PAN-OS: GlobalProtect Device Quarantine - Detailed Guide
GlobalProtect makes it easier for you to block compromised devices from your network by identifying a compromised device with its Host ID and, optionally, serial number instead of its source IP address. This ability can be preferable to blocking a compromised endpoint from a network based on its IP address, because if a device’s IP address changes (for example, if a user moves their endpoint from a work location to their home), security policies based on IP addresses could allow the endpoint back on the network.
After you identify a device as compromised (for example, if a device has been infected with malware and is performing command and control actions), you can manually add the device’s Host ID to a quarantine list and configure GlobalProtect to prevent users from connecting to the GlobalProtect gateway from a quarantined device. You can also automatically quarantine the device using log forwarding profiles with security policies or HIP Match log settings .
Starting with Android 8.0 version, GlobalProtect app is unable to retrieve device serial number as GlobalProtect app is not device owner app or profile owner app. In this case, you can use ANDROID_ID as the device serial number. ANDROID_ID is application specific on an Android device and the ID may change when resetting your Android device to factory settings.
Prerequisites & Licensing
Before you begin to quarantine devices, make sure that your GlobalProtect users are running a minimum GlobalProtect app version of 5.1 (introduced PAN-OS 10.0, feature expanded in 10.2). In addition, make sure that a valid GlobalProtect subscription license is present on the firewall performing the quarantine action (adding devices to the list). The license requirements are enforced as follows:
- The firewall requires a GlobalProtect subscription license to manually or automatically add devices to the quarantine list. You receive the following error message if you attempt to add a device without a license: The device cannot be quarantined. You must have a valid GlobalProtect subscription to add the device to the quarantine list.
- However, you can delete quarantined devices from the quarantine list without a license.
- If your GlobalProtect subscription license expires, the quarantine list is retained and not deleted, but new devices cannot be added.
- GlobalProtect performs a license check hourly.
- If you do not have a valid GlobalProtect license and try to commit a configuration referencing the Quarantine List (in Data Redistribution or Log Forwarding), a warning message is displayed.
View Quarantined Device Information
You view quarantined device information from the Device Quarantine page:
-
On Next-Generation Firewalls: Select
Device > Device Quarantine. -
On Panorama Appliances: Select
Panorama > Device Quarantine.
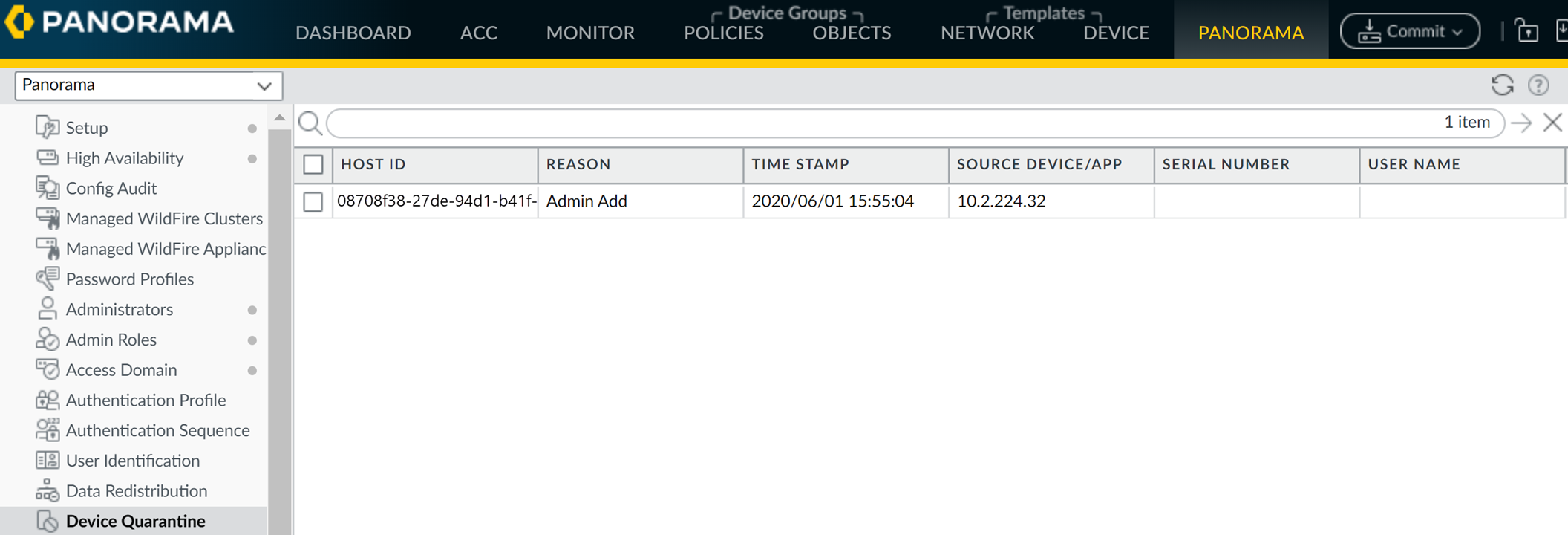
- You can also view GlobalProtect quarantine activity from the ACC . The GlobalProtect Quarantine Activity tab displays a chart summarizing quarantined devices by action, reason, and location.
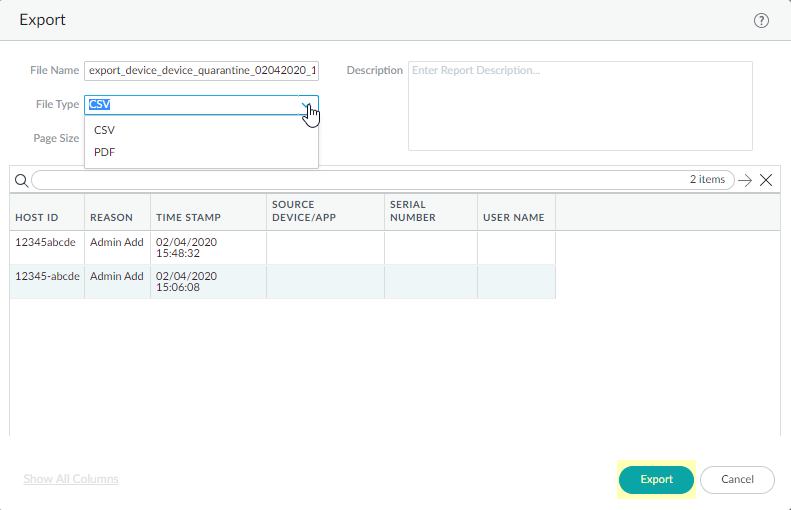
- To export the list to a PDF or CSV file, select PDF/CSV at the bottom of the Device Quarantine page.
Manually Add and Delete Devices From the Quarantine List
You can add a device manually from the quarantine page, from specific logs, or via the API. Deletion is done from the quarantine page.
-
From Device Quarantine Page:
Select
Device > Device Quarantine(orPanorama > Device Quarantine) and click Add . Enter the Host ID and optionally the Serial Number .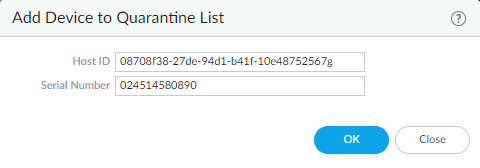
-
From Logs (GlobalProtect, Threat, Traffic, Unified):
-
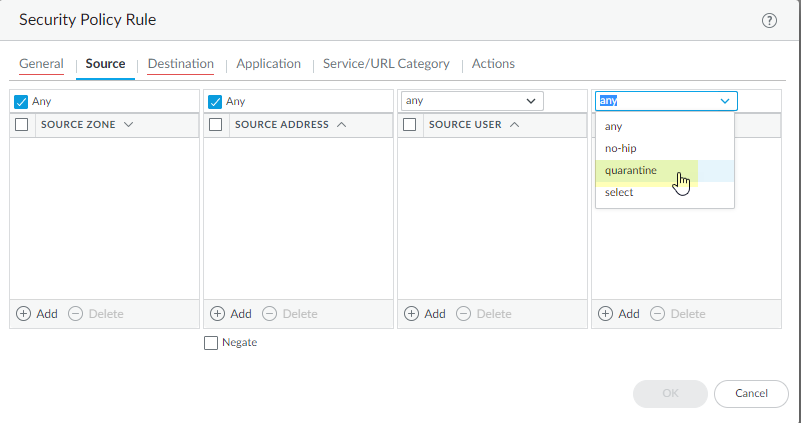
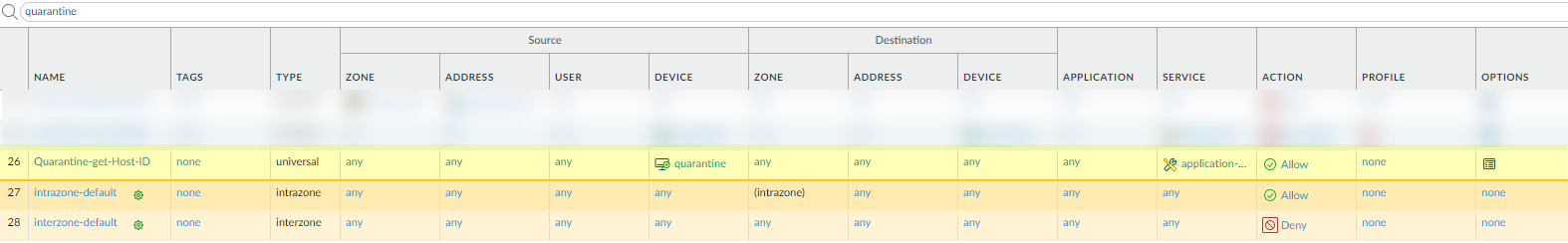
(For Threat/Traffic/Unified Logs) Enable Host ID Logging:
Ensure Host ID information is included in these logs. Create a Security Policy rule (it can be permissive, e.g., allow any/any) and set the
Source Device
to
Quarantine
on the Source tab. This ensures the firewall populates the Host ID field in relevant logs.
-
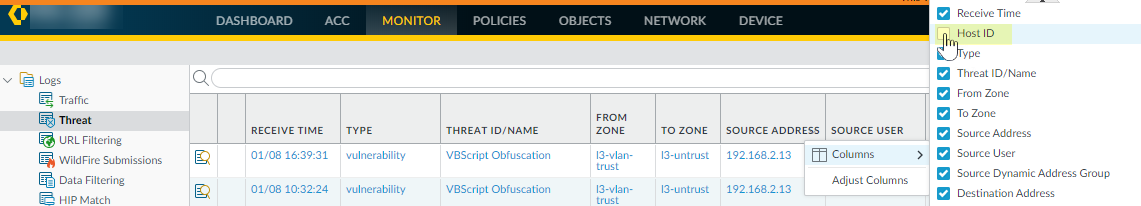
Navigate to the relevant log (
Monitor > Logs). -
Ensure the
Host ID
column is visible (add it via the column selector if needed).
-
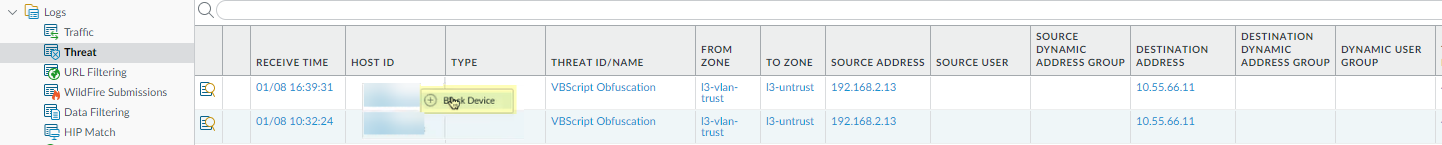
Right-click the
Host ID
of the device you want to quarantine and select
Block Device
.
-
(For Threat/Traffic/Unified Logs) Enable Host ID Logging:
Ensure Host ID information is included in these logs. Create a Security Policy rule (it can be permissive, e.g., allow any/any) and set the
Source Device
to
Quarantine
on the Source tab. This ensures the firewall populates the Host ID field in relevant logs.
-
Finding the Host ID:
If you only know the username, you can find the Host ID in the HIP Match logs (
Monitor > Logs > HIP Match). Filter for the user, open a log entry, and find the Host ID underOS > Host ID. - Via API: Use the XML API or REST API to add/delete devices from the quarantine list programmatically. Refer to the API Usage Guide .
-
Deleting Devices:
Select the device(s) on the
Device Quarantinepage and click Delete . This is typically done after remediation.
Host ID Values by OS:
-
Windows: Machine GUID from Registry (
HKEY_Local_Machine\Software\Microsoft\Cryptography\MachineGuid) - macOS: MAC address of the first built-in physical network interface
- Android: Android ID
- iOS: UDID
- ChromeOS: GlobalProtect assigned unique alphanumeric string (32 characters)
Automatically Quarantine a Device
Automation uses Log Forwarding Profiles or HIP Match Log Settings.
-
Using Log Forwarding Profile:
-
Go to
Objects > Log Forwardingand Add/Edit a profile.
- Add a Log Forwarding Profile Match List entry.
- Set the Log Type (e.g., Threat, Traffic, GlobalProtect).
-
Define a
Filter
for the trigger condition (e.g.,
(severity eq critical)for Threat logs). -
Under
Built-in Actions
, click Add and select
Quarantine
. Optionally set a
Timeout
.
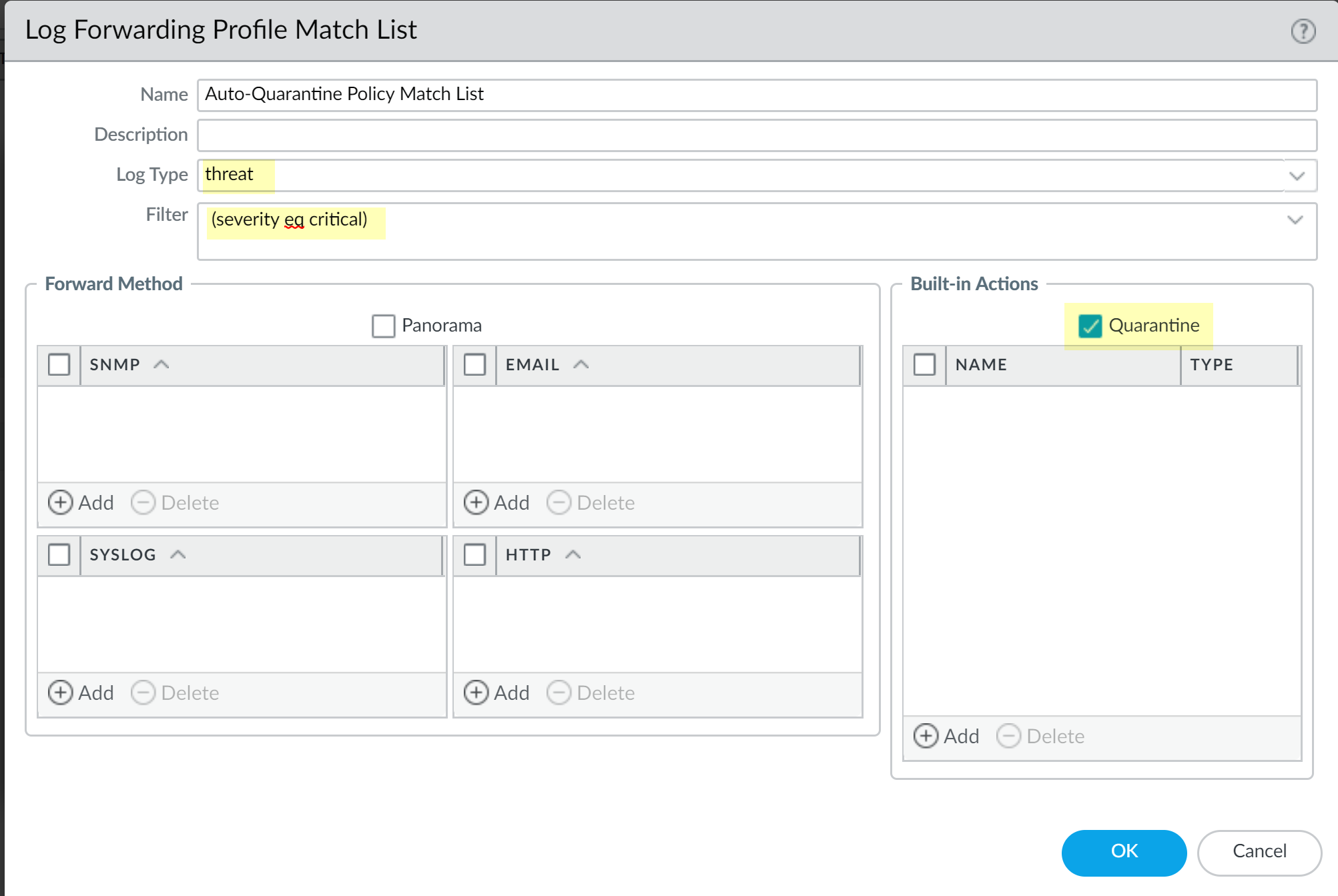
Remember, if using Threat or Traffic logs, the Host ID must be present (requires the Security Policy rule with Quarantine as Source Device, mentioned earlier).
-
Confirm the profile shows Quarantine under Built-in Actions.
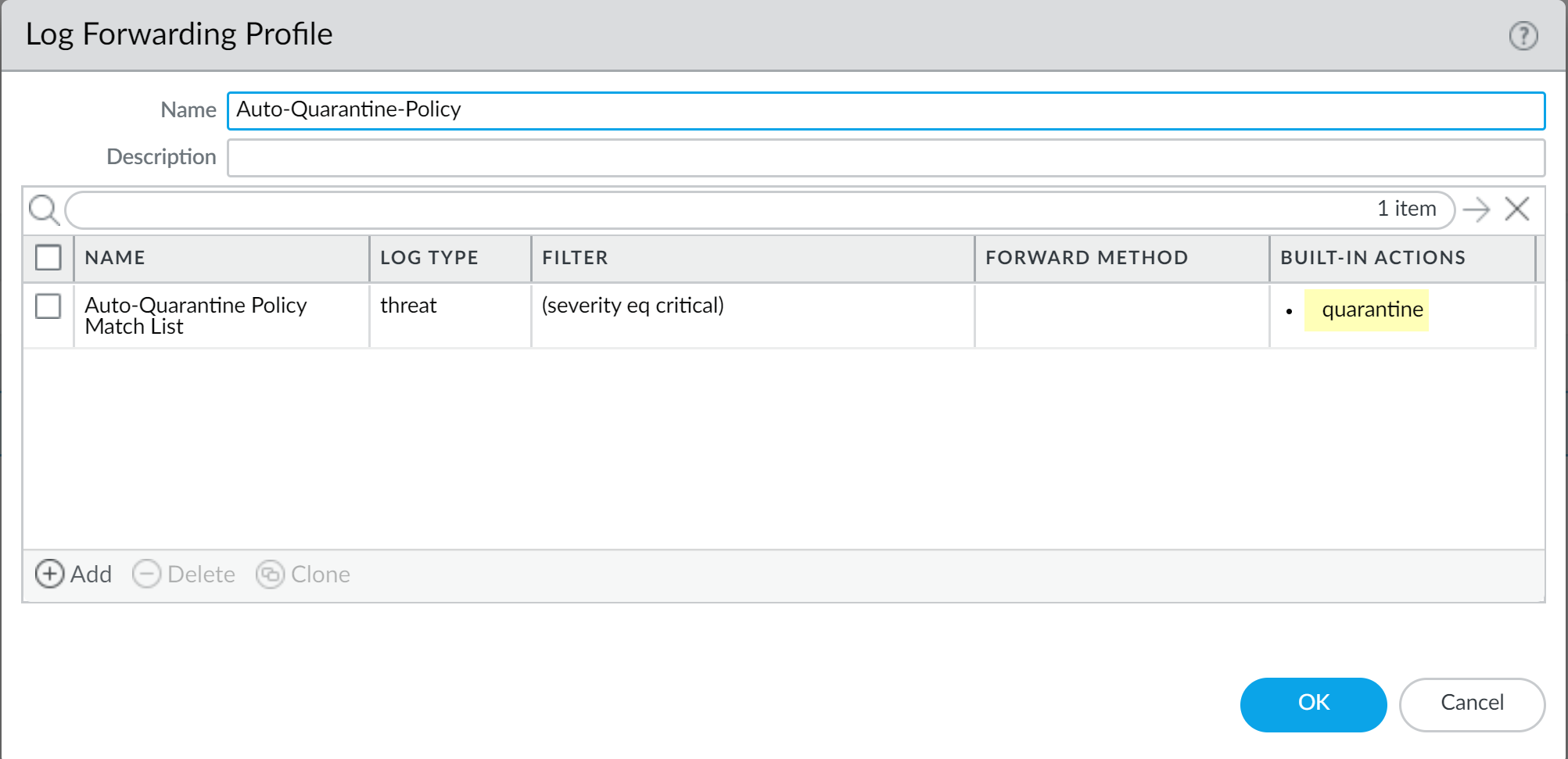
-
Assign this Log Forwarding profile to the relevant Security Policy rule(s) under the
Actions
tab.
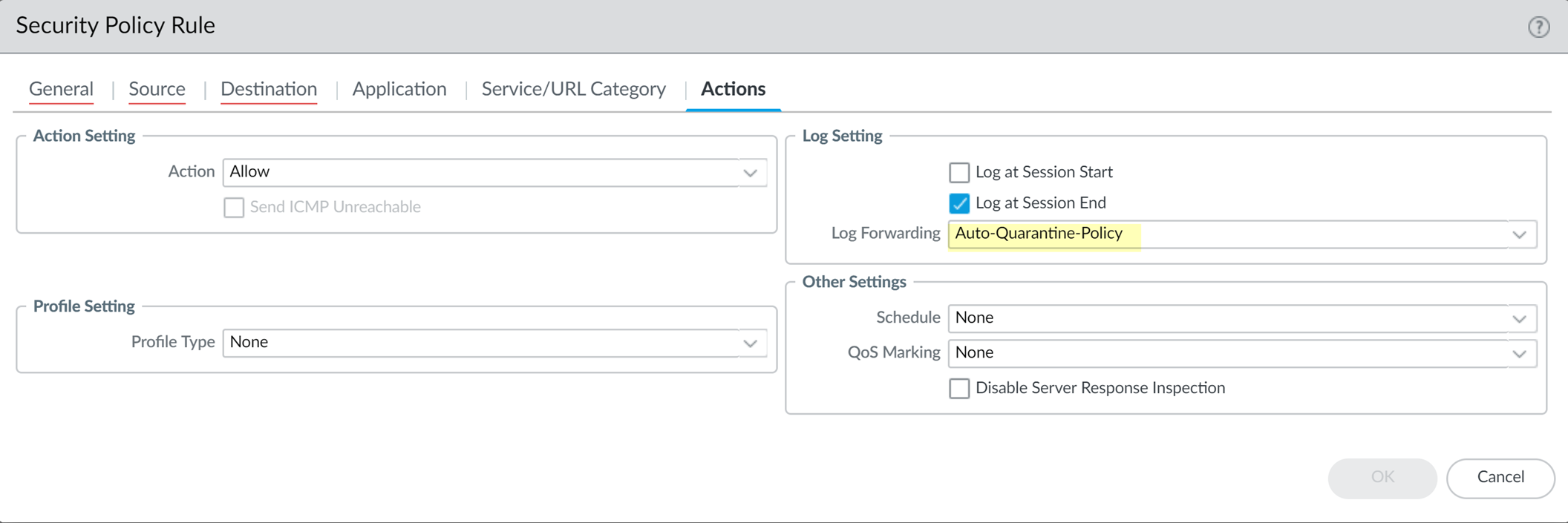
-
Go to
-
Using HIP Match Log Settings:
-
Go to
Device > Log Settings > HIP Matchand Add/Edit a setting. - Define a Filter based on HIP Match log fields (e.g., matching a specific Host ID known to be problematic, or a failed HIP check).
- Under Built-in Actions , Add the Quarantine action. Optionally set a Timeout.
-
This method does *not* need to be attached to a Security Policy; it acts directly on HIP Match logs.
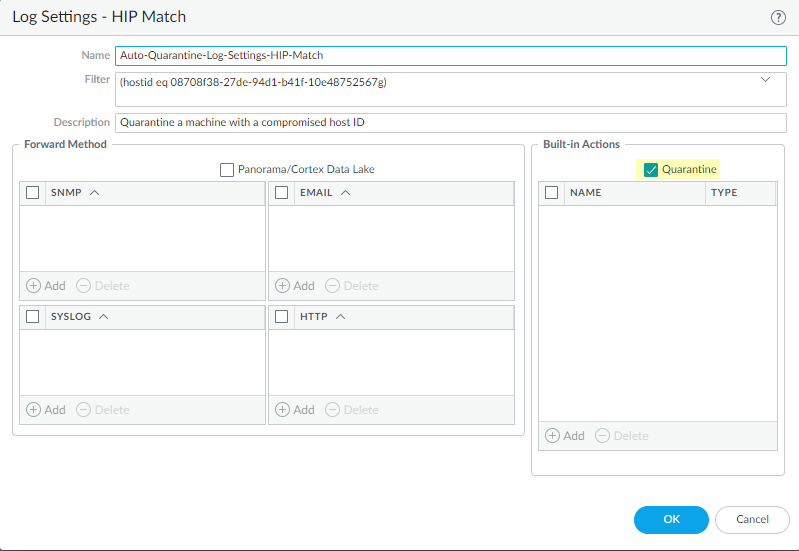
-
Go to
Use GlobalProtect and Security Policies to Block Access
Once a device is quarantined, you block its access:
-
Block GlobalProtect Login:
-
Go to
Network > GlobalProtect > Gateways > [Your Gateway] > Agent > Client Settings > [Your Config] > Data Collection. -
Check the box for
Block login for quarantined devices
.
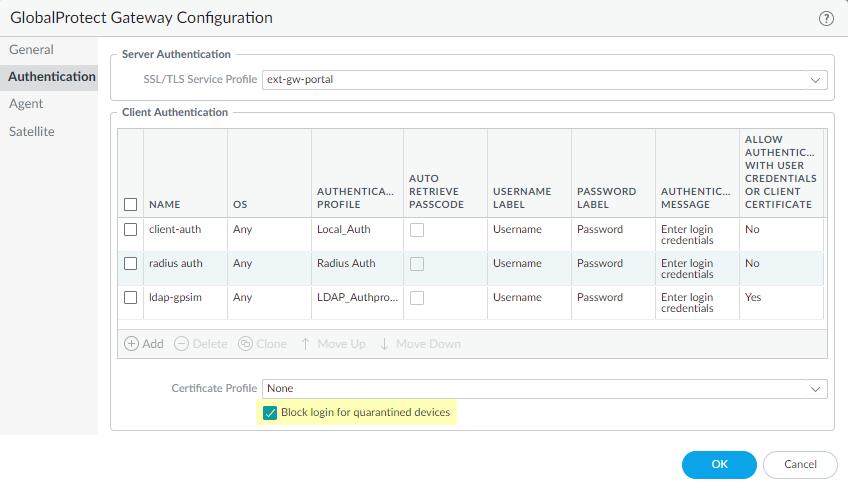
- Users attempting to log in from a blocked device will receive a notification in the GP app.
- Note: If this setting is *not* enabled, the user gets the notification but can still log in.
-
Go to
-
Block Network Access via Security Policy:
-
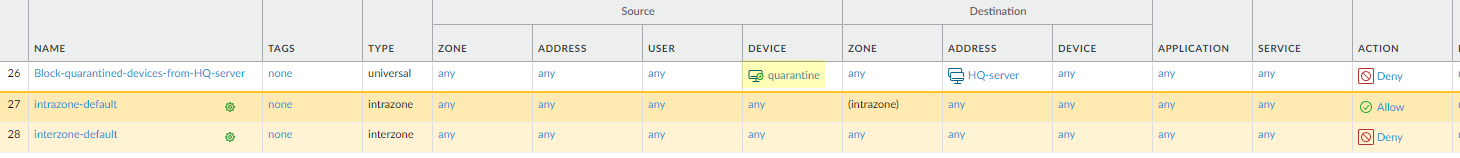
Create a Security Policy rule (
Policies > Security). - On the Source tab, set Source Device to Quarantine .
- Set other criteria (Destination Zone, Address, Application, etc.) as needed.
-
Set the
Action
to
Deny
.
- For this policy to work effectively, the user must have successfully logged into a GlobalProtect gateway *from the quarantined device at least once* while the device was quarantined (and the "Block login" setting was OFF for that login), so the firewall registers the device/user mapping associated with the quarantined Host ID. This mapping can then be redistributed.
-
Create a Security Policy rule (
Redistribute Device Quarantine Information from Panorama
Panorama can act as a central repository for the quarantine list and distribute it to managed firewalls using User-ID Redistribution.
-
Enable User-ID on Panorama Interface:
Ensure User-ID redistribution is enabled on the Panorama interface used to communicate with redistribution agents (
Device > Setup > Interfaces > Managementor a dataplane interface viaNetwork > Interface Mgmt).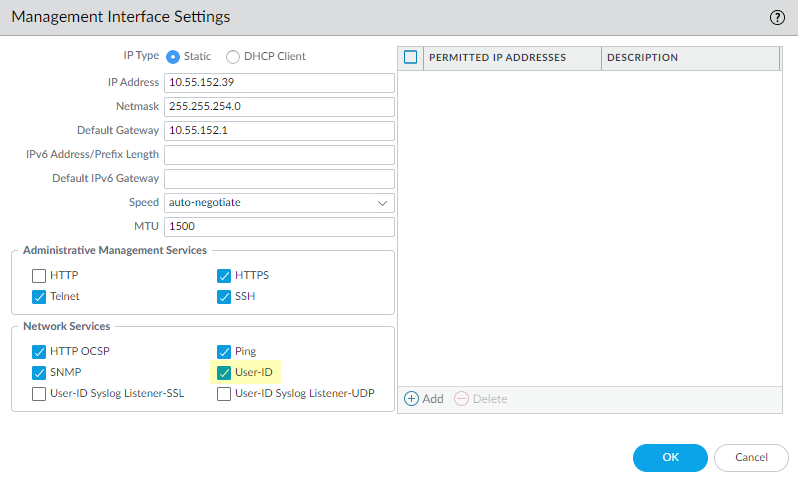
-
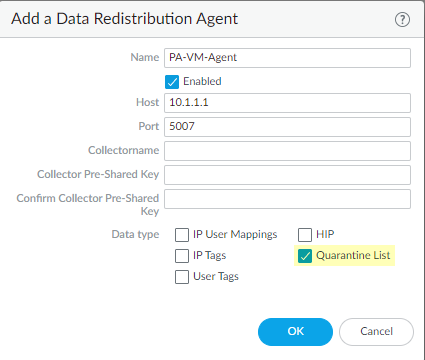
Configure Data Redistribution Agent:
-
Go to
Panorama > Data Redistribution. - Click Add to create an agent configuration.
- Specify the managed firewalls/gateways (Servers) that should receive the data.
-
Under
Data Type
, select
Quarantine List
.
-
Go to
- Commit changes to Panorama and push to relevant Device Groups.
Visual Flows: Device Quarantine
Flow 1: Automatic Quarantine via Logs
sequenceDiagram
participant Device as Device (GP Agent)
participant FW_Pano as Firewall/Panorama (Policy & List Mgmt)
participant GP_GW as GlobalProtect Gateway
Note over Device, FW_Pano: Initial State: Device is NOT Quarantined
Device->>+FW_Pano: Sends traffic triggering policy/threat (e.g., malware detected)
FW_Pano->>FW_Pano: Generate Log (e.g., Threat Log) containing Source Host ID
Note over FW_Pano: Log is forwarded/evaluated based on Log Forwarding Profile or Log Setting
FW_Pano->>FW_Pano: Filter defined in Profile/Setting Matches Criteria
FW_Pano->>FW_Pano: Execute Built-in Action: Add Host ID to Device Quarantine List
Note over FW_Pano: Device is now marked as Quarantined internally
deactivate FW_Pano
Note over Device, GP_GW: Later... Device attempts VPN connection
Device->>+GP_GW: Initiate GlobalProtect Connection (Sends Host ID)
GP_GW->>GP_GW: Receive connection request & Host ID
Note over GP_GW: Check Gateway Config: "Block login for quarantined devices" is Enabled
GP_GW->>GP_GW: Check received Host ID against Quarantine List
alt Host ID Found in Quarantine List
GP_GW-->>-Device: Block Connection (Device Quarantined Notification)
else Host ID NOT Found
GP_GW->>Device: Proceed with normal Authentication/Connection (if other checks pass)
end
Flow 2: Manual Quarantine by Administrator
sequenceDiagram
participant Admin
participant Device as Device (GP Agent)
participant FW_Pano as Firewall/Panorama (Policy & List Mgmt)
participant GP_GW as GlobalProtect Gateway
Note over Admin, FW_Pano: Admin identifies problematic device & obtains Host ID
Admin->>+FW_Pano: Manually Add Host ID to Device Quarantine List (GUI/CLI/API)
FW_Pano-->>Admin: Confirm Host ID added
deactivate FW_Pano
Note over FW_Pano: Device is now marked as Quarantined
Note over Device, GP_GW: Later... Device attempts VPN connection
Device->>+GP_GW: Initiate GlobalProtect Connection (Sends Host ID)
GP_GW->>GP_GW: Receive connection request & Host ID
Note over GP_GW: Check Gateway Config: "Block login for quarantined devices" is Enabled
GP_GW->>GP_GW: Check received Host ID against Quarantine List
alt Host ID Found in Quarantine List
GP_GW-->>-Device: Block Connection (Device Quarantined Notification)
else Host ID NOT Found
GP_GW->>Device: Proceed with normal Authentication/Connection
end