Connect the Dynamic Privilege Access Enabled Prisma Access Agent to a Different Server
An instance of the Prisma Access server is also known as a tenant . If your administrators set up multiple Prisma Access servers, you can connect to a different server to access the network or the resources through that server.
For example, you need to work on a different project, but that project is only accessible on a different server. You will need to connect to that server before you can change to that project.
- Launch the Prisma Access Agent by clicking the Prisma Access Agent icon
![]()
from the macOS menu bar or Windows taskbar.
- Edit the server settings by selecting the server management icon.
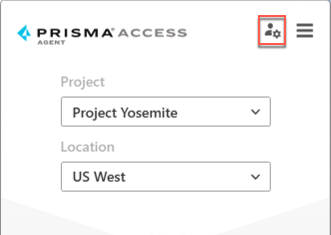
- The server information appears showing the server that you're connected to. If other servers are listed, you can select one and Connect to it.
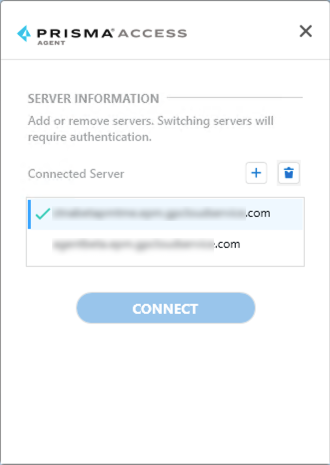
- If you need to add a server, complete the following steps:
- Click the + sign.
- Enter the new server name (provided by your administrator) and Add it.
The format of the server name is <xxx>.epm.gpcloudservice.com without the https:// . The maximum length of the server name is 256 characters. The maximum number of servers allowed on this page is 20.
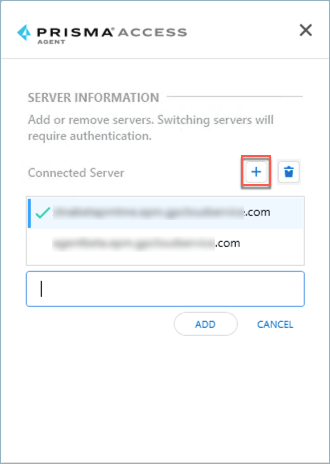
- After adding the server, select it and click Connect .
- When the Confirmation window appears, click Yes to disconnect from the current server and connect to the other server. You will need to provide your sign-on credentials again.
- When prompted, log in to the new server by providing the project name (if applicable).
Disable the Dynamic Privilege Access Enabled Prisma Access Agent
If your administrator allows it, you can temporarily disable the Prisma Access Agent. This is helpful on devices where other secure access apps, such as the GlobalProtect app, coexists with the Prisma Access Agent. In this case, you will have to disable the Prisma Access Agent before you can switch to the other app.
After you disable the Prisma Access Agent, the agent is in the disabled state, where:
- All traffic to Prisma Access locations are disabled, and multi-factor authentication (MFA) is disabled.
- Communication with the server persists so the agent can continue to receive upgrades, remote shell requests from the administrator, and perform HIP checks.
- If configured by the administrator, the anti-tamper feature will continue to function to protect the agent from unauthorized tampering.
- On macOS devices, the system and network extensions for Prisma Access Agent will continue to be active, and the content filter will also continue to be active.
- Connecting to another server reenables the Prisma Access Agent automatically.
To disable the Prisma Access Agent:
- Open the Prisma Access Agent app by clicking the Prisma Access Agent icon
![]()
in your taskbar.
If you're disabling the agent for the first time or if you don't see the Disable link in the settings page, sign out of the Prisma Access Agent.
- Select the hamburger menu and select Sign Out .
- Log in to the Prisma Access Agent app again to make the Disable link appear in the settings window.
- Click the hamburger menu to open the settings window.

- Disable the Prisma Access Agent.
- Close the settings window by clicking the X .
The Prisma Access Agent is disabled.
- To reenable the Prisma Access Agent:
- Open the Prisma Access Agent.
- Select the hamburger menu and Enable the Prisma Access Agent.
The Prisma Access Agent functionality will resume.
Switch Between the Prisma Access Agent and GlobalProtect App
In some organizations, the Prisma Access Agent is installed on user devices that already have the GlobalProtect app installed. After installing the Prisma Access Agent, you can switch between the Prisma Access Agent and the GlobalProtect app as needed.
After switching to the GlobalProtect app, the Prisma Access Agent is in the disabled state. In the disabled state:
- All traffic to Prisma Access locations are disabled, and multi-factor authentication (MFA) is disabled.
Both Prisma Access Agent and GlobalProtect use the same GlobalProtect port to listen to MFA requests (for additional authentication for certain applications), but only one agent can use the port at a time. When you disable the Prisma Access Agent, the port will be released for use by GlobalProtect.
- Communication with the server persists so the agent can continue to receive staged rollout upgrades, ADEM notifications, remote shell requests from the administrator, and perform HIP checks.
- If configured by the administrator, the anti-tamper feature will continue to function to protect the agent from unauthorized tampering.
- On macOS devices, the system and network extensions for Prisma Access Agent will continue to be active, and the content filter will also continue to be active.
- If you switch to another server, the Prisma Access Agent will be re-enabled automatically. If the you try to connect to a Prisma Access location while the agent is disabled, the agent will connect to the best location.
You can use either the Prisma Access Agent app or the Prisma Access command-line tool (PACli) to switch between the two apps.
Before switching to the GlobalProtect™ app, you need to disable the Prisma Access Agent. If your administrator configured the feature to allow users to disable the Prisma Access Agent, you can use the app to disable the Prisma Access Agent. After you disable the Prisma Access Agent, you can start the GlobalProtect app.
Your administrator must contact the Palo Alto Networks team to enable this tenant-level feature. It's not available as an agent setting on Strata Cloud Manager.
- To switch from the Prisma Access Agent to the GlobalProtect app:
- Open the Prisma Access Agent.
If you're disabling the agent for the first time, open the Prisma Access Agent app and sign out of the Prisma Access Agent.
- Select the hamburger menu and select Sign Out .
- Log in to the Prisma Access Agent app again to make the Disable link appear in the preferences window.
- Click the hamburger menu to open the preferences window.

- Disable the Prisma Access Agent.

- Close the preferences window by clicking the X .
The Prisma Access Agent is disabled.

- Start the GlobalProtect app and Connect to GlobalProtect.
- To switch from the GlobalProtect app back to the Prisma Access Agent:
- Open the GlobalProtect app.
- Click the options menu and select Disconnect .
- Launch the Prisma Access Agent app.
- Click the hamburger menu to open the preferences window.

- Enable the Prisma Access Agent.

- Close the preferences window by clicking the X .
- If the agent is in Always On mode, the agent is enabled and will connect to the best location.
If the agent is in On-Demand mode, the Prisma Access Agent is enabled but remains disconnected. Click the lock icon to connect to the Prisma Access location.
View and Monitor Dynamic Privilege Access Users
Dynamic Privilege Access enables Prisma Access to apply different network and Security policy rules to mobile user flows based on the project your users are working on. Go to InsightsUsers in the Strata Cloud Manager Command Center to view user-based access information in your environment.
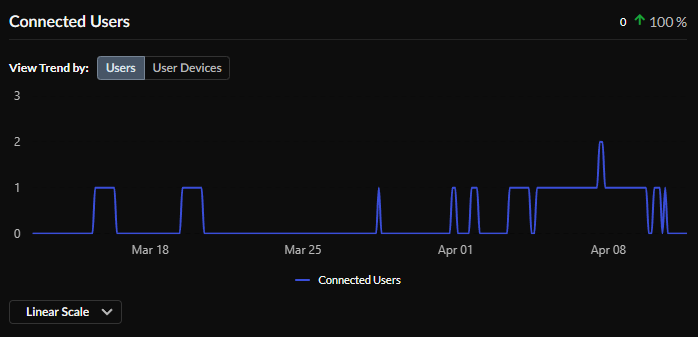
Connected Users
View Connected Users to view current connected users or connected user devices. The up or down arrow compares this time range with a previous time range to determine the difference, in percentage, in number of connected users or devices.
Select View Trend by Users to view the number of users currently connected to Prisma Access Agent, and click View Trend by User Devices to see the number of user devices currently connected to Prisma Access Agent.
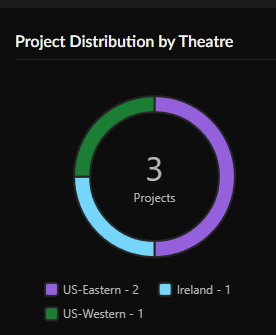
View Project Distribution by Theatre to see the number of projects by location, or theater.
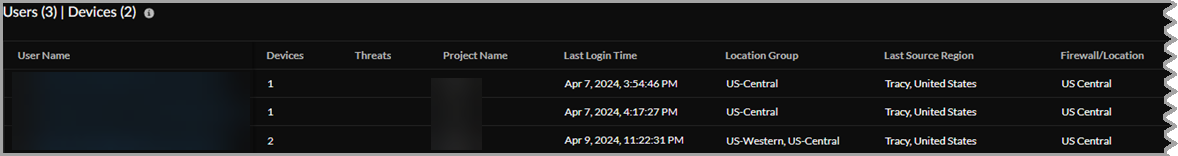
The Users | Devices table shows the Project Name associated with each user and device. You can also see how many devices are connected by user, last login time, last source location, last connected Prisma Access location, the source Internet Protocol, and OS family and version.
Select any Project Name to go to the Projects page.
Select any User Name to view user details such as Activity and Connectivity .
Activity
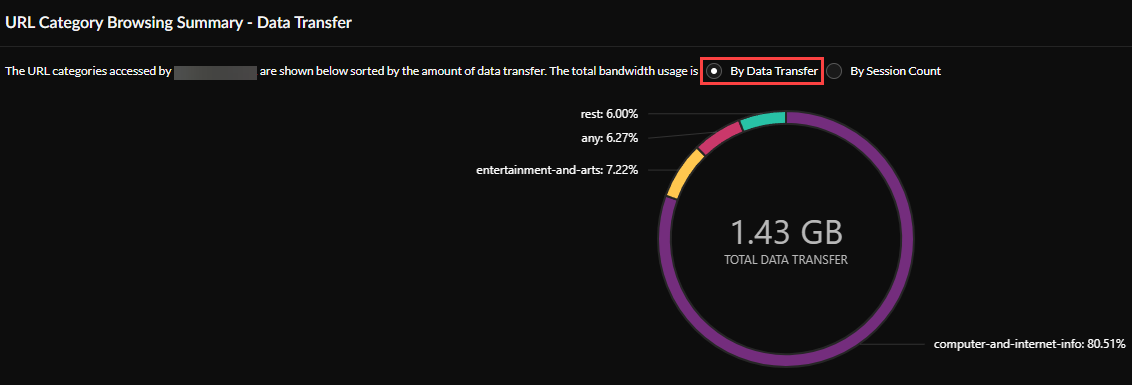
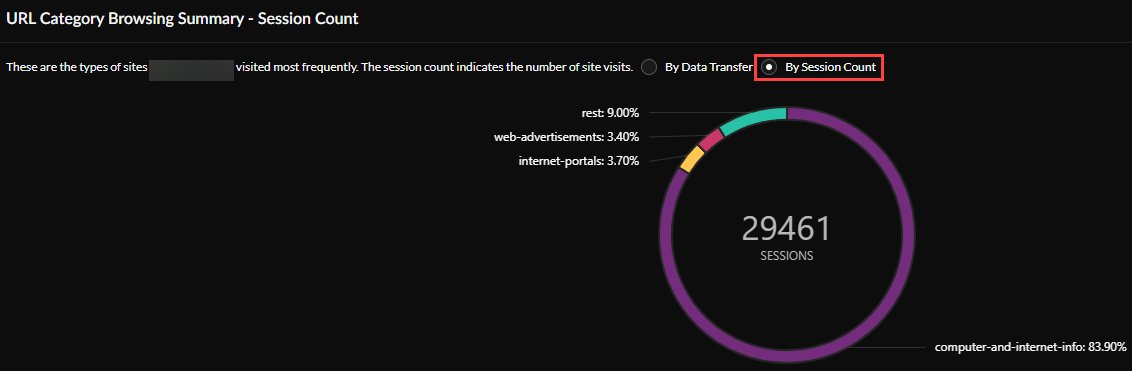
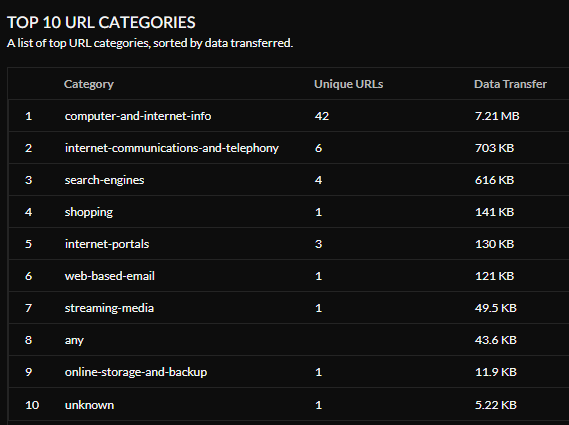
URL Browsing Category Summary- Data Transfer —View your browsing category data transfer summary By Data Transfer or By Session Count . You can also view a list of the Top 10 URL Categories , sorted by data transferred.
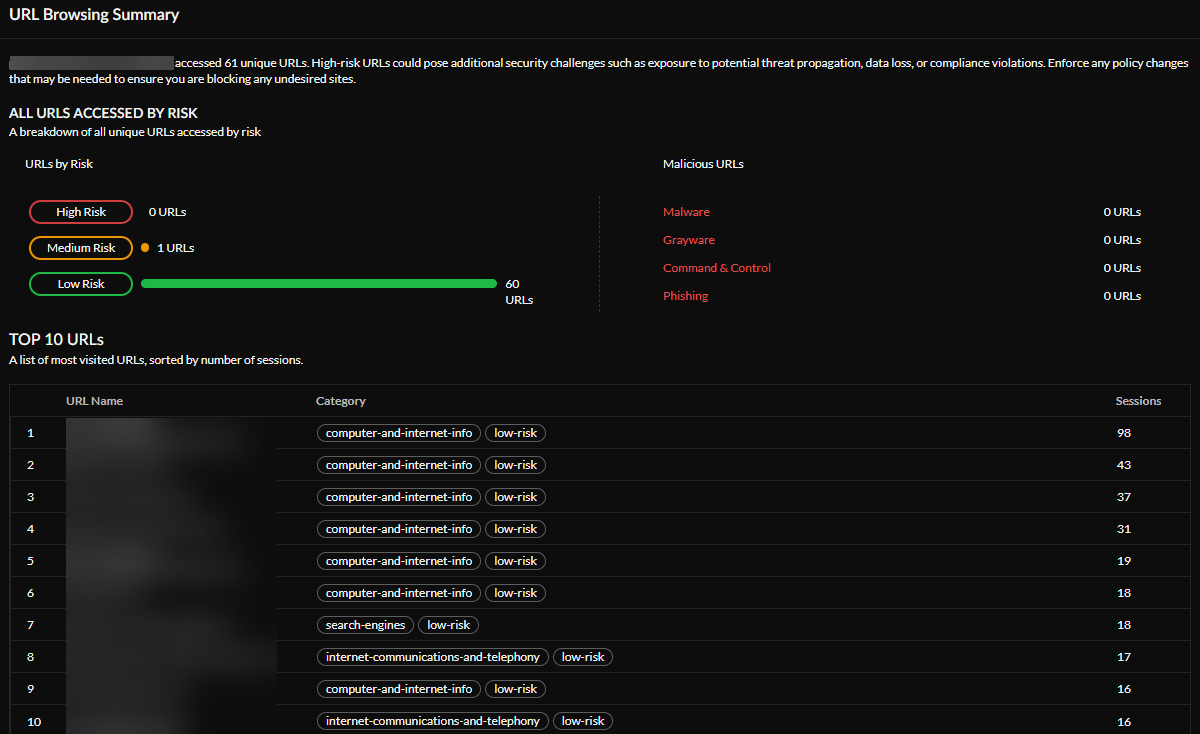
URL Browsing Summary —See your URL browsing summary, including all URLs that you accessed by risk. You can view a breakdown of URLs by risk (High, Medium, or Low) and see how many malicious URLs you accessed. You can also view a list of the Top 10 URLs visited, and how many times you visited each URL.
View URL Filtering Logs —Select View URL Filtering Logs to view details about total data transferred. The logs provide an audit trail for system, configuration, and network events. Network logs record all events where Prisma Access acts on your network.
- View all log data, or use the drop-down to filter by Firewall/URL , Common , or Endpoint . Each of these filters has several subfilters to choose from, as well.
- Enter a log query. Click in this field to view a selection of queries to start with, and build your query.
- Select a time range. The default is past 60 minutes.
- Select Log Settings to view the Strata Logging Service dashboard. Strata Logging Service manages the delivery mechanism for logs.
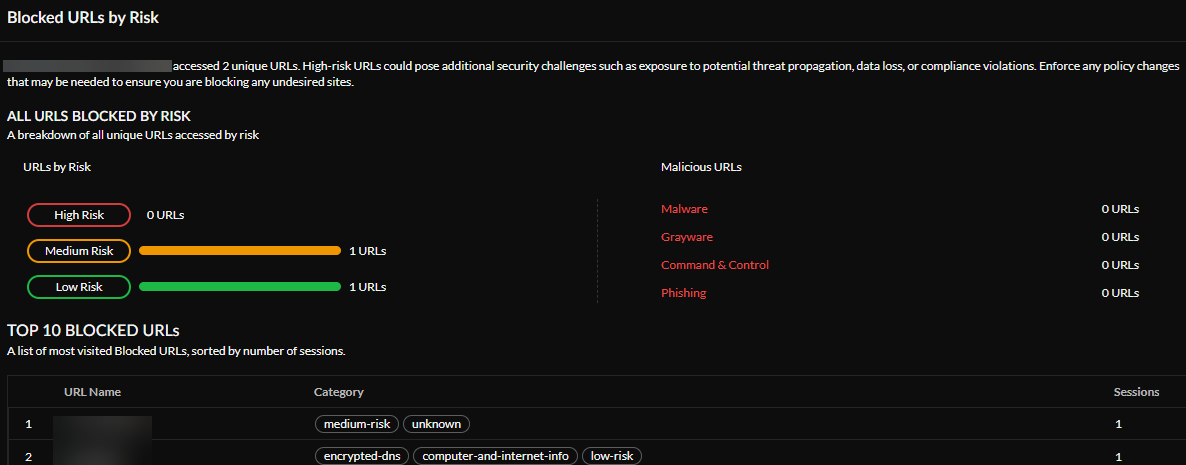
Blocked URLs by Risk —See whether you have accessed, or tried to access, any URLs blocked by risk. High-risk URLs might create additional security challenges, such as exposure to potential threat propagation, data loss, or compliance violations. Enforce any policy changes necessary to block any undesired sites. You can also see a list of the Top 10 Blocked URLs that you visited most, sorted by the number of sessions.
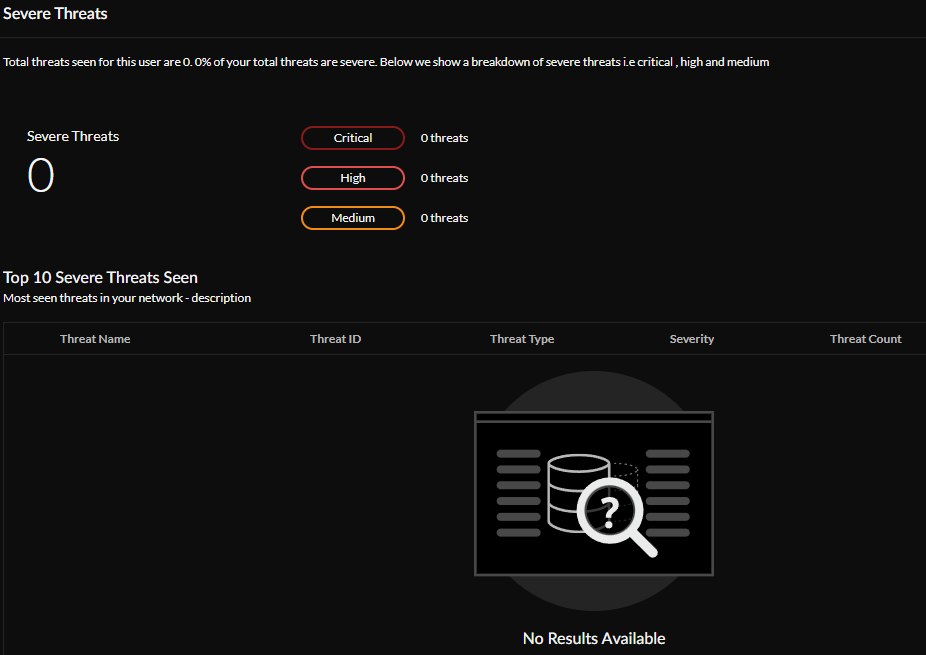
Severe Threats —See how many of your threats are severe. Severe threats are further broken down into Critical, High, and Medium threats. You can also view a list of the Top 10 Severe Threats Seen in your environment.
Connectivity
Select any User name to view information about the user's Connectivity during the Time Range selected.
Active Projects —You can see which projects were active during the time range you selected, and the date that each project became active.
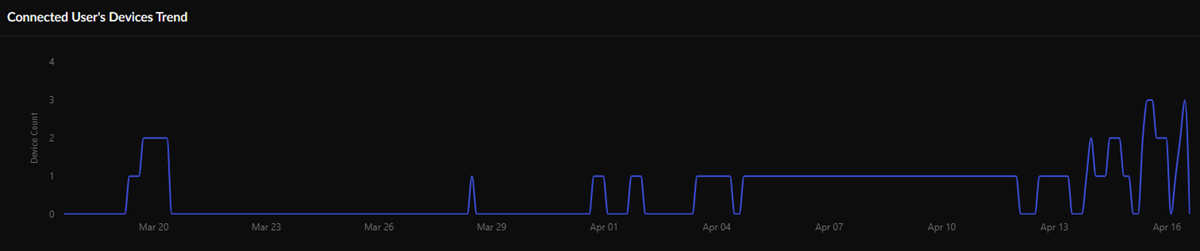
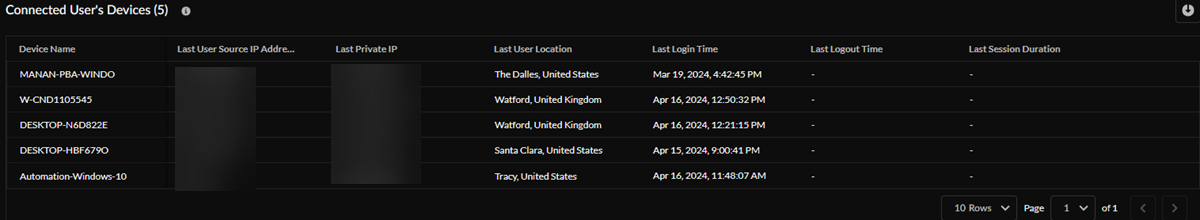
Connected User's Devices Trend and Connected User's Devices —On the main Users page, you could see all connected users and their projects. On the Connectivity page, view your individual Connected User's Devices trend during the time range selected and details about your Connected User's Devices , such as device name, last user source IP address, last private IP address, last user location, last login time, last logout time, and last session duration.
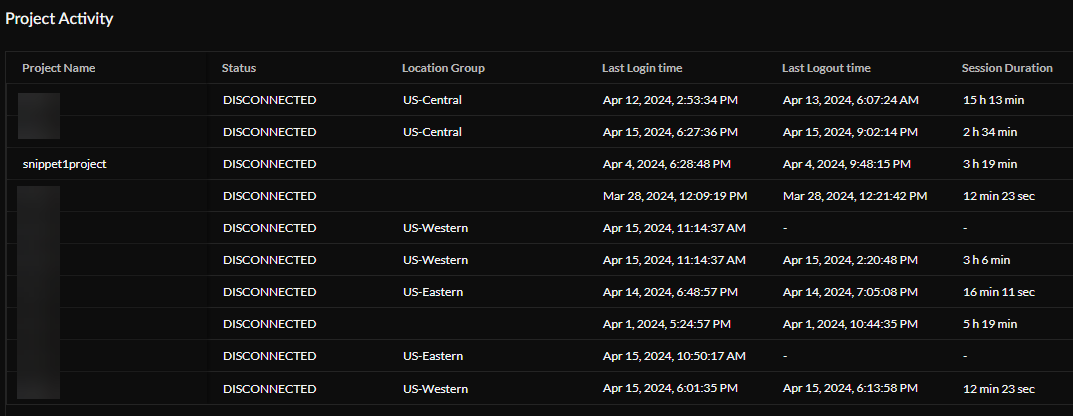
Project Activity —View a user's project activity by session. You can see the current status of a session, when the user logged into each project, when they logged out, and how long each session lasted.
Total User Activity by Project —View the time a user spent on each project during the time range selected.
View and Monitor Dynamic Privilege Access Projects
Gain visibility into your Prisma Access Agent deployment by using Strata Cloud Manager to monitor your users' project activity. Go to Activity InsightsProjects in the Strata Cloud Manager Command Center to view project-based access information in your environment.
Projects
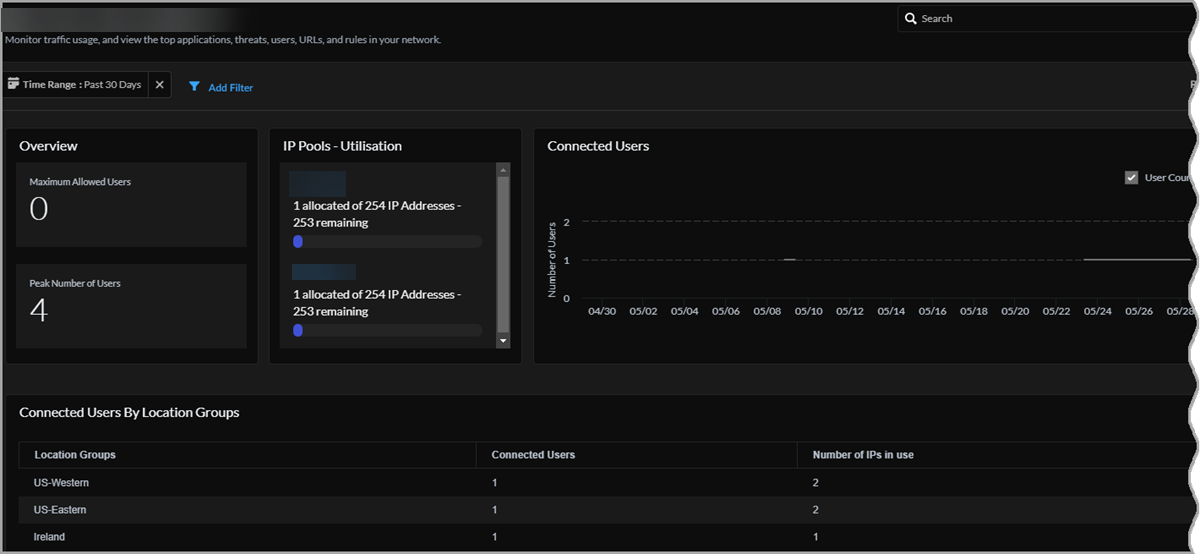
The Projects table provides an overall view about the projects your users access using Prisma Access during the selected time range. You can see each project's number of connected users, peak number of users, maximum allowed users, Prisma Access location groups, IP address pool allocated, the IP pool utilized, number of available IP addresses, and the last connected Prisma Access location.
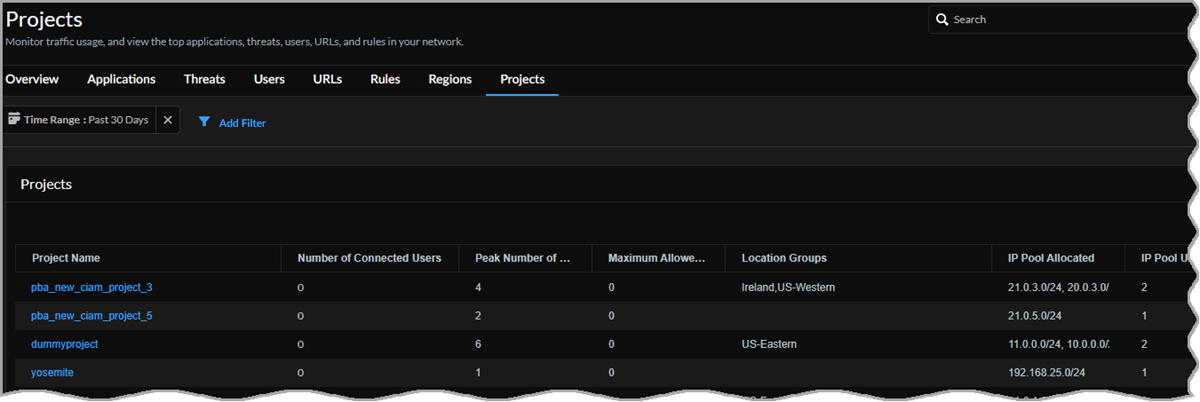
Select a Project Name to go to that project's details page. The project name (blurred in the following image) appears in the upper left corner of the page.
Overview
On the project details page, Overview shows the maximum allowed users for this project and the peak number of users during the selected time range.
IP Pools - Utilization
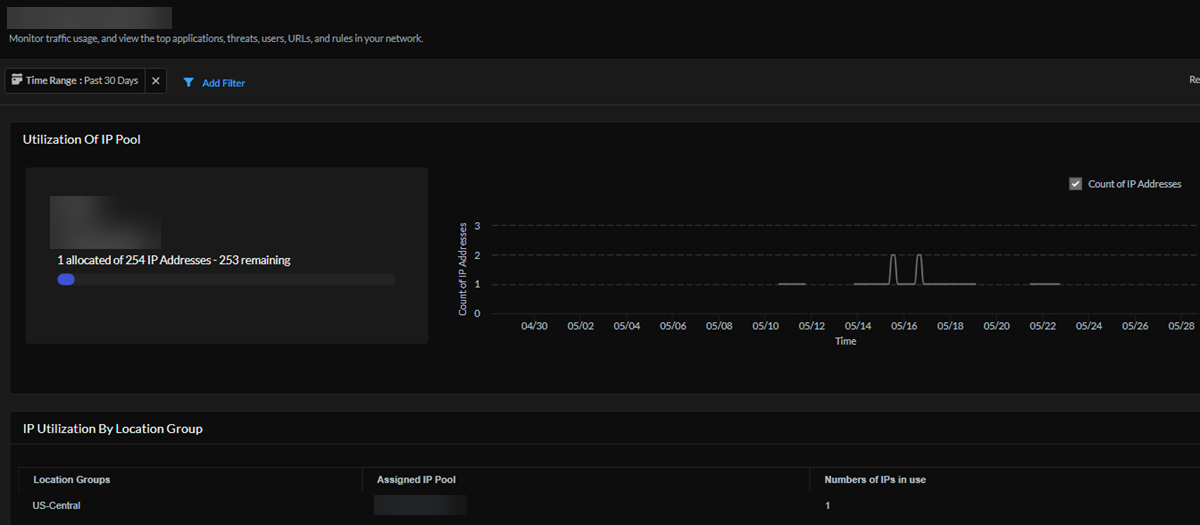
View the number of IPs in use and the number of IPs that are still available for the pools in this project. Select a specific IP pool to go to its details page (see the following image), where you can see this IP pool's utilization, the number of IP addresses used, and IP address utilization by Prisma Access location group.
Connected Users
View a graph of the users connected during the selected time range. Hover over any point in the graph to see the user count at that point.
Connected Users by Location Groups
View the number of users by the Prisma Access Location Group they're in. You can also see the number of IP addresses in use for each Location Group .
Automatic Tunnel Restoration in Dynamic Privilege Access Prisma Access Agents
Automatic tunnel restoration enhances the end-user experience by maintaining consistent and efficient connectivity for Prisma Access Agents. This feature automatically restores secure connections after interruptions, reducing user frustration and minimizing work disruptions.
Automatic tunnel restoration is a standard feature of Prisma Access Agents so no configuration is required for it to work. To understand automatic tunnel restoration, you should be familiar with the following key concepts:
Connectivity Modes
Depending on how you configured the Prisma Access Agent, your users will connect to a gateway using one of the following modes:
- Always On —In this mode, the Prisma Access Agent continuously attempts to maintain a connection to a location. Users can't disconnect, and the sign-out option is disabled in the Prisma Access Agent app.
- On-Demand —This mode allows users to choose when to connect or disconnect. When users choose the Best Location , the agent behaves like it's in Always On mode until manually disconnected.
Location Selection
Your users can connection to a location using (gateway) the following methods:
- Best location selection —This method selects the optimal location based on various factors. It's used when no specific location is chosen or when reconnection to a chosen location fails in Always On mode.
- Manual location selection —Users can choose a specific location to connect to. The behavior differs based on the connectivity mode.
Monitoring and System Changes
Prisma Access Agent monitors various network and system changes, including:
- Network status changes such as internet connectivity coming up or going down
- System sleep mode and resume events
- Service disable or enable events
- Service restarts due to reboots, upgrades, or crashes
Restoration Window
The Prisma Access Agent will attempt to restore the connection for up to 30 minutes after an interruption occurs. This time frame will help to significantly reduce manual reconnections due to changes in network conditions.
- When a connection interruption occurs, the Prisma Access Agent initiates the secure tunnel restoration process.
- The agent attempts to restore the connection for up to 30 minutes.
- If successful within this time frame, the connection is reestablished without user intervention.
- If unsuccessful after 30 minutes, the user might need to manually reinitiate the connection.
Tunnel restoration behavior differs depending on the connectivity mode for the agent.
Tunnel Restoration in Always On Mode
In Always On mode, the Prisma Access Agent actively attempts to maintain a constant connection:
- If the user manually chooses a location and it becomes unavailable, Prisma Access Agent will try to reconnect to the chosen location.
- If reconnection to the chosen location fails, Prisma Access Agent automatically switches to the best location.
- The agent continuously attempts to restore the connection, trying up to five times using the best location.
- The system will notify users about connection status changes in the Prisma Access Agent app.
Tunnel Restoration in On-Demand Mode
In On-Demand mode, the restoration behavior depends on how the connection was initiated:
- If the user chose Best Location , the agent behaves similarly to Always On mode until manually disconnected.
- If the user chose a specific location:
- Prisma Access Agent attempts to reconnect only to that location.
- If reconnection fails, it does not connect to any other location.
- Users are notified of failed connection attempts.
- After a manual disconnect, the Prisma Access Agent remains in a disconnected state until the user initiates a new connection.
In both modes, Prisma Access Agent monitors network and system changes to trigger restoration attempts when necessary, ensuring optimal connectivity within the 30-minute restoration window.