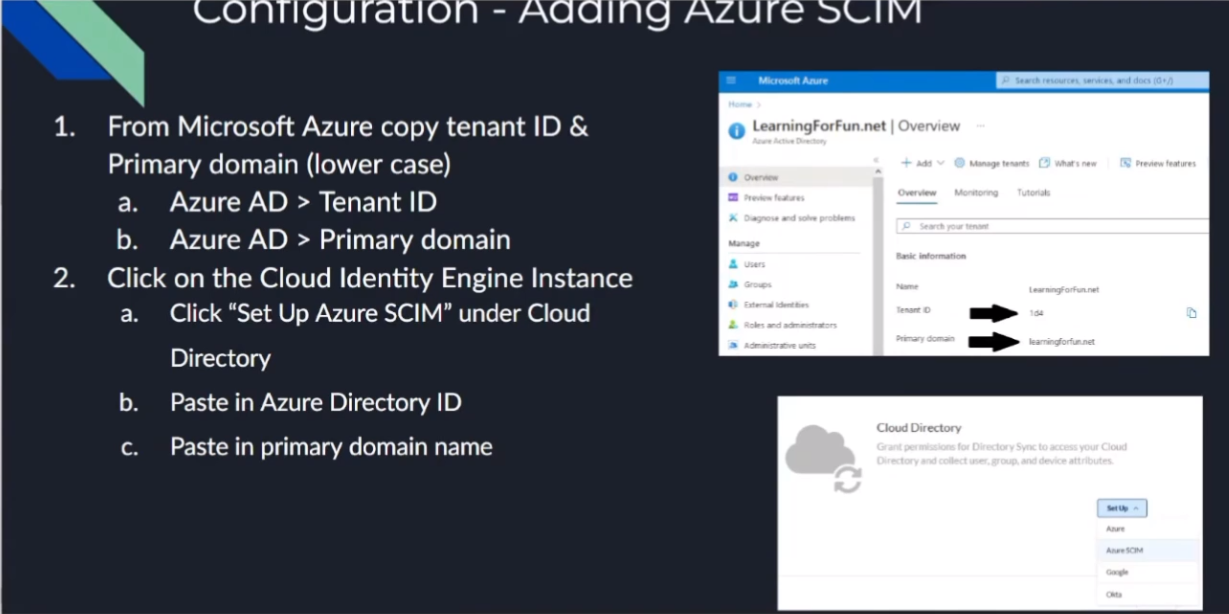
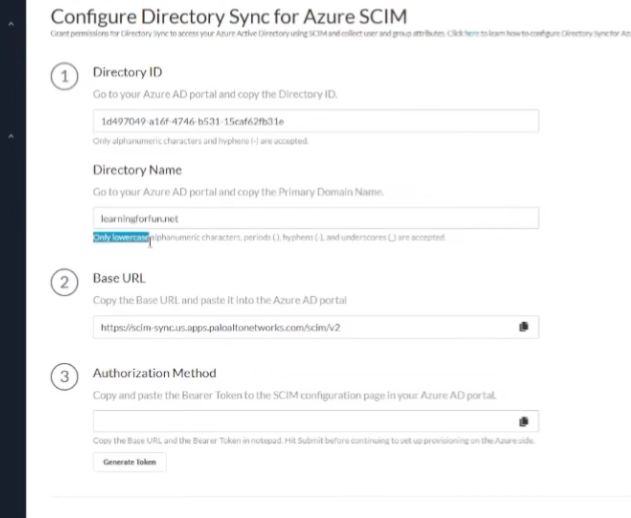
so to do that this is a little bit more complicated as a couple of bouncing back and forth between microsoft and uh the cie instance
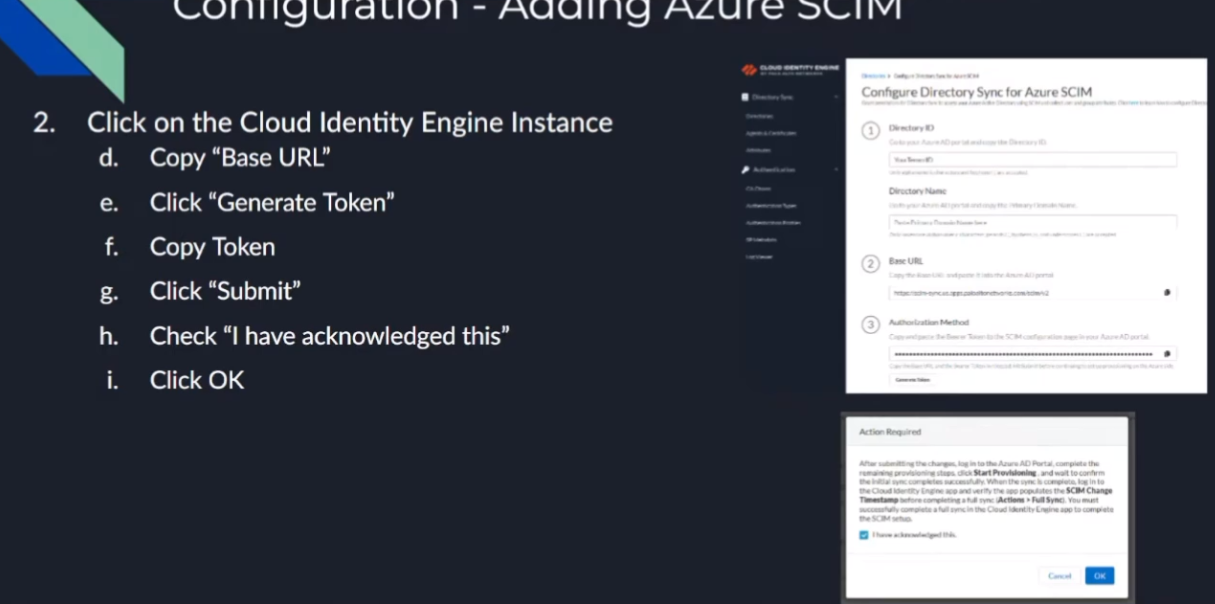
so first off we're going to want to make sure that we copy from microsoft our tenant id and then the primary domain and then we're going to use those inside of the cloud identity engine to help generate our secure token and so we're going to paste that in to the azure what we copied over from azure the attendant id and the domain and then that's going to give us a base url which we need to copy as well as uh we need to generate an authorization cookie we're going to copy those two things and then take and then we're going to submit that and we're going to acknowledge a message that says hey once this is done and you go over there you paste this into azure and you sync it you need to come back over here and do a full synchronization as a last step to get everything working
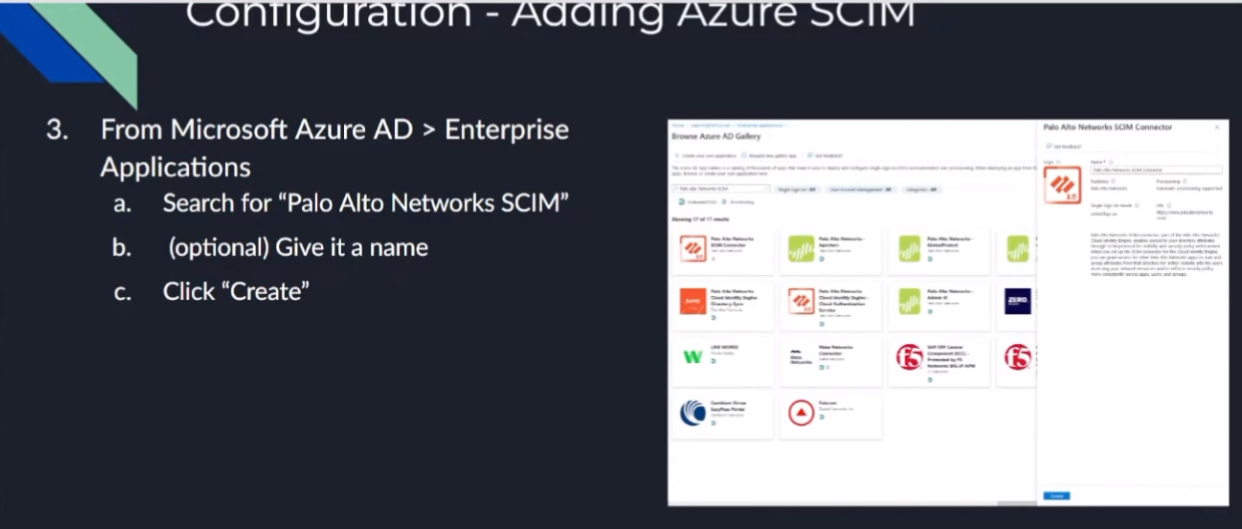
so now where we have the piece of information we're going to go under our enterprise apps and azure and we're going to search for palo alto network skim once that comes up you're going to give it a custom name if you want or you just leave it as palatable the network skim and then we're going to click create once it's created we're going to go down
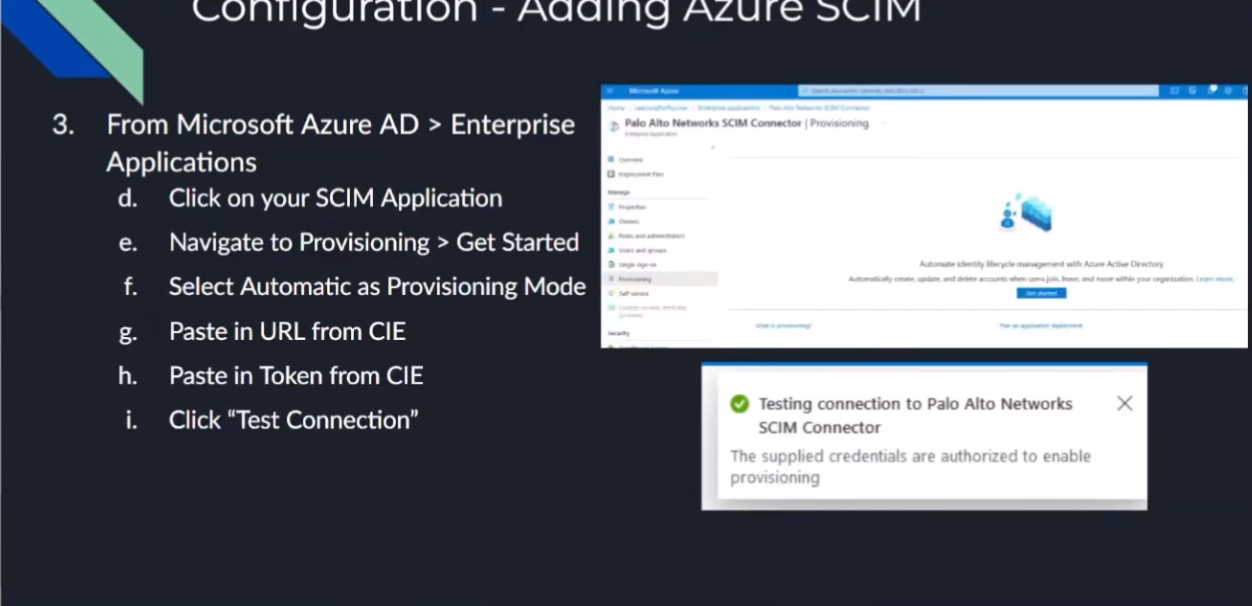
to provisioning and once there we're going to click on getting started you're going to paste that url on that token from the cie portal like like i said it's a bunch of back and forth but we're almost done and then we're gonna test that connection you should see a positive message like the one i have down there and once you get that you can go ahead and click save and after doing that what you're going
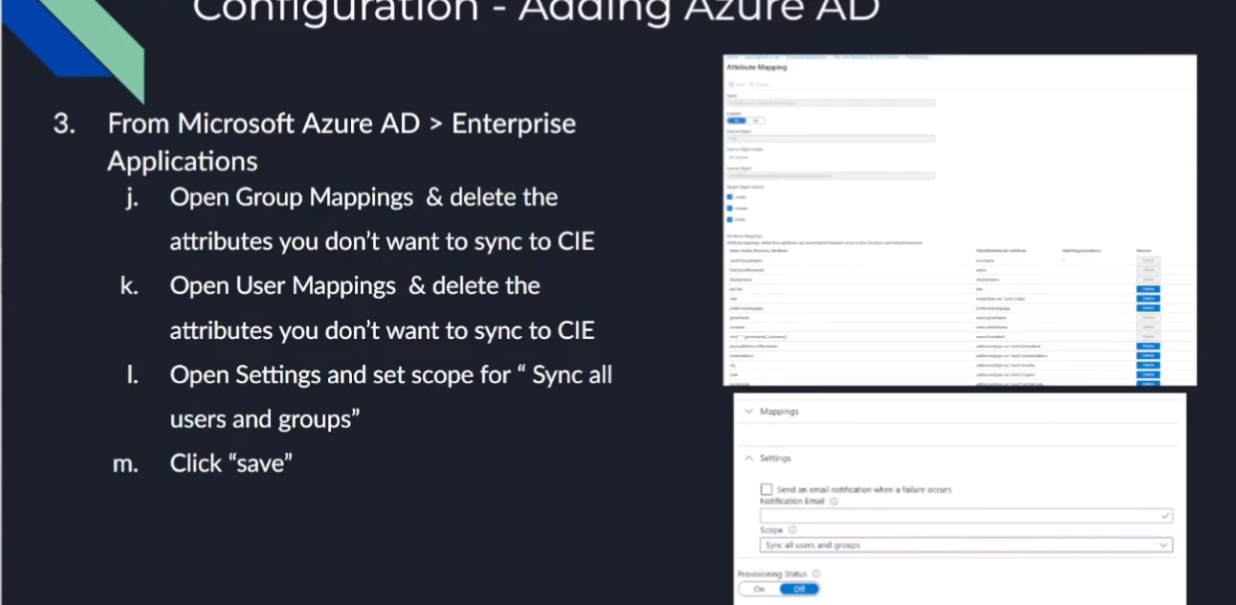
to want to do is you're going to open up your group and your users and you should see a list of all the attributes that you could delete so just the ones that you want to send over right so this is the big power behind skim besides having that credentials now we're setting up that secure connection between inner domain identity mappings it's such a cool name um but it allows you to really limit what you send over as far as attributes and things like that so go in there select what you want to and then with that the last step is to go under settings and set it to sync for all users and groups click save
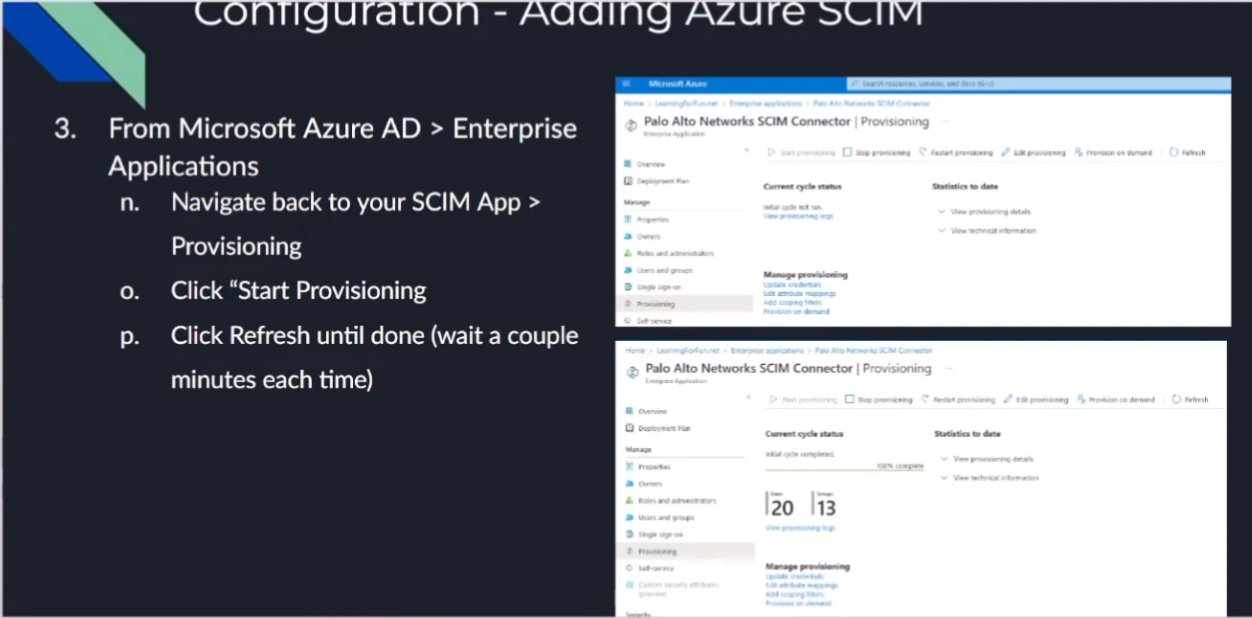
once we're done with that you're going to click on start provisioning under under the app itself we should see that under provisioning and that's in that top left area over there once that's done you should see it change that screen on the bottom down there where it's going to talk about number of users number of groups and say it's complete
once that happens
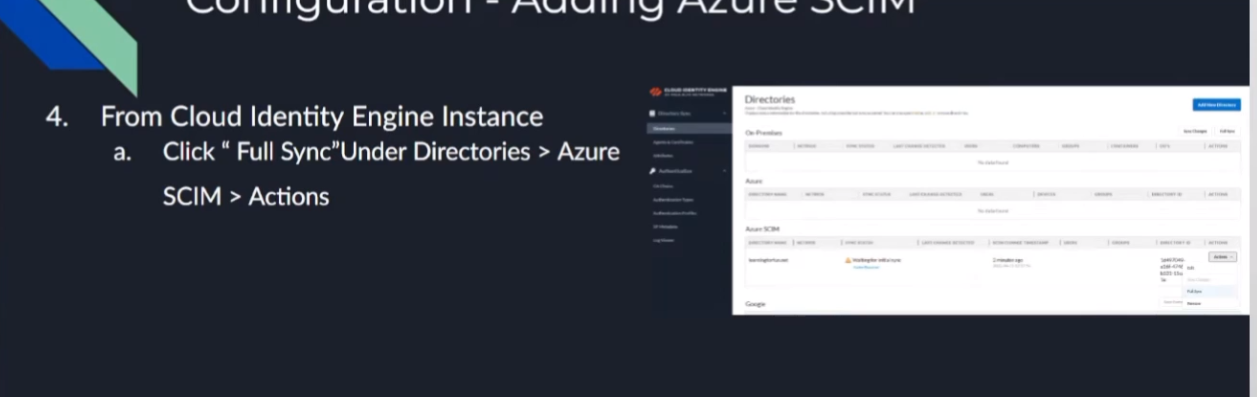
we're going to go back over to the clouded in the engine and remember that message we had to acknowledge where we have to go back and we tell it to do a full sync afterwards well this is us doing that full sync and that's it after that we're done so it's only six times back and forth but no one's counting uh and then to validate it looks just like the rest of them we have success we have users and groups who would have thought so now
we're going to go ahead and walk through that so here i am back in my hub under skin all right so first thing i need to do is i need to go to my instance and under here active directory
i need to copy my tenant id so i'm going to go ahead and paste that over and then i need to copy my primary
domain so now that i've grabbed those i can jump back over to my cloud editing engine
and click on azure skim and i'm going to paste those in so paste in my directory id i click on put in my domain all lowercase
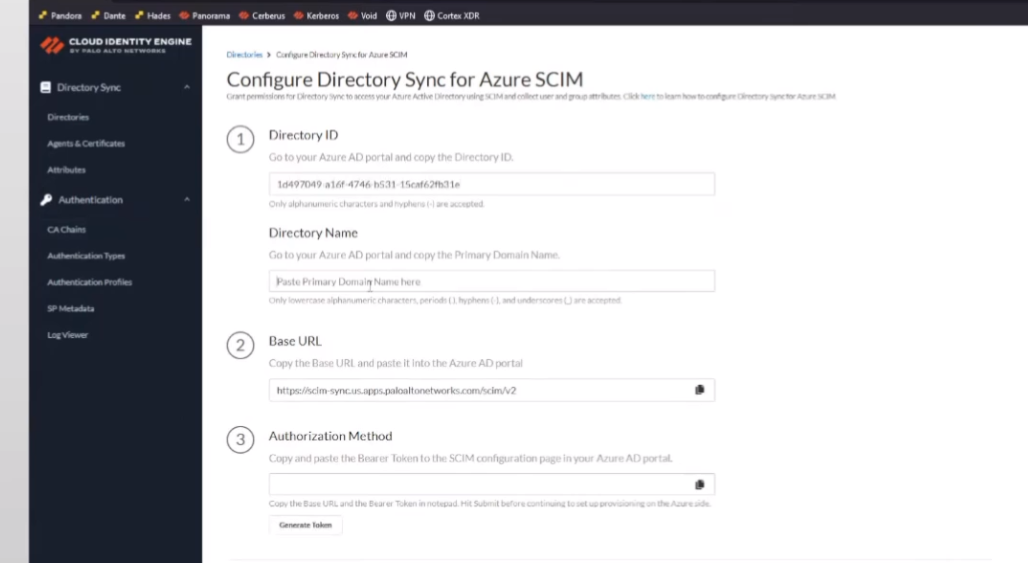
tells me right here only lowercase so it's good at hinting
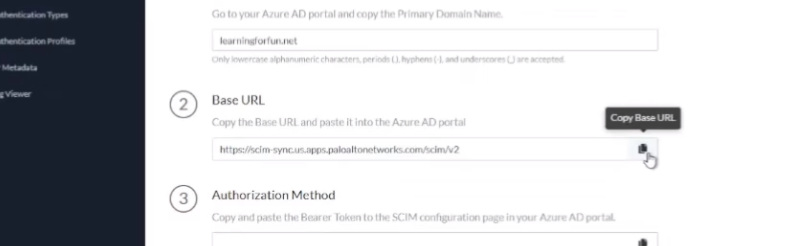
and then we're gonna copy out this base url

and then here's where we're gonna generate the token gonna go ahead and copy that we're gonna need that here in a minute all right and then we're going to hit submit
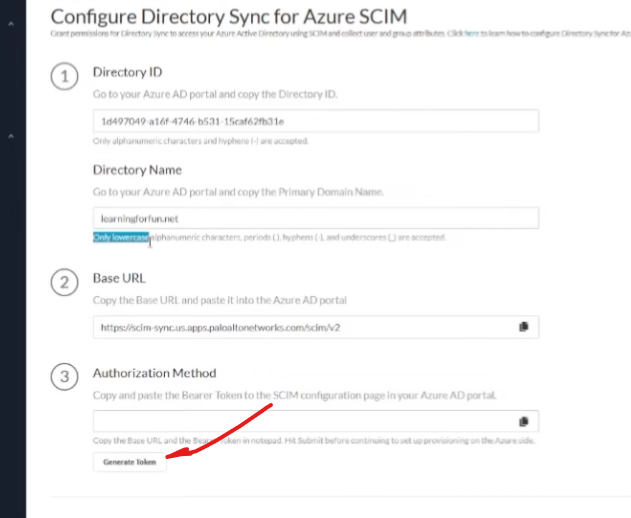
and then here's where we're gonna generate the token gonna go ahead and copy that we're gonna need that here in a minute all right and then we're going to hit submit
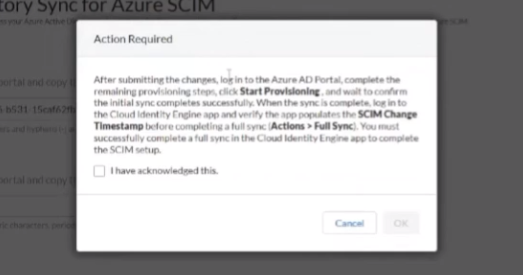
and we're going to acknowledge that we know after we go over to azure we're going to have to come back here and click submit or uh full sync yes so we're going to click it and hit ok
all right our work here is almost done it's waiting now so now we're gonna go back to azure we're gonna go under our enterprise applications we're gonna go to new application hello alto networks skim
there it is i'm going to call it so give it the default name because i'm not feeling that creative right now all right so i've created it almost i've clicked the create button
it did i clicked it
all right so now that it's created i'm going to go under my provisioning
click get started select automatic
and then there's my tenant url on my secret so i still have the secret copied over
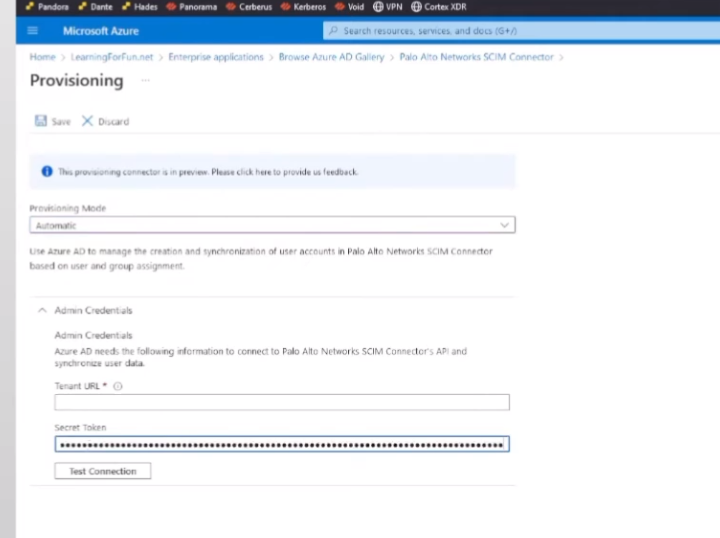
and paste it in first go back grab my tenant
test the connection you can see that positive message there so that's awesome
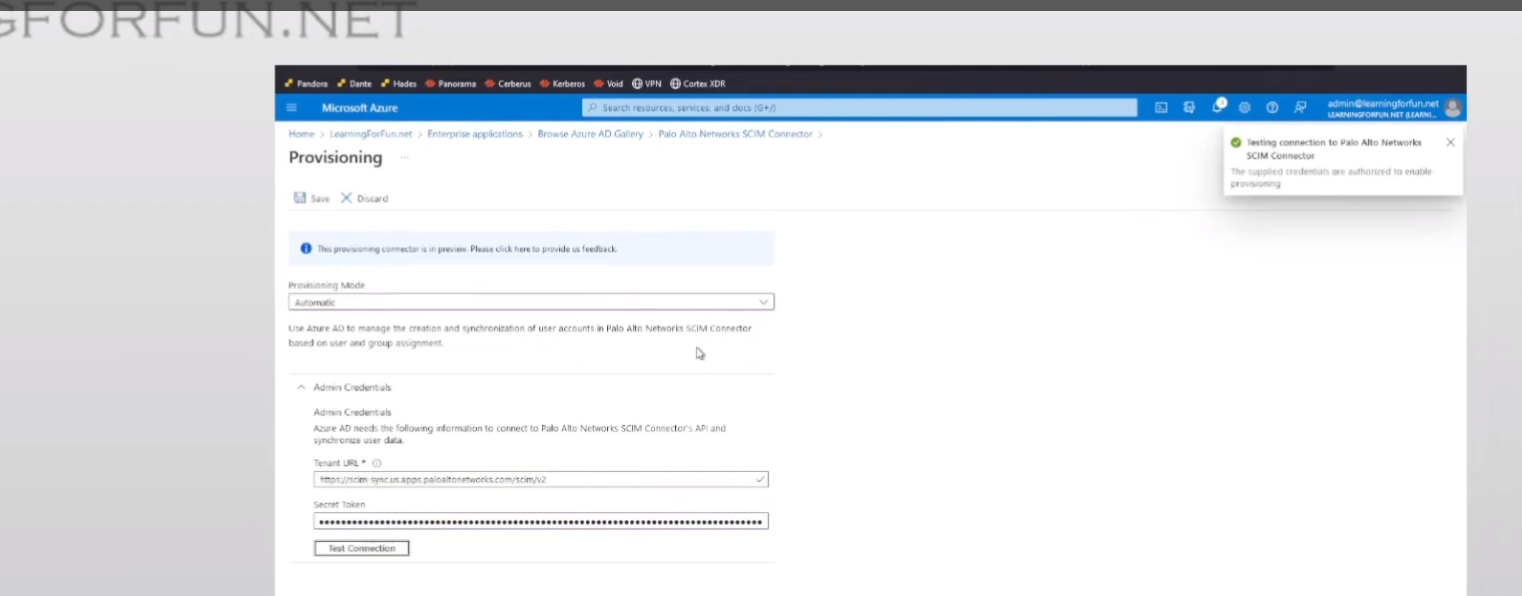
click save all right now we're gonna go to our mappings
and i for one don't want the cie to know what city my users are in
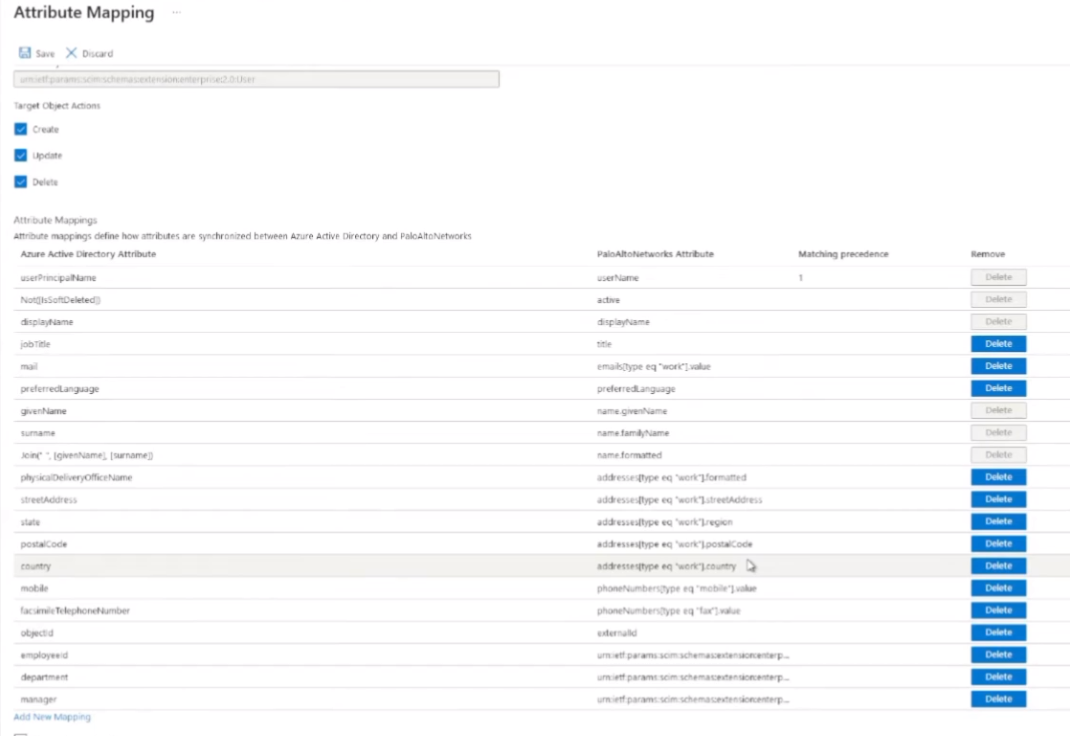
and i don't want them to have telephone numbers so this will just depend on your organization right you could be all or none we just really need to have uh whatever you're using for the group mappings so if that's the mail and upn then so be it um we just it just really comes down to it you'll see there's some of them that are greyed out like the upn uh the mail you can delete but i found a lot of the times and most of them you'll see in my my examples the mail is what i use the primary username now that we're moving to the cloud that's more often than not the one that i i like to use rather than upn
so but do whatever makes sense and once that done just click save save our changes
all right then we're going to go back to provisioning and then down here under settings
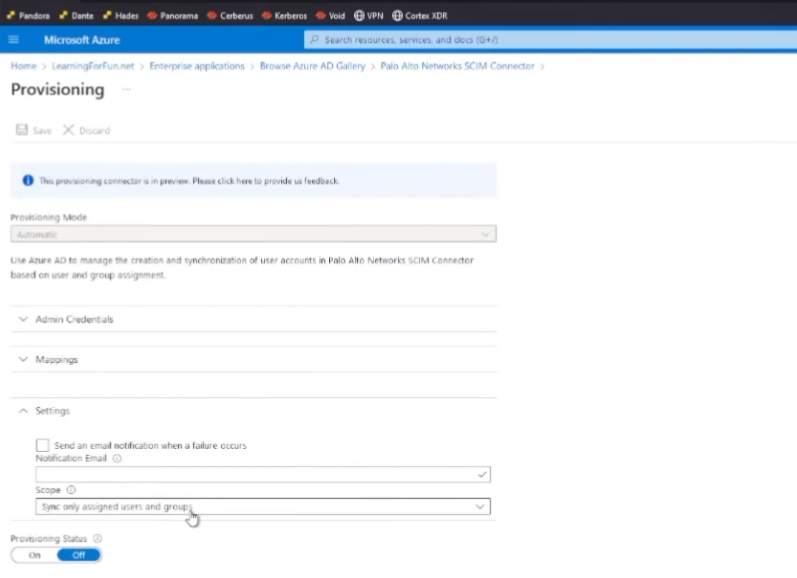
usually thanks there i don't know why i wasn't there but it was supposed to be so sync all users and groups and then i'm gonna go ahead and click save and with that i should now be able to go back and click start provisioning
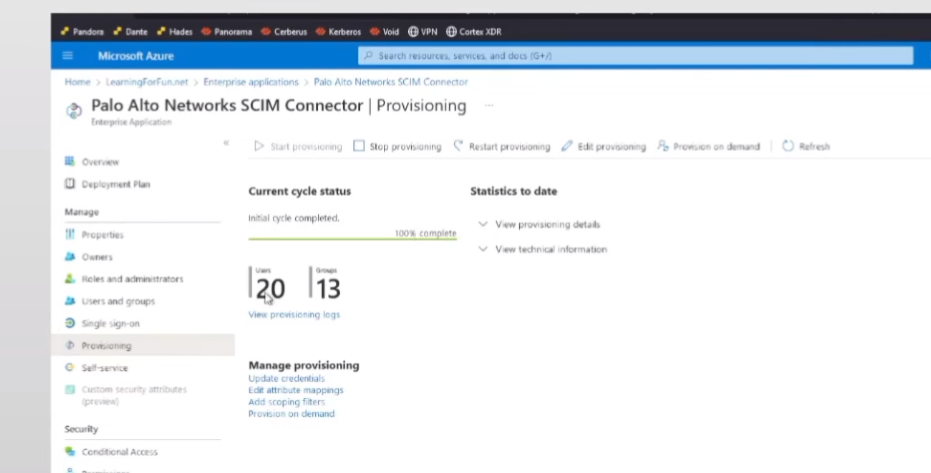
all right so click refresh we see it's done i have complete users and groups but i'm not done i got to go back over to the cloud identity engine because i told it i would
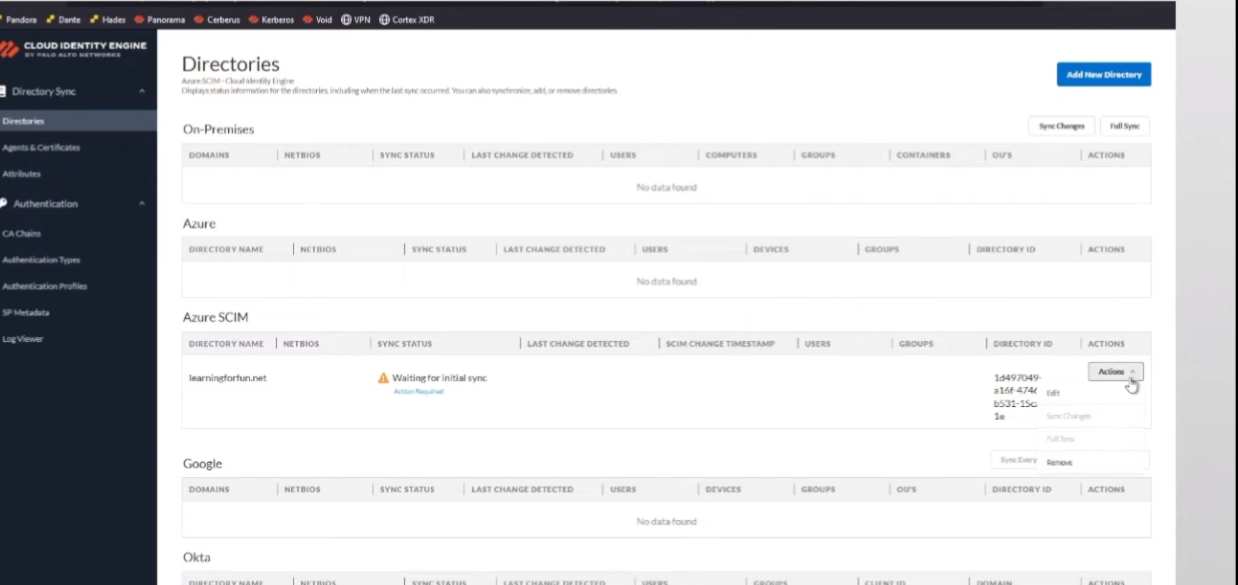
and now go to actions and let's go come on be there on this wait go ahead and refresh this all right so we see the directory id showed up and a minute ago so now that that's there full sync is here i'm gonna click yes and this is where I win
so next we are going to move onto google so for google first thing you want to do is go ahead and verify your account has the correct admin role you could either create a specific admin role or just give an account that has a permission it says 15 permissions up front the screenshot i have there on the right
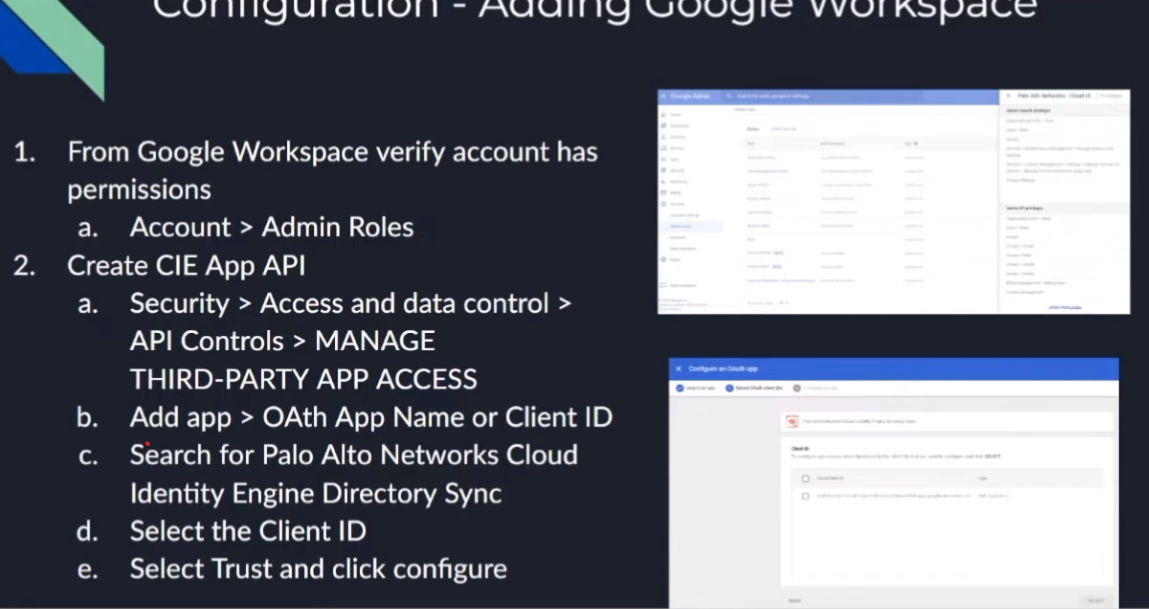
has all 15 in it that's the group that i created earlier just to show it i'll walk you through show you how it is if you want to go ahead and manually do it and that's really it beside your uh google tenant id you'll need that everything else is done in the cie we're just going to go in actually i take that back we have to add the third party app access api and the way that we do that in google is we go down through security access and data control third-party app access we add the app the oauth app name and client id this is what we're selecting and then we search for palo alto networks cloud identity engine directory sync
select the client id there's only one client id and select trust and configure
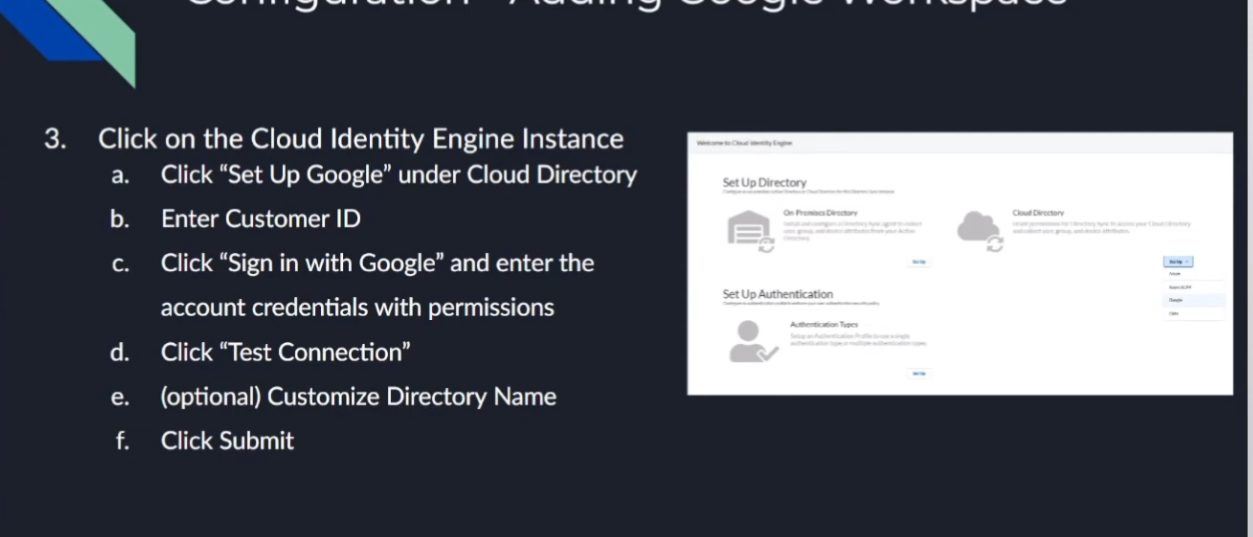
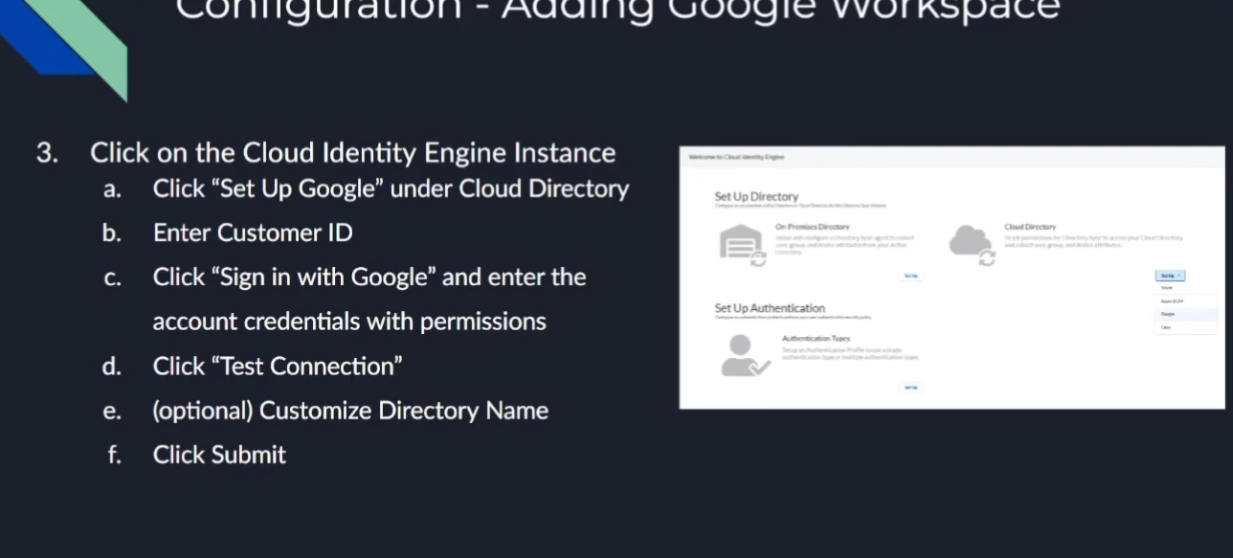
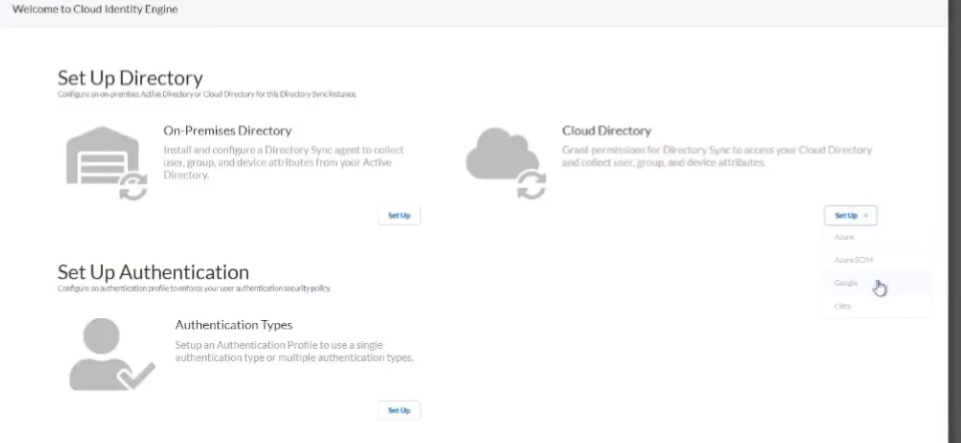
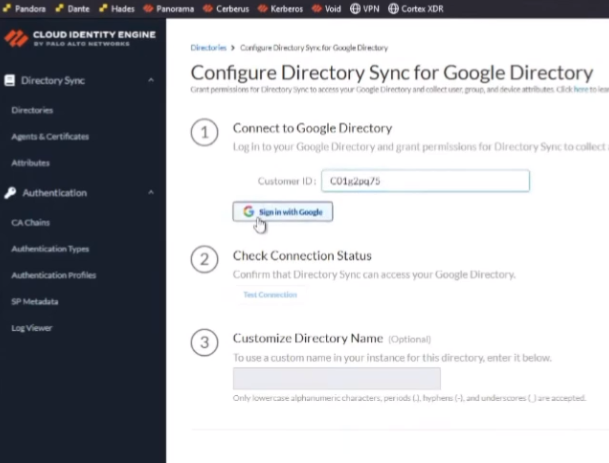
and then that's it that that's what allows it to tie in and so after we do that then we go back to the the cloud id engine and we go to cloud directory and google we're going to enter that customer id which i called attendant id but it's a customer id completely different and then you're going to sign in with that account that has the permissions for those 15 uh permissions in that role that i was mentioning earlier for google we're going to test the connection you're going to customize the name if you need to remember if it's overlapping you're going to want to yes you are and then you're going to want to click submit
and then to verify it's going to say success it's going to have users and it's going to have groups and you are going to win so now we're going to do a walkthrough
but here we are we're back and go into our google cloud identity engine
we are going to first go to our google admin console
and i am going to go to account and admin roles
and it's going to verify its fee because that's cool all right it's still me we're there for a minute all right so here's the one that i created earlier
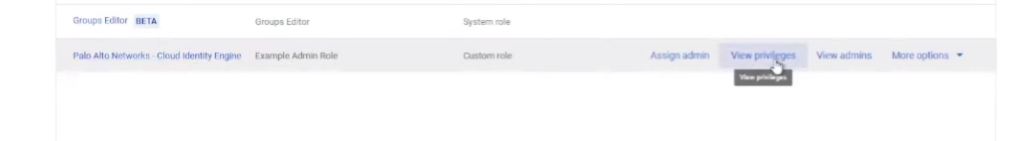
so if we view the privileges you can see here's all 15 privileges that are required
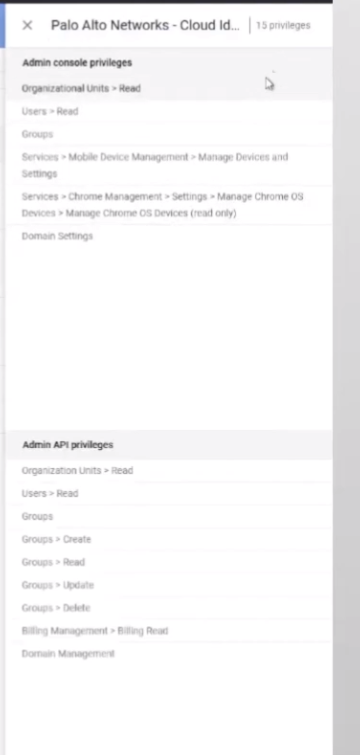
uh if you wanted to to edit it um let's see here just go into it and then yeah it's just selecting them from this drop down box
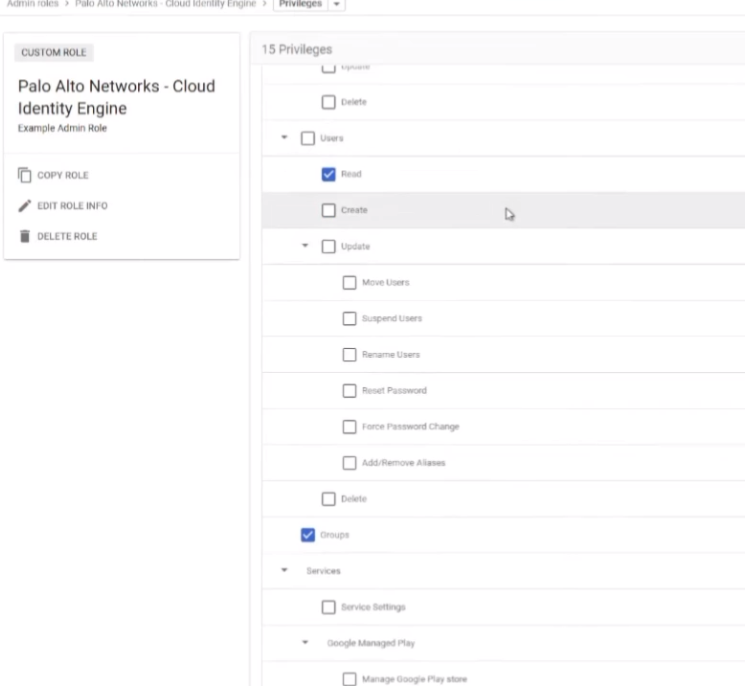
right so just easy to go under each area it tells you from that screenshot i did earlier it's not really that exciting so have fun with that
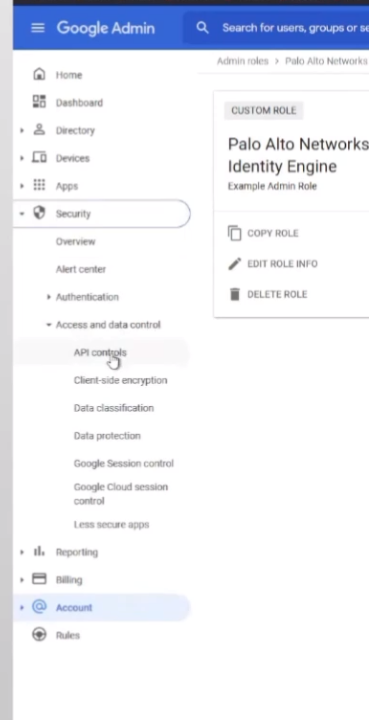
so once you get a an account set up with it or you set one with the right role now we're going to authorize the cie to talk so under security we're going to go to access and data control and then api controls and once you're there you're going to manage third party app access
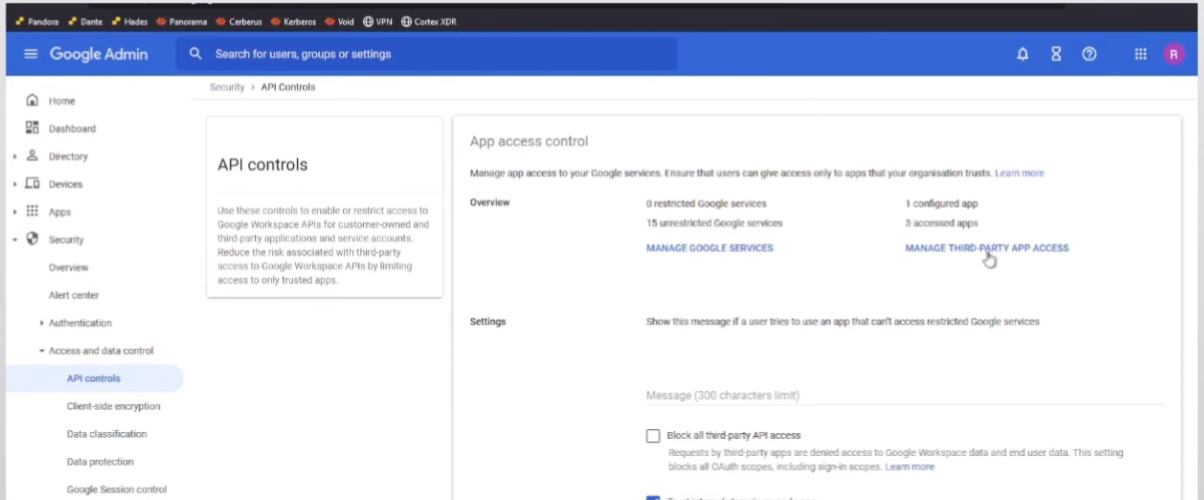
so i already have it down here and it's entrusted but it's the same process
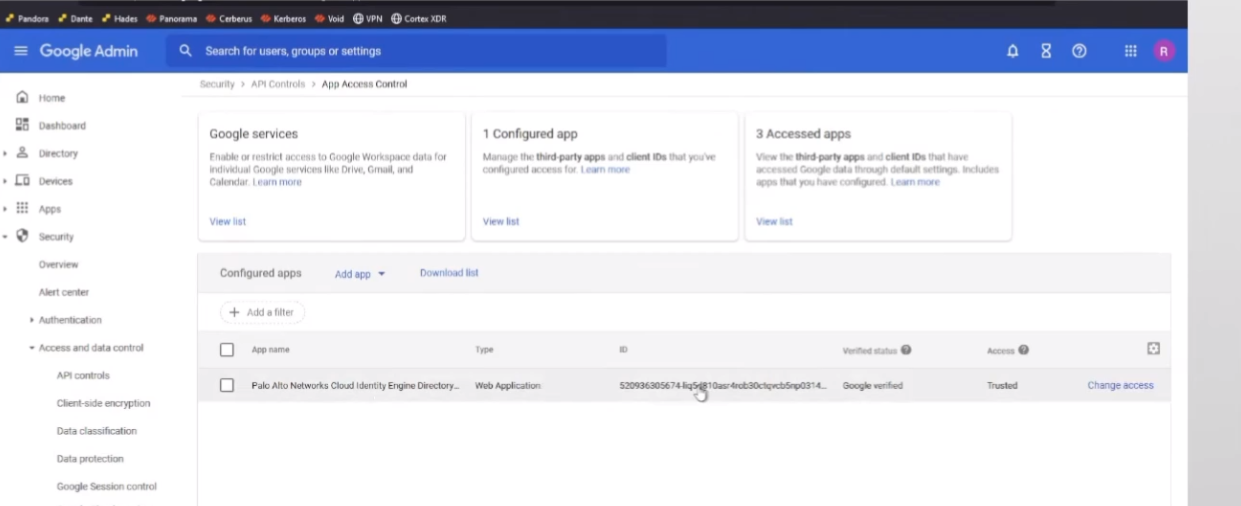
i'm just going to walk you through we're going
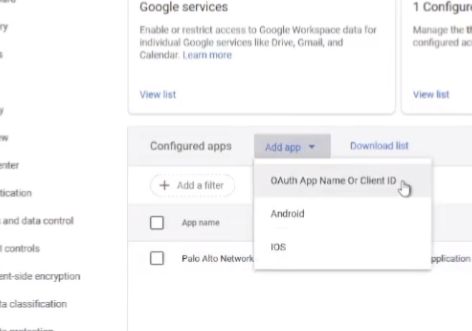
to add app there's a oauth app name or client id
we're going to search here for palo alto networks you can put cloud into the engine if you want but there's only two things that come back right now and so we're gonna do the one that's called cloud identity engine directory sync
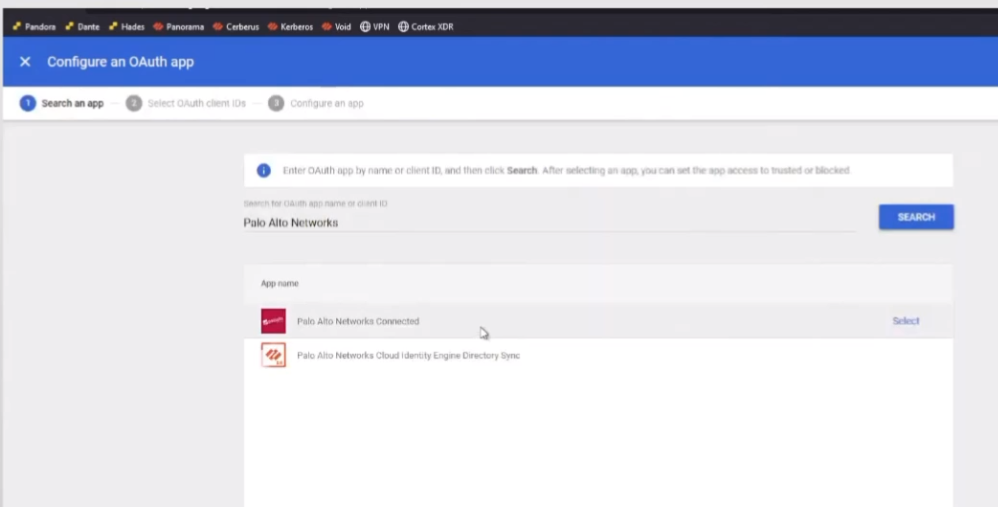
we're gonna hit select here's that client id we're gonna go ahead and check
it we're gonna hit select now we're gonna hit trust
once you do that you're gonna hit configure and since i already have it it'll error out but that's what makes it show up down here and then you can tell it to to access and that's really all there is to it from this point we're going to go back to the cloud identity engine if you need to know how to get your account uh your not your tenant id your client id under account under account settings or customer id now let's call it everything but the right thing you'll see it's it's right here so i have that copied down over here
so i'm ready to go so i'm gonna go back to cloud identity engine go to google and then put my customer id
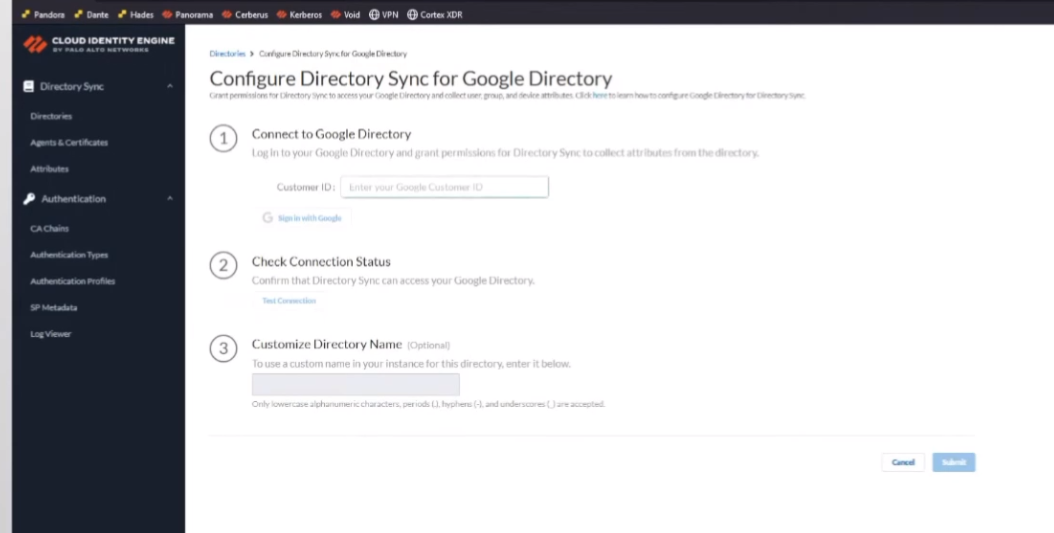
and assign it to google
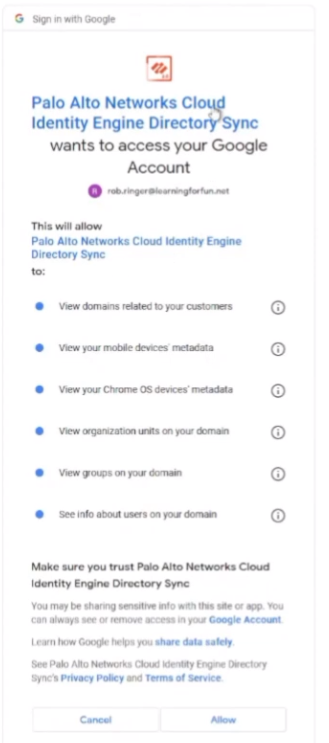
with my super secret site in name then i'm going to tell it it does have permission to access my domains uh my mobile users chrome os basically everything so i can get those attributes right so i'm gonna go ahead and allow it once i do that
it's gonna i'm gonna do test connection it's going to pull it and here's where i'm going to customize it l
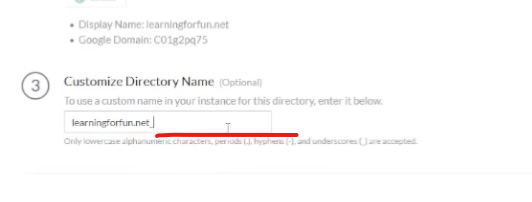
et's put google at the end go ahead and click submit
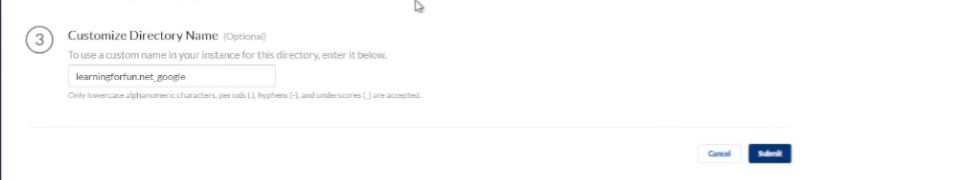
i'm going to win all right so we're going to wait a minute
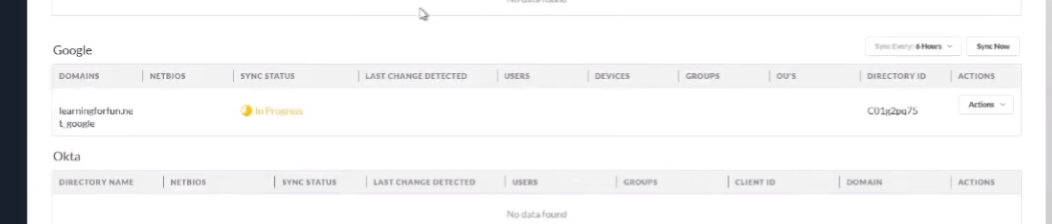
and it's going to show up that'll be awesome
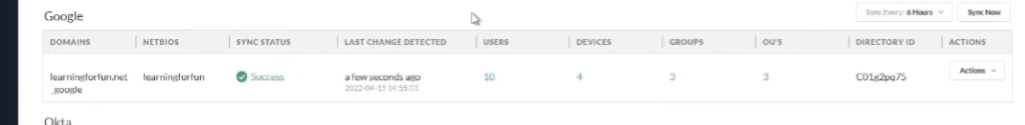
all right so we have our sync status success our users our groups we are good to go so
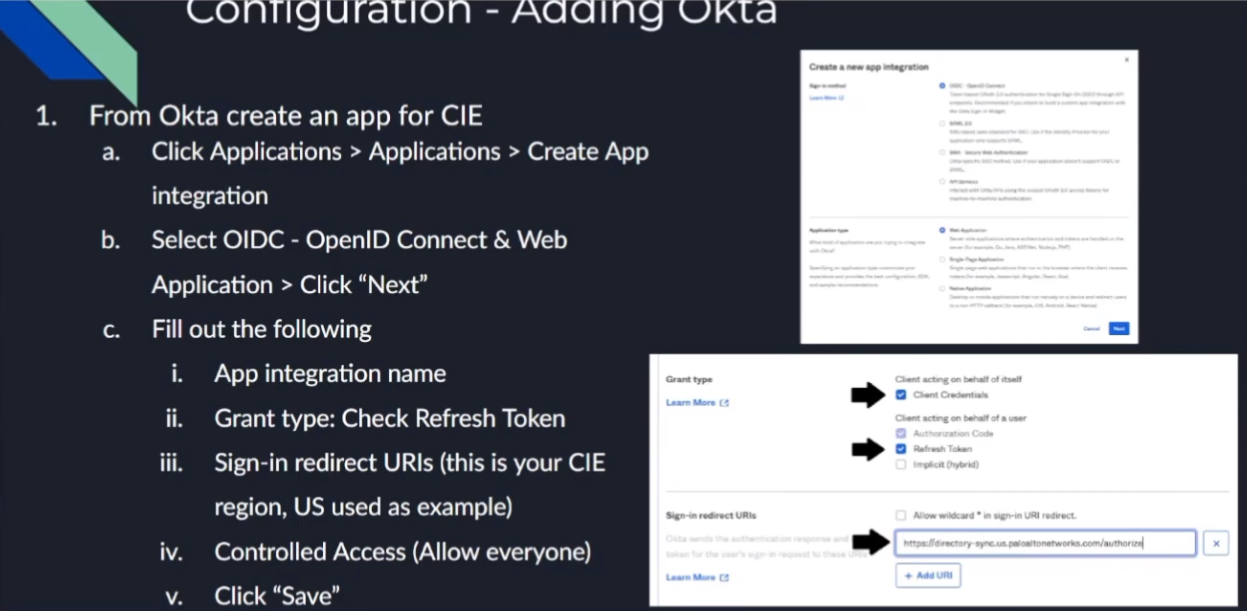
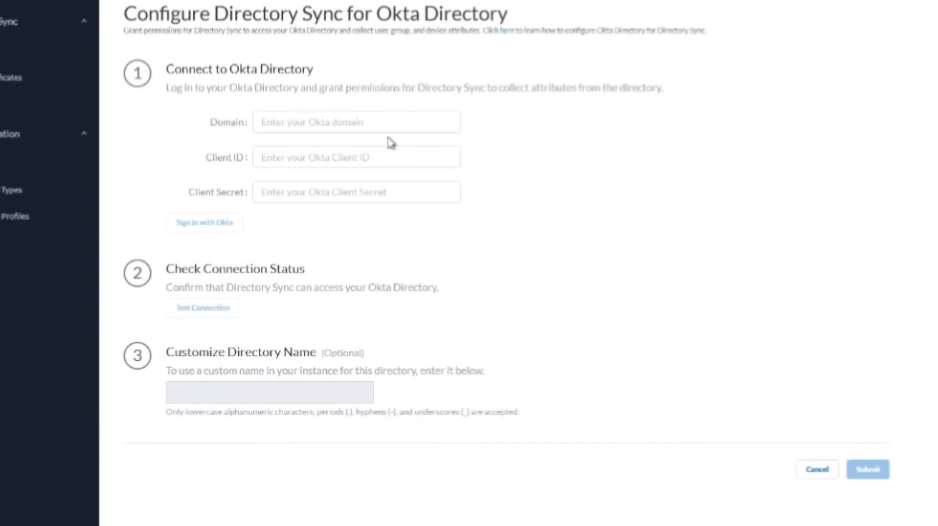
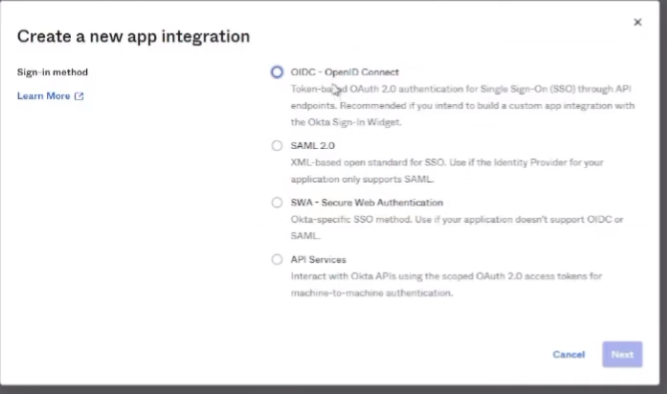
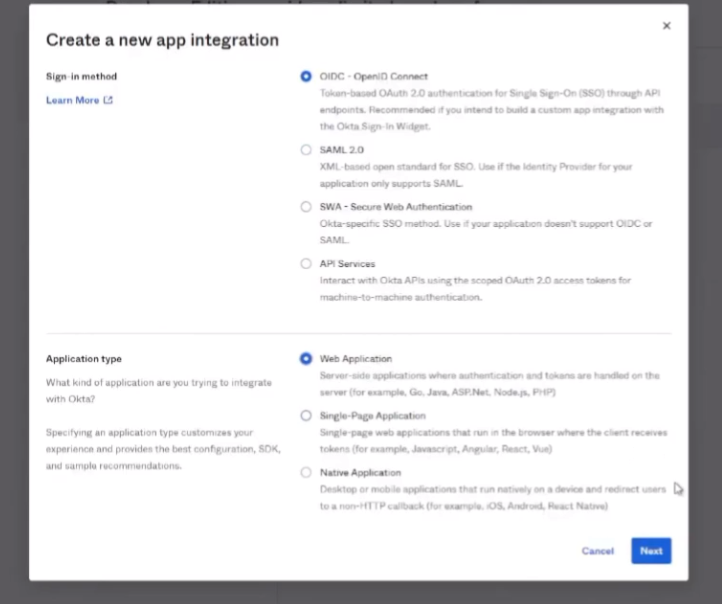
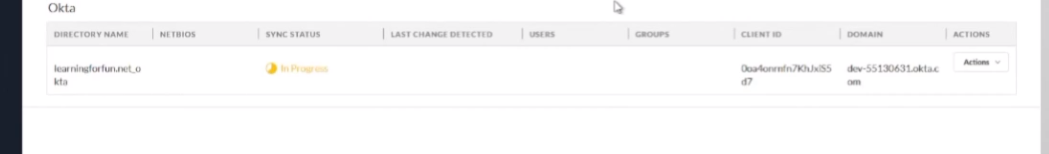
all right to do octa what we're going to do is we're going to log into the octa portal and then we're going to create an app for cie so we need to go to applications applications create app integration select oidc and open id connect and then web application click next so we're going to give it a name and then grant type we're going to check the client credentials and the refresh token then the sign in redirect url this is your cie region us is what i have in the screenshot down there but in the documentation you can find all the rest of them and then controlled access i'm just going to send it to allow everyone if that's what you want to be able to connect into it use that and then go ahead and click save so
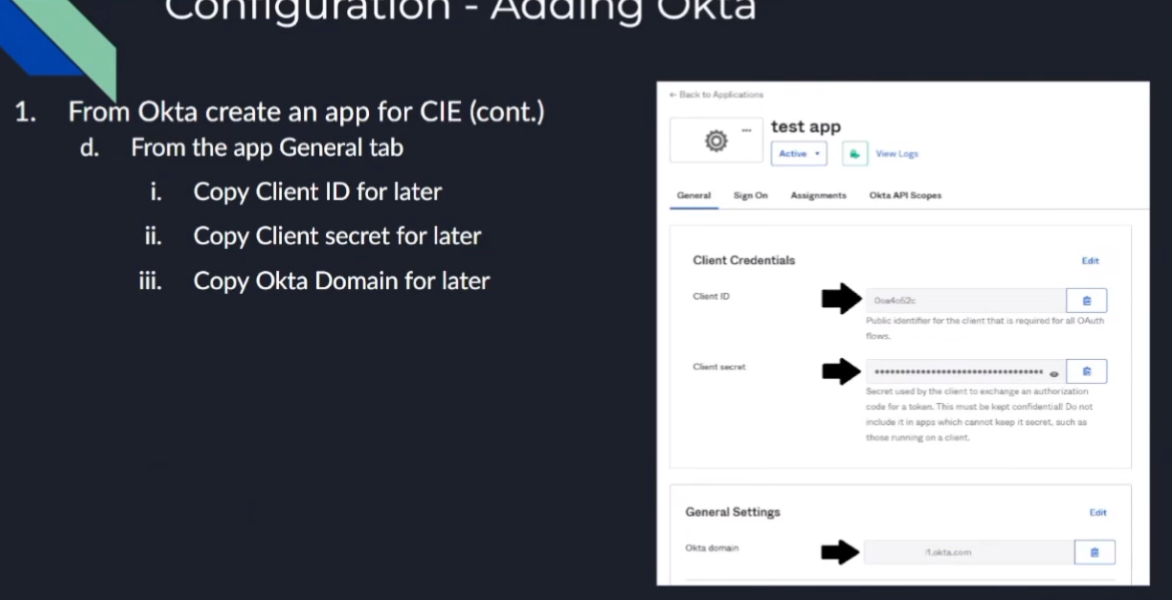
from next thing you're going to do once you create the app you're going to need to copy the client id to use mcie as well as the client secret and your domain
so once you have that the last thing we need to do is apply the app uh the api scopes so for the api scopes we need these to grant the permissions for these five
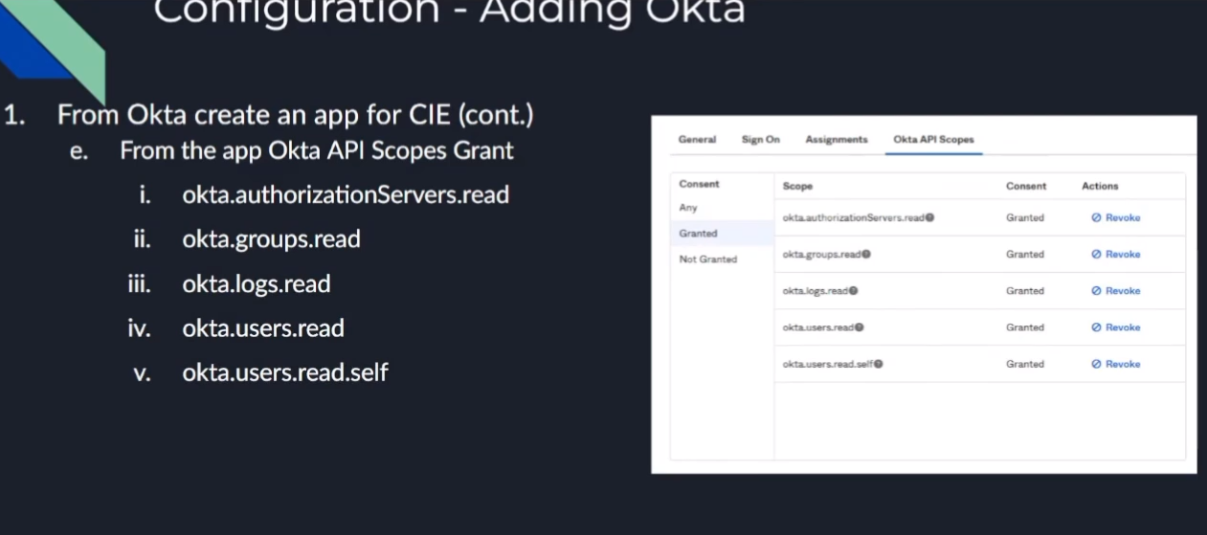
um i believe the first one's optional but refer to the documentation on when and where you would use it it's a it's a read one so i went ahead and just granted it here in this video so if the authorized servers read octa groups read logs read users read users read self
and so once you do that we're done with octa
so we can jump over to the cie portion and then from there on the cie portion
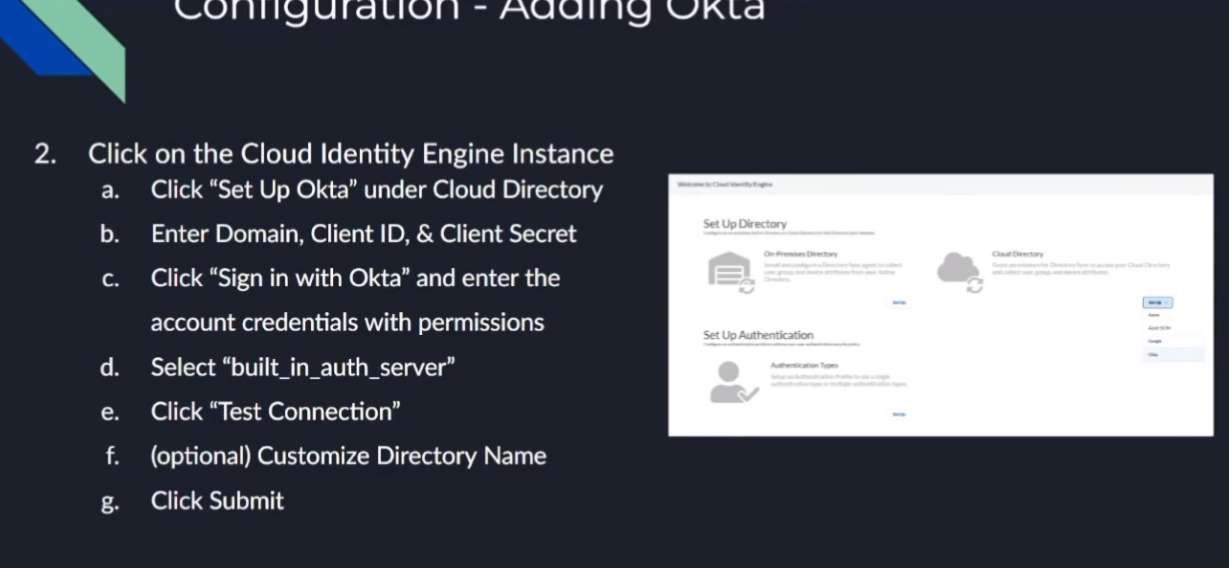
we're just going to click on the cloud directory and then set up octa we're going to enter the information you copied from earlier so the domain the client id the client secret and we're going to click sign in with octa and enter the permissions for the account that can do it
and then you're going to be given two different options use the built-in auth server unless you need to use the other one which is would be my recommendation and then click test connection
after that optionally give it a customized domain name uh or directory name sorry you'd want to do that if you have overlapping domains and then click submit
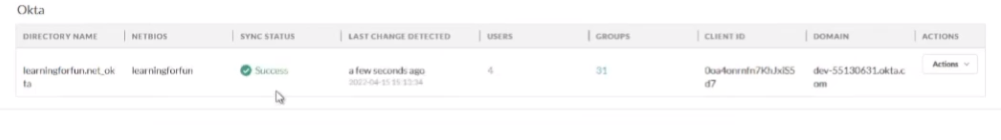
finally you'll be able to validate it worked because you'll have success users and groups
almost like you can validate all of them the exact same way all right so now we're going to go ahead and knock this one out as well
so here we are back at the hub go ahead and select our octa instance
and we're gonna go to cloud directory click on octa and there's that information we need
so we're gonna jump over to octa and i'm in my octa dashboard so i'm going to go to applications
i'm going to go ahead and create one
call that's my oidc connect and then web applicationand i'm going to call it step i'm going to click client credentials refresh
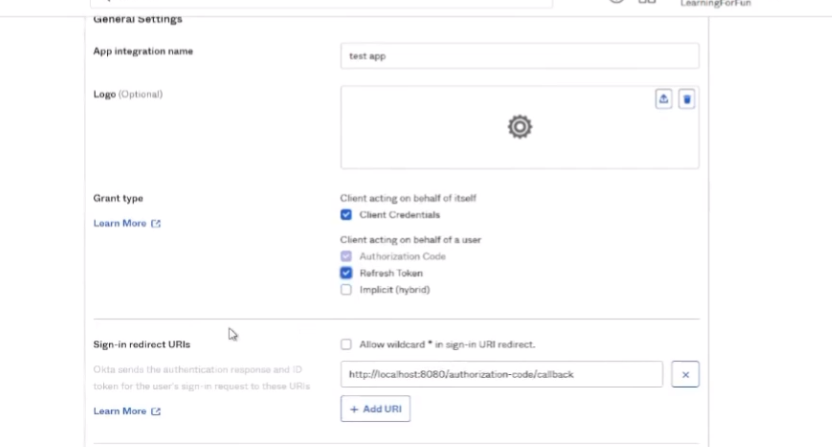
and then the sign in redirect url is for my region the us is what i'm going to paste in here
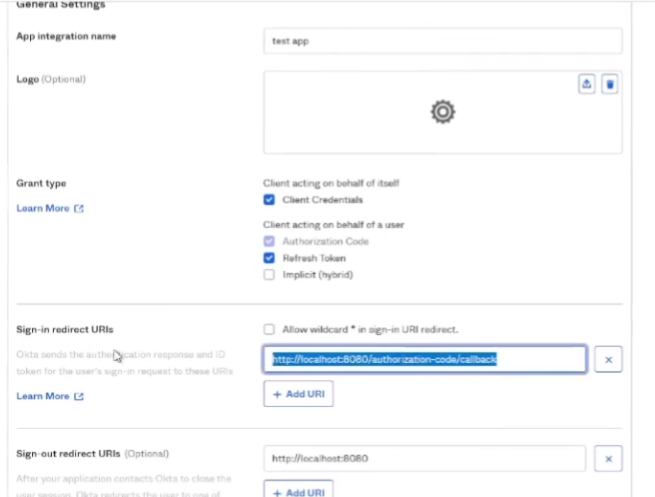
okay and then down below i'm going to allow everyone in my organization access
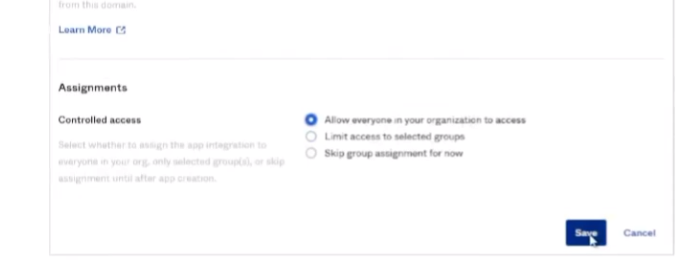
for this just for me for this video and then once i do that i'm going to click save
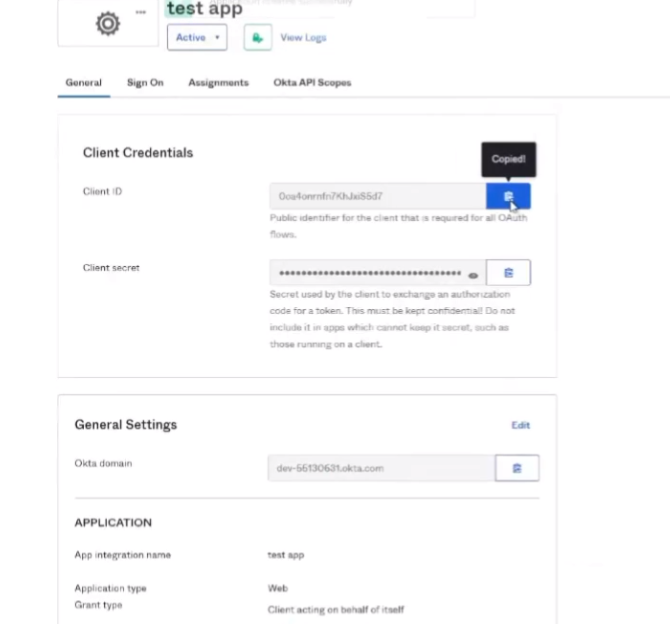
and under the general tab there's just three pieces of information so i'm going to go ahead and copy that client id all right and then i'm going to copy the secret and then i'm going to copy that octa domain i call it good
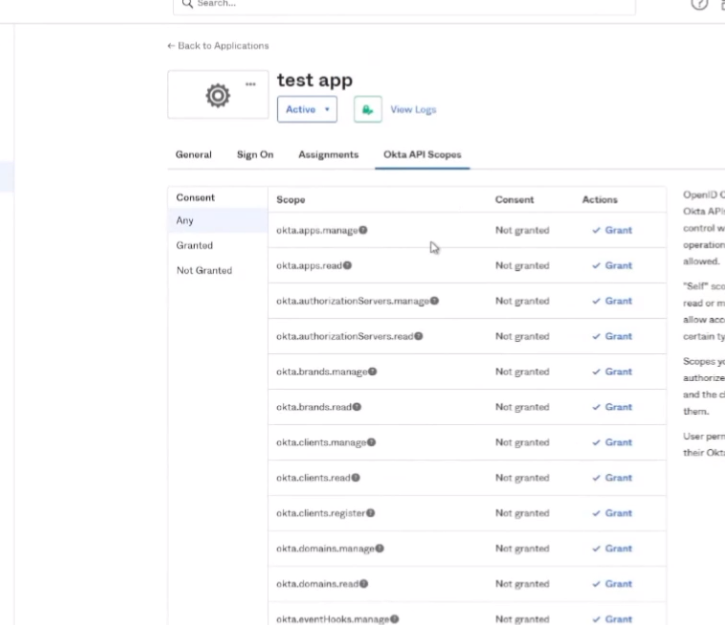
then i'm gonna go to the api scopes so the five that i need are let's go over to documentation here so tell us um there's that one that's optional so it's we have more than one authorization server so it's the authorization read e'll go ahead and just create that one and then achieve control effort and then there's the bottom box so i don't even need for that just right there all right so that should be all five I can check by looking at granted two three four five so i should be good
and it's activated already so there's my app i have everything i need so go back to the cie we're gonna put my domain in i'm going to put my client id in secret i'm going to sign in with octa
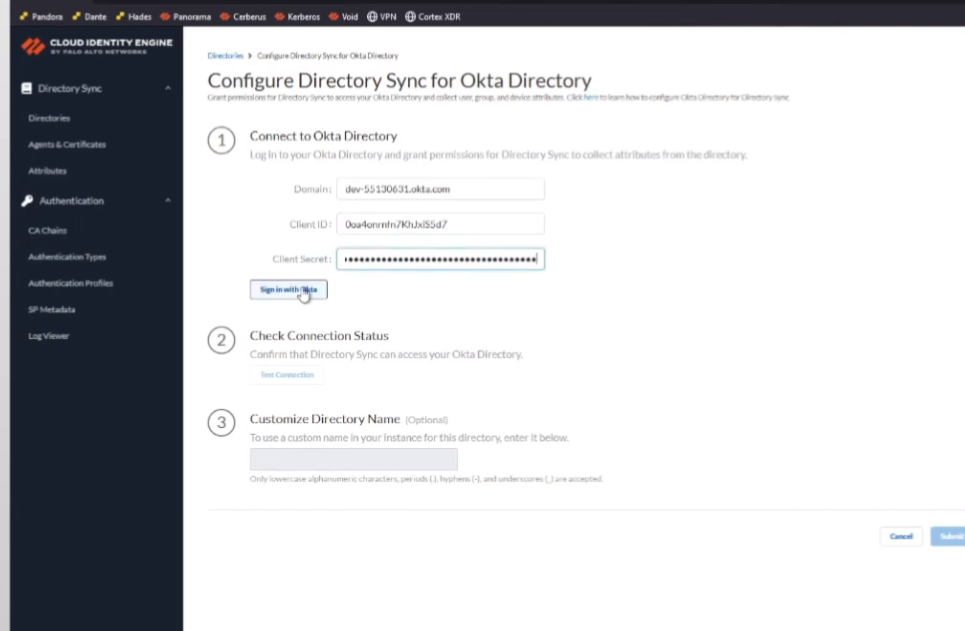
here's where we turn to off server so i'm going to use the built-in one and i'm going to go ahead and test that connection
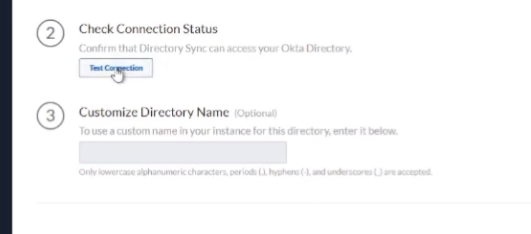
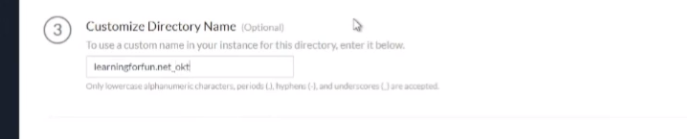
and it came back good so i'm going to go ahead and set up my dev i'm going to at underscore octa which could just take a little bit and it'll show up too just like the rest did there we are we see success users and groups
and there we have it that's octa all right so for the final portion i'm going to walk you through how to add it to your firewall and then how to add it to your cloud instances like a cloud managed panorama it's what i'm going to use but it's the same for anything else like cortex xdr
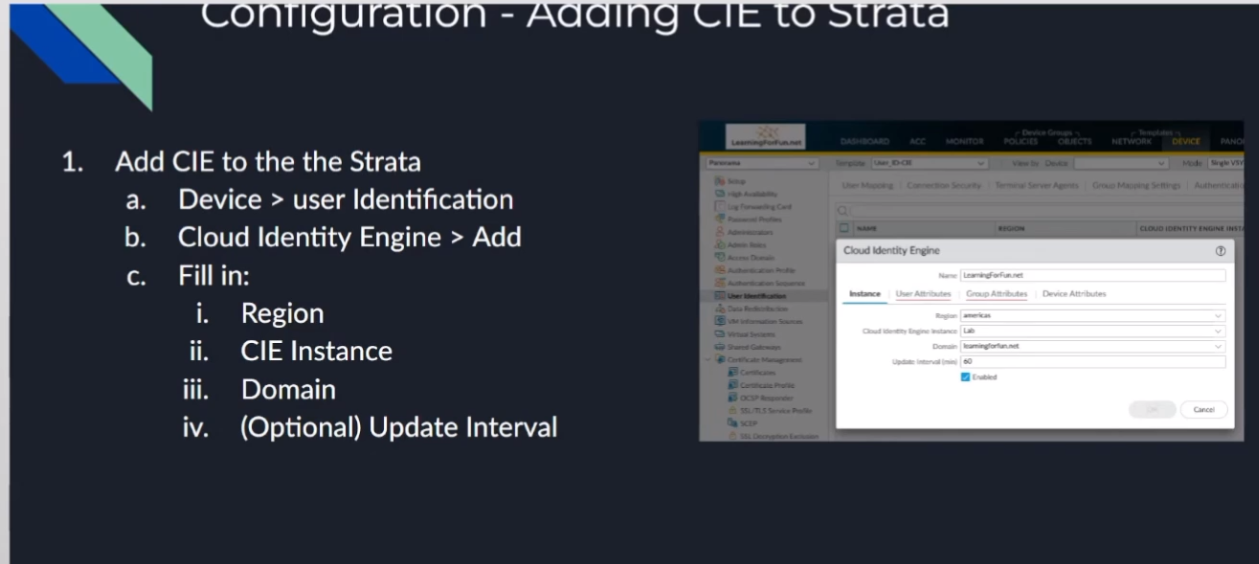
or your data lake everything like that so to add it we're going to log into either your firewall or panorama and then we're going to go under the device user identification cloud identification and ad and what you're going to do is you're going to give it a name and then you need to fill in the region that your cie is in the cie instance name that you gave it and then the domain that you want from it and so this is why it was critical if you have the same domain in different locations to give them a unique name unique name so you know which one you're dealing with from the drop down once we do that we need to tell it where do we want to map our user attributes from right so primary username my preferences use mail just because I see mail is unique across all these different elements um that works great now if you're doing something like uh azure skim and you choose not to send the mail over well that's not gonna work for you right so you need to to communicate a little bit with uh your organization if you're gonna be depending on the attributes but i found that mail works great and then upn works great for an alternate and then for groups distinguished name as a group name and mail as the email
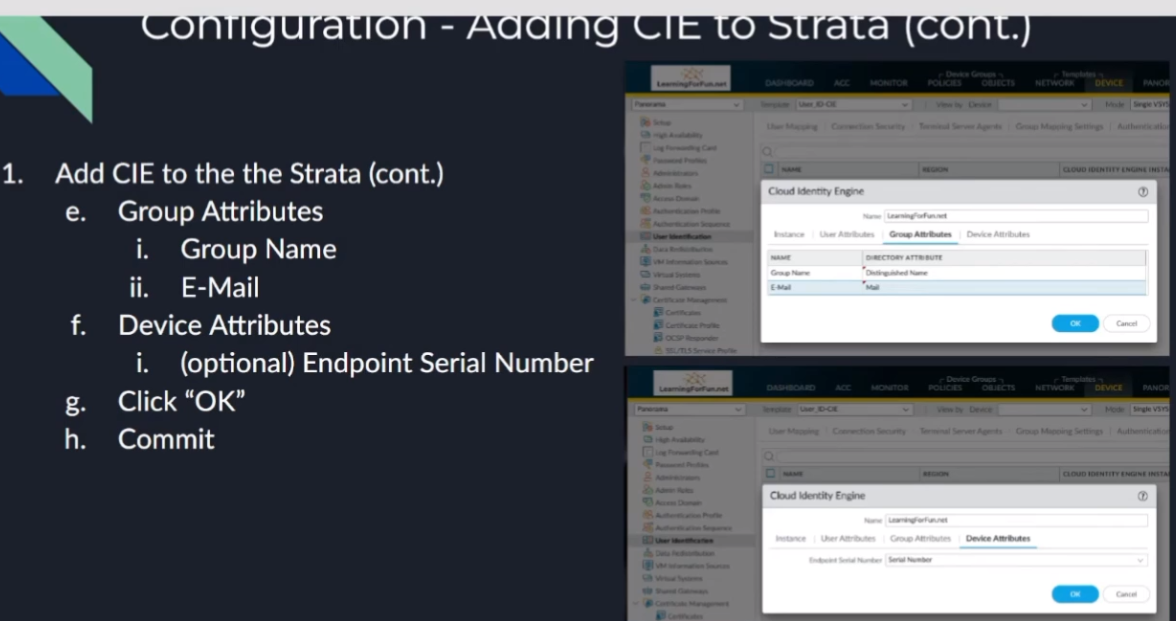
is pretty much never let me down and then under device attributes if you're if you're using that functionality serial number is your only option there so go ahead and set that click ok and then you would just commit it uh to your devices
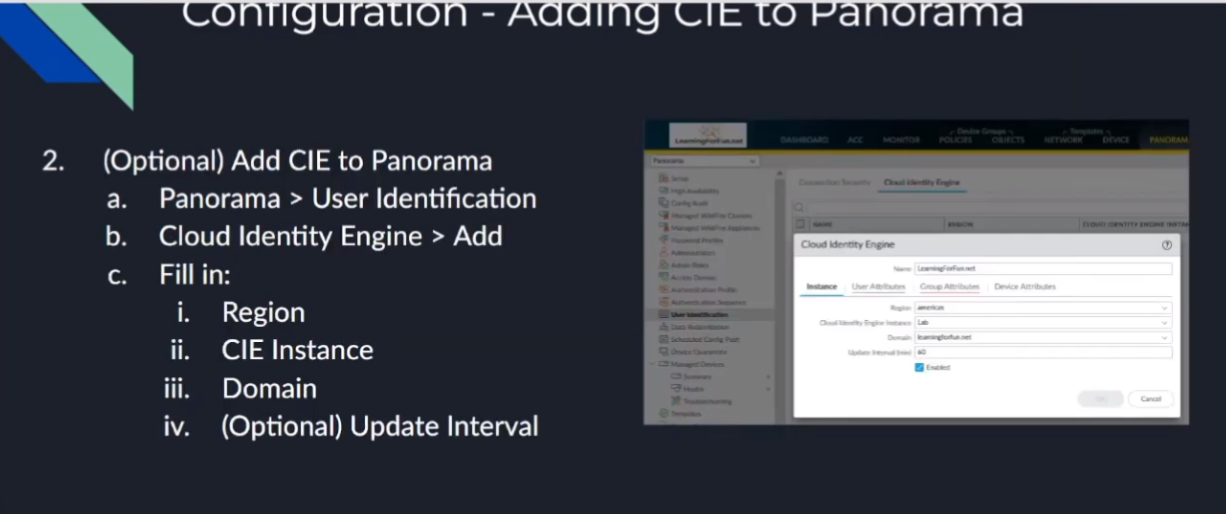
so if you're using panorama you're going to want to add this to panorama the same way that you're doing a master device for your user id information you're going to want to set that up in panorama as well so we're going to add the user id to panoramas under the panorama tab the same exact thing we did under the devices for the firewalls you're going to give it a name you're going to set the region you're doing your cloud instance your cie or your region your cie instance your domain the update interval you're going to give the mappings on the users same thing mail upn you're going to want to make sure these match between your devices in your panorama and then the same with your group attributes
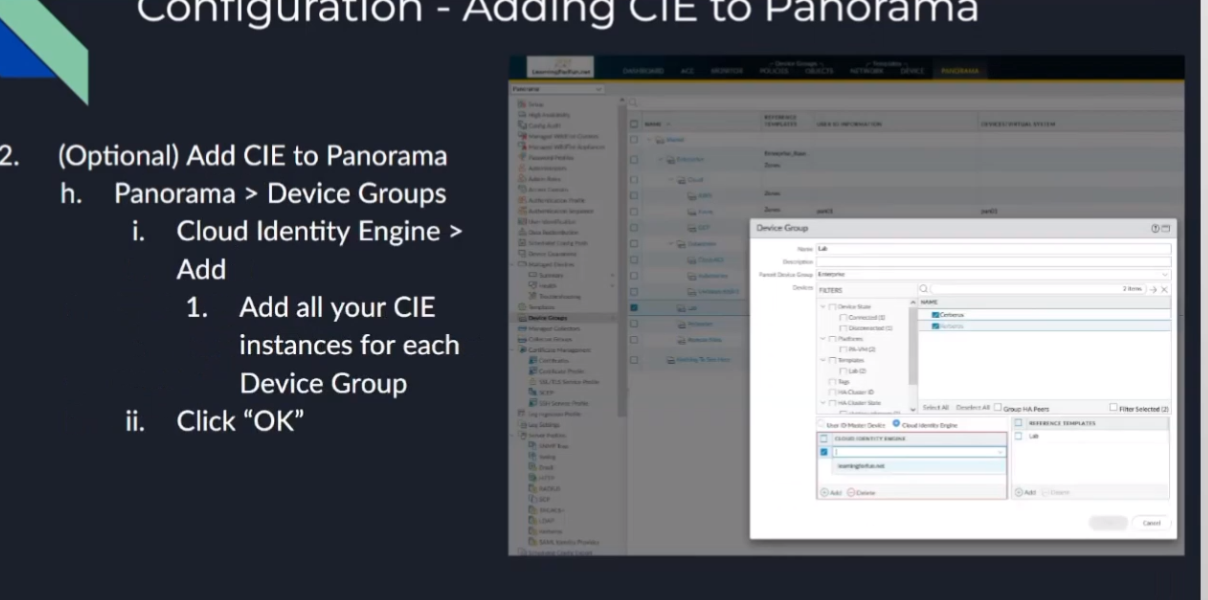
so you're also going to want to under your templates and your device groups this is very very important down below you'll see when you open up like your device group for example under user id master device is now the option for cloud identity engine once you move those devices over to cloud identity engine you're going to want to select your cloud identity engine that you just defined in panorama down there because that's going to tell you where to get the users and groups that those devices are going to be using so you're going to select it from the drop down list you can have multiple ones in there so if we have like learning for fun.net for my on-prem and then learning for fun.net um azure and then octa and google those would all show up down there because maybe i have different accounts and different ones synchronized or whatnot so i can have multiple ones show up there uh the id it's just critical that we do that you're going to do it under your device groups and your templates and it would be under your template stacks so all right and that's all there is to it
i'll do a quick walkthrough of that for you all right so i'm in panorama i'm going to go to my device and so i if you're in the firewall directly you don't have panoramic just could be right on your device if you're under panorama you can use whatever template template makes sense for you i like to use a modular template system so i have one that i call user id cie where when i'm ready to move do i server cie i just attach the template to the template stack and i'm good to go so but do whatever makes sense for you obviously so i'm going to go under user identification
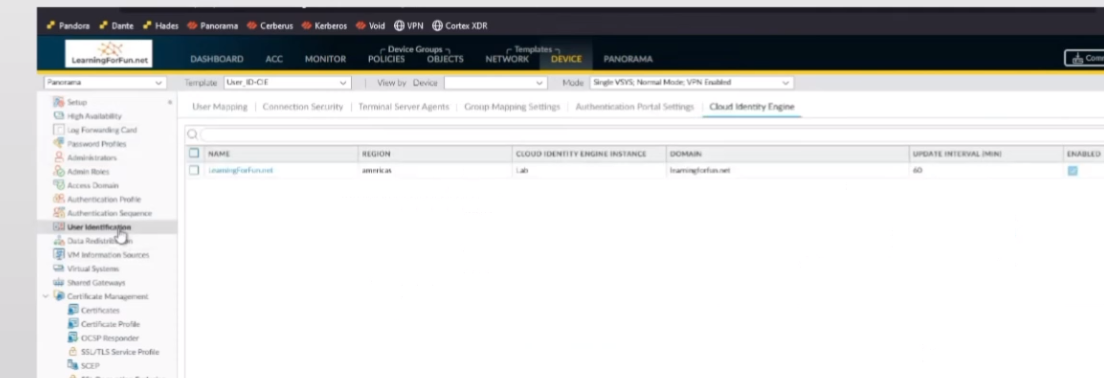
my cloud identity engine so i already have one that's added here that's lab but let's say i wanted to add a different one so we'll say learning fun dot net and we'll do um a jira so my instance here is america's and we'll do lab and then domain this is this is the one instance of cie
and i'll be able to show you this here in a second where i have all of them together so that's where they show up and so i'll go ahead and
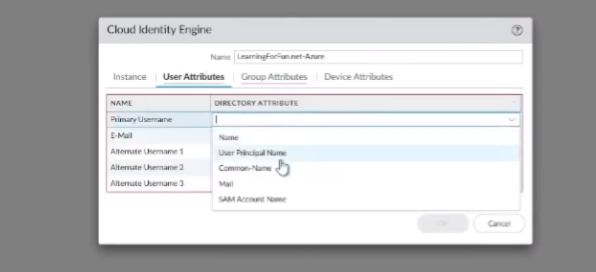
click azure i'll do my attributes right here so i'm going to do mail list my primary and ultimate is my upn my group is going to be distinguished name then email is mail go ahead and click device serial and i would just do this for all the rest of them that i have unique things
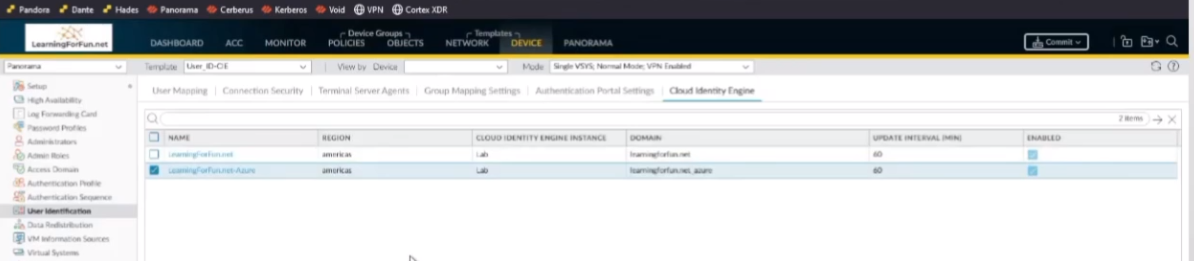
in for so and then since i'm using panorama i'm going to go over to panorama as well go over to user identification
and i'm going to add this one as well
so i'm going to go ahead and click add vpn it's the same exact thing as before it's super exciting i know but once we get it done it's done all right and so that's that's there so now the next thing we need to do is we're going to go under our device groups
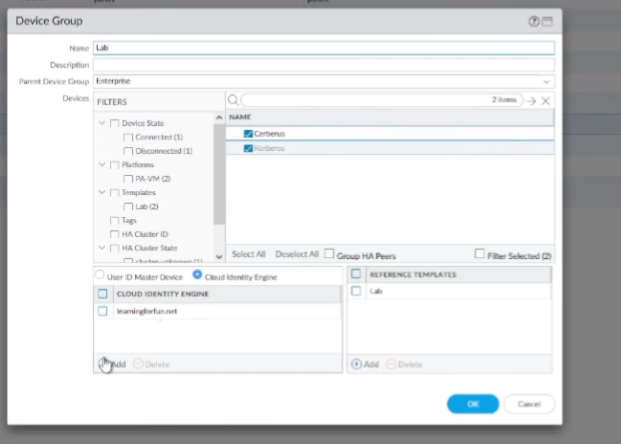
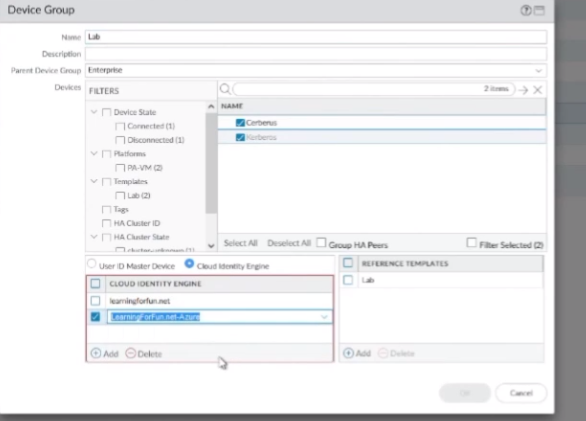
so i'm gonna pick my lab units here and so where i already have learning for fun.net now i'll have azure show up let me go ahead and click ok there
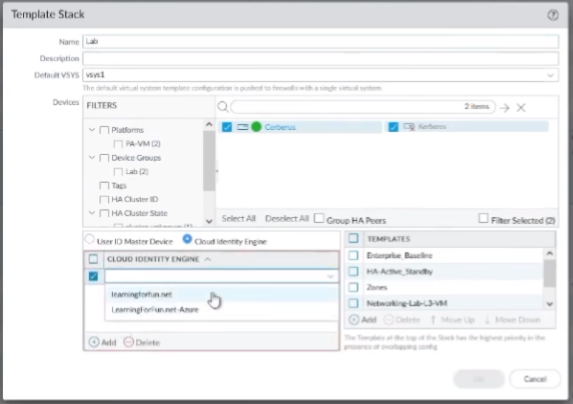
and then i'll want to go to my templates and then under my stack so my lab stack here i'll go to swap over the cloud identity engine and so i have both my learning for fun.net and then the azure one i just added i want to make sure i add those there so that i can use those groups under things under my templates so it would be there things like my portal and my gateway for my client configs so once i do that i can go ahead and hit commit and push the device and i'll go ahead and be sent out and that's really all there is to it for the
panorama side so now i'm going to swap back over and show you how to do it for your cloud services on the the lots of network cells so say that we already have prisma access identified or one of your other services
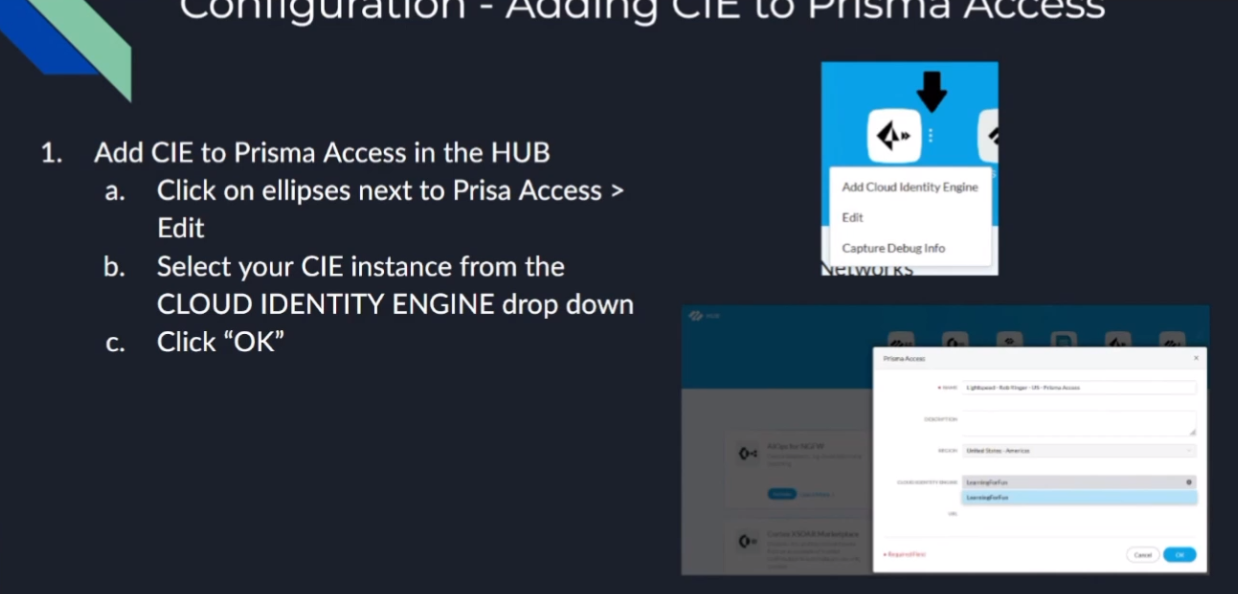
so all you have to do is click on the ellipses and you can click edit and then you'll see this section down below called cloud identity engine and then from the drop down you just select your instance name so what i'm going to do is go ahead and jump in and set that up for you so just one moment and walk you through it
all right so here i am here's my prisma access instance so i'm going to go ahead and click uh well i clicked add prisma access cloud in the engine
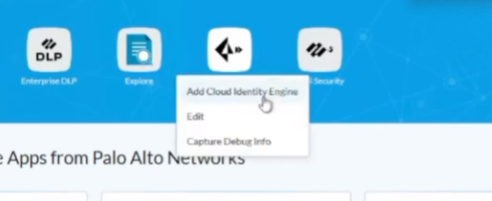
so that's one way to do it the other way would be to click edit and then we can see it shows up down here and i'm gonna click on my cloud identity engine and click ok
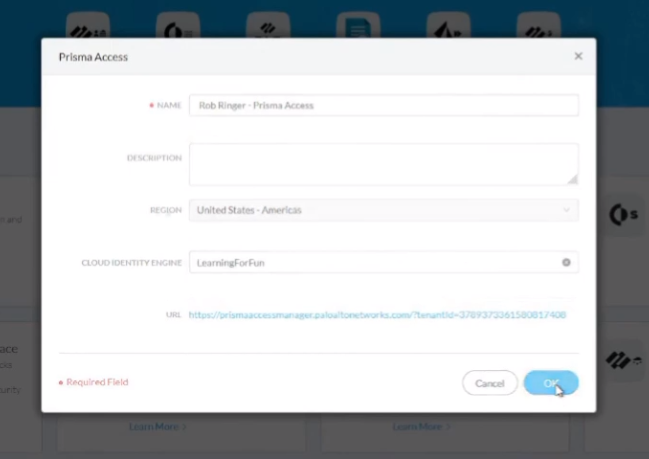
and once that's added i'll go ahead and jump into the prisms access real quick and show you what it looks like
into my cloud management access so it looks very similar to how it's set up on entering my right with our shared objects mobile users so everything that we're used to seeing before so we're global protect our remote users our apps are set up but the big thing is under identity services where we click on cloud identity engine this is where we do our mappings just like we were doing on the firewall
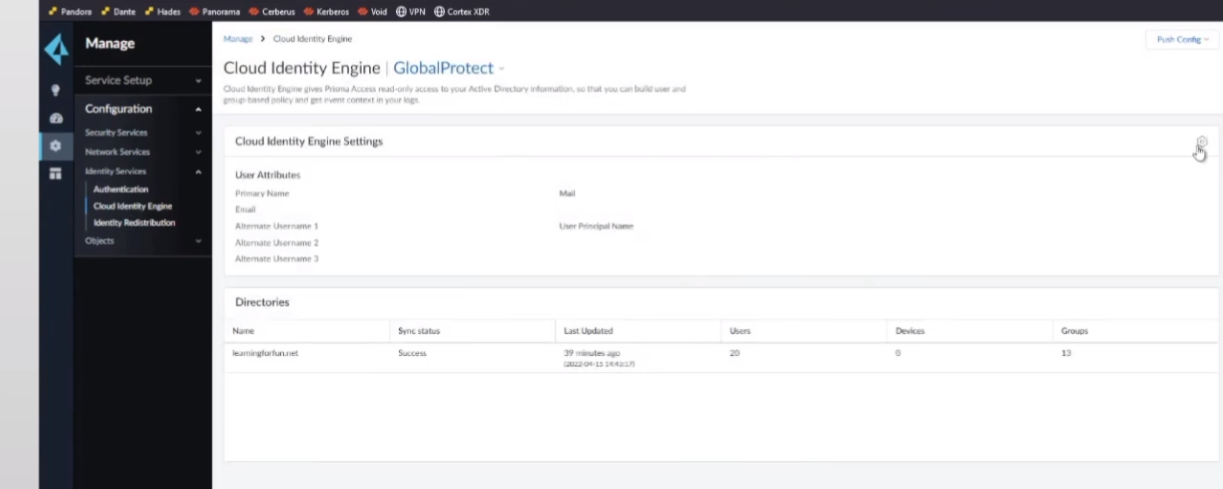
we see that we have mail and upn just like i was doing there then we see our directories and this is what we had linked um from the hub portal so now if i want to do any of my security policies just like i do under panorama i'm going to go ahead and add a rule and i'm going to go ahead and do basic based on users we can see all my groups show up there so if it's google google devices or anything else that i want to do here so rob bringer outlook which is one of my accounts this is an external third party
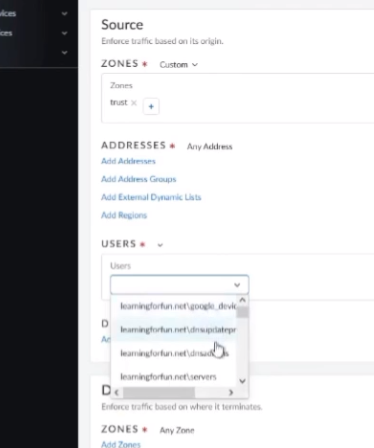
account um i just through azure that i integrated so it's that easy to be able to tie cie into both on your on-prem or your cloud instances